
Randomness Quiz - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Challenge Question - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Totient - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

Introduction - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Auditing Tradeoffs - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Jonathan Katz - Introduction to Cryptography Part 2 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography II" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This session will focus on public-key cryptography, including key exchange, public-key encryption,
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Totient Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Steven Galbraith, Isogeny graphs, computational problems, and applications to cryptography
VaNTAGe Seminar, September 20, 2022 License: CC-BY-NC-SA Some of the papers mentioned in this talk: Ducas, Pierrot 2019: https://link.springer.com/article/10.1007/s10623-018- 0573-3 (https://rdcu.be/cVYrC) Kohel 1996: http://iml.univ-mrs.fr/~kohel/pub/thesis.pdf Fouquet, Morain 2002: ht
From playlist New developments in isogeny-based cryptography

Few other Cryptanalytic Techniques
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Stanford Seminar - The Evolution of Public Key Cryptography
EE380: Computer Systems Colloquium Seminar The Evolution of Public Key Cryptography Speaker: Martin Hellman, Stanford EE (Emeritus) While public key cryptography is seen as revolutionary, after this talk you might wonder why it took Whit Diffie, Ralph Merkle and Hellman so long to discov
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

Stanford Seminar - Cryptology and Security: the view from 2016 - Whitfield Diffie
"Cryptology and Security: the view from 2016" - Whitfield Diffie, ACM 2015 Turing Award About the talk: On the face of it, the cryptographers have solved their piece of the puzzle but every other aspect of security, from crypto-implementations to operating systems to applications, stinks.
From playlist Engineering

Donald Knuth: All Questions Answered - Heroes Lecture Stanford Engineering
Professor Knuth was the guest of honor at this special event on the evening of May 12. Knuth briefly discussed his work and then opened the room queries from the audience. In his typical self-deprecating style, the Professor warns: "the audience should be aware that the answers will be my
From playlist Stanford Engineering Heroes

An Uncrackable Code? (Quantum Cryptography) - A Quantum Scientist Explains #QuantumMinutes
Note: at 8:55 it be should ½ x ½ = ¼ of course, not + What is Quantum Cryptography? Today's host, Dr. Lukas Knips, is a quantum researcher in the group of Prof. Harald Weinfurter at the Ludwig-Maximilians-Universität (LMU) München in Germany. His research focusses on free-space Quantum Ke
From playlist Summer of Math Exposition Youtube Videos

Cryptography: Codes, Ciphers, and Connections
The encryption of information is as old as information itself. Ever since two people wanted to pass something along, so has there been a third party who wanted to be privy to it. This back and forth battle of creating codes, breaking them, and finding new ones has been happening quietly fo
From playlist Mathematics

Stanford Lecture: Donald Knuth - All Questions Answered (May 12, 2011)
May 12, 2011 Donald Knuth, in this Stanford Engineering Hero Lecture, answers questions from the audience--from his opinion of Wikipedia to the next great discovery in computer science to his most memorable mistake. Learn more: http://scpd.stanford.edu/knuth/
From playlist Donald Knuth Lectures
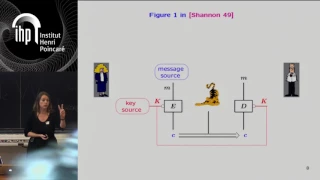
Shannon 100 - 26/10/2016 - Anne CANTEAUT
Comment concevoir un algorithme de chiffrement sûr et efficace : l'héritage de Shannon Anne Canteaut (INRIA) Dans son article fondateur publié en 1949 posant les fondements de la cryptographie, Claude Shannon a énoncé deux méthodes de conception visant à éviter les attaques statistiques
From playlist Shannon 100

CTNT 2022 - An Introduction to Galois Representations (Lecture 3) - by Alvaro Lozano-Robledo
This video is part of a mini-course on "An Introduction to Galois Representations" that was taught during CTNT 2022, the Connecticut Summer School and Conference in Number Theory. More about CTNT: https://ctnt-summer.math.uconn.edu/
From playlist CTNT 2022 - An Introduction to Galois Representations (by Alvaro Lozano-Robledo)

This video gives a general introduction to cryptography WITHOUT actually doing any math. Terms covered include cryptology vs cryptography vs cryptanalysis, symmetric vs public key systems, and "coding theory." NOTE: Yes, I said and wrote "cryptOanalysis" when it's actually "cryptanalysis
From playlist Cryptography and Coding Theory

How cryptography and Web3 can fight misinformation and help restore trust in digital media
Subscribe to Stanford Engineering's The Future of Everything podcast: https://the-future-of-everything-stanford-engineering.simplecast.com/ A group of researchers explore how the tools of cryptography can be used to verify the veracity of the images and videos you see online. Many of the
From playlist The Future of Everything