
C23 More about the annihilator approach
Finding the annihilator differential operator for other types of expressions.
From playlist Differential Equations

C34 Expanding this method to higher order linear differential equations
I this video I expand the method of the variation of parameters to higher-order (higher than two), linear ODE's.
From playlist Differential Equations

Another, perhaps better, method of solving for a higher-order, linear, nonhomogeneous differential equation with constant coefficients. In essence, some form of differentiation is performed on both sides of the equation, annihilating the right-hand side (to zero), so as to change it into
From playlist Differential Equations

Determine if the Functions are Linearly Independent or Linearly Dependent
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys How to determine if three functions are linearly independent or linearly dependent using the definition.
From playlist Differential Equations

C07 Homogeneous linear differential equations with constant coefficients
An explanation of the method that will be used to solve for higher-order, linear, homogeneous ODE's with constant coefficients. Using the auxiliary equation and its roots.
From playlist Differential Equations

C13 Third and higher order linear DE with constant coefficients
An example problem of a third-order, homogeneous, linear ODE with constant coefficients by making use of the roots of the auxiliary equation.
From playlist Differential Equations

A01 Introduction to linear systems
An introduction to linear sets of ordinary differential equations.
From playlist A Second Course in Differential Equations

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Linear versus Nonlinear Differential Equations
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys Linear versus Nonlinear Differential Equations
From playlist Differential Equations

Lilya Budaghyan : On APN and AB power functions
CONFERENCE Recording during the thematic meeting : « ALgebraic and combinatorial methods for COding and CRYPTography» the February 23, 2023 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker: Guillaume Hennenfent Find this video and other talks given b
From playlist Combinatorics

Louis Nirenberg: Some remarks on Mathematics
Abel Laureate Louis Nirenberg, Courant Institute, New York University: Some remarks on Mathematics This lecture was held by Abel Laurate Louis Nirenberg at The University of Oslo, May 20, 2015 and was part of the Abel Prize Lectures in connection with the Abel Prize Week celebrations. P
From playlist Louis Nirenberg

Mod-01 Lec-01 Introduction and Overview
Advanced Numerical Analysis by Prof. Sachin C. Patwardhan,Department of Chemical Engineering,IIT Bombay.For more details on NPTEL visit http://nptel.ac.in
From playlist IIT Bombay: Advanced Numerical Analysis | CosmoLearning.org

Introduction to Differential Equation Terminology
This video defines a differential equation and then classifies differential equations by type, order, and linearity. Search Library at http://mathispower4u.wordpress.com
From playlist Introduction to Differential Equations
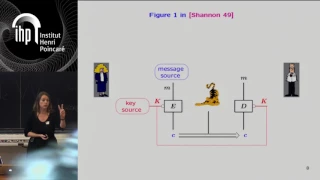
Shannon 100 - 26/10/2016 - Anne CANTEAUT
Comment concevoir un algorithme de chiffrement sûr et efficace : l'héritage de Shannon Anne Canteaut (INRIA) Dans son article fondateur publié en 1949 posant les fondements de la cryptographie, Claude Shannon a énoncé deux méthodes de conception visant à éviter les attaques statistiques
From playlist Shannon 100
Transfer Functions: Introduction and Implementation
In this video we introduce transfer functions and show how they can be derived from a set of linear, ordinary differential equations. We also examine how to use a transfer function to predict the output of system to a given input. Topics and time stamps: 0:38 – Example using an aircraft
From playlist Control Theory

Valentin Suder - Sparse Permutations with Low Differential Uniformity
Sparse Permutations with Low Differential Uniformity
From playlist Journées Codage et Cryptographie 2014

Gaël Thomas - Diffusion dans les schémas de Feistel généralisés
Diffusion dans les schémas de Feistel généralisés
From playlist Journées Codage et Cryptographie 2014

Instance-Hiding Schemes for Private Distributed Learning -Sanjeev Arora
Seminar on Theoretical Machine Learning Topic: Instance-Hiding Schemes for Private Distributed Learning Speaker: Sanjeev Arora Affiliation: Princeton University; Distinguishing Visiting Professor, School of Mathematics Date: June 25, 2020 For more video please visit http://video.ias.edu
From playlist Mathematics

CERIAS Security: Perturbation of Multivariable Public-key Cryptosystems 4/5
Clip 4/5 Speaker: Jintai Ding · University of Cincinnati Public key cryptography is an indispensable part of most modern communication systems. However, quantum computers can break cryptosystems like RSA, which are based on For more information go to the Cerias website (http://bit
From playlist The CERIAS Security Seminars 2005 (2)

B27 Introduction to linear models
Now that we finally now some techniques to solve simple differential equations, let's apply them to some real-world problems.
From playlist Differential Equations