Introducing the Concept of Congruence
From playlist GeoGebra Geometry

Constructing the Wallace-Simson Line
From playlist GeoGebra Geometry

Dynamic Offset Rasa Developer Summit 2019
Josh Converse, Software Consultant at Dynamic Offset, shares how Rasa works in harmony with other technologies. It has been said of the Beatles that the whole (the band) is greater than the sum of the parts (the band members). The same can hold true for open source software. This talk ex
From playlist Rasa Developer Summit 2019

GeoGebra Link: https://www.geogebra.org/m/ketkkfuj
From playlist Geometry: Challenge Problems

Joao Pequenao - Collide@CERN inspiration partner
Joao Pequenao is working with Gilles Jobin, the first winner of collide@CERN Geneva Award for Dance and Performance. To know more: https://arts.web.cern.ch/collide/dance-performance-residency
From playlist Arts@CERN

Mythical Mountains: Crash Course World Mythology #33
Our mythical places series continues, and this week Mike Rugnetta is talking about some stories that revolve around mountains. Mountains loom large in human stories, not least because mountains are, well, large. So ascend with us to the lofty peaks of The Ten Thousand Treasure Mountain in
From playlist World Mythology

Constructing a REGULAR POLYGON: GeoGebra Beginner Exercise 1
Screencast displays how to use the REGULAR POLYGON tool to construct various regular polygons in GeoGebra. Try it yourself here: https://www.geogebra.org/m/NUtDnGgC#material/ez3tzHra
From playlist GeoGebra Geometry & Graphing Calculator: BEGINNER Tutorial Series
GeoGebra Link: https://www.geogebra.org/m/f5zgupmz
From playlist Geometry: Challenge Problems

Cumulative Frequency Curves - GCSE Maths Exam Questions
GCSE Maths Cumulative Frequency Curves maths exam question practice taken from past papers and practice papers. Keywords: Cumulative frequency curves, median, interquartile range, quartile, graph Help revise for the 8300 new specification 9-1 mathematics exams and your mock. Deep dive
From playlist GCSE Maths Exam Question Compilations

Follow-up: Barbie electronic typewriter
Here is a copy of the description from the Barbie video: ---- I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett fr
From playlist My Maths Videos

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Live CEOing Ep 544: Language Design in Wolfram Language [Ciphers & WFR Submissions] [Part 01]
In this episode of Live CEOing, Stephen Wolfram discusses upcoming improvements and features to the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Stephen Wolfram
From playlist Behind the Scenes in Real-Life Software Design

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography
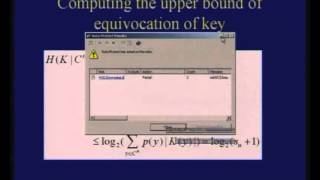
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
A very quick demo of how to access the 2D and 3D calculator on Geogebra.
From playlist Geogebra

What is Bill Cipher? (Scientific Analysis)
What is Bill Cipher? Today we discover the very very confusing science of what Gravity Fall's Bill Cipher is. =======WARNING VERY VERY CONFUSING======= This video talks about dimensions and alternate universes. Your mind might explode! Sources: -http://en.wikipedia.org/wiki/Four-dim...
From playlist Scientific Videos