
The method of determining eigenvalues as part of calculating the sets of solutions to a linear system of ordinary first-order differential equations.
From playlist A Second Course in Differential Equations

Changing notation with complex eigenvalues.
From playlist A Second Course in Differential Equations

A11 Eigenvalues with complex numbers
Eigenvalues which contain complex numbers.
From playlist A Second Course in Differential Equations

Linear Algebra: Ch 3 - Eigenvalues and Eigenvectors (5 of 35) What is an Eigenvector?
Visit http://ilectureonline.com for more math and science lectures! In this video I will explain and show (in general) what is and how to find an eigenvector. Next video in this series can be seen at: https://youtu.be/SGJHiuRb4_s
From playlist LINEAR ALGEBRA 3: EIGENVALUES AND EIGENVECTORS

With the eigenvalues for the system known, we move on the the eigenvectors that form part of the set of solutions.
From playlist A Second Course in Differential Equations
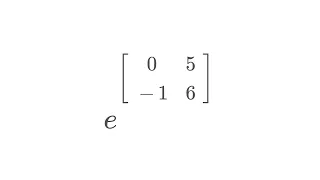
Calculating e^A for a matrix A, explaining what this has to do with diagonalization, and solving systems of differential equations Check out my Eigenvalues playlist: https://www.youtube.com/watch?v=H-NxPABQlxI&list=PLJb1qAQIrmmC72x-amTHgG-H_5S19jOSf Subscribe to my channel: https://www.y
From playlist Eigenvalues
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cylindrical contact homology of links of simple singularities - Leo Digiosia
Joint IAS/Princeton/Montreal/Paris/Tel-Aviv Symplectic Geometry Title: Cylindrical contact homology of links of simple singularities Speaker: Leo Digiosia Affiliation: Rice Date: October 8, 2021 Abstract: In this talk we consider the links of simple singularities, which are contactomop
From playlist Mathematics

Pierre Albin: The sub-Riemannian limit of a contact manifold
Talk by Pierre Albin in the Global Noncommutative Geometry Seminar (Americas) on January 29, 2021. https://globalncgseminar.org/talks/tba-5/?utm_source=mailpoet&utm_medium=email&utm_campaign=global-noncommutative-geometry-seminar-americas-01292021_14
From playlist Global Noncommutative Geometry Seminar (Americas)

10A An Introduction to Eigenvalues and Eigenvectors
A short description of eigenvalues and eigenvectors.
From playlist Linear Algebra

Pablo Portilla | Tête-à-tête graphs and Seifert Manifolds
Worldwide Center of Mathematics Lecture Seminar Series
From playlist Center of Math Research: the Worldwide Lecture Seminar Series

DeepSec 2007: Intercepting GSM traffic
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speaker: Steve This talk is about GSM security. We will explain the security, technology and protocols of a GSM network. We will further present a solution to build a GSM scanner
From playlist DeepSec 2007

DLP Attacks and intro to El Gamal
We cover basic attacks on the discrete logarithm problem. The El Gamal Cipher is presented. We start discussion digital signatures.
From playlist PubKey

Differential Equations | The Matrix Exponential e^{tA}.
We outline a strategy for finding the matrix exponential e^{tA}, including an example when A is 2x2 and not diagonalizable. http://www.michael-penn.net http://www.randolphcollege.edu/mathematics/
From playlist Systems of Differential Equations

Stanford Lecture: "Aha" Sessions - Problem 2 - Code Breaking Part 2
January 22, 1985 Notes from these problem sessions were published as A Programming and Problem-Solving Seminar, Stanford Technical Report No. STAN-CS-85-1055. (http://www-cs-faculty.stanford.edu/~knuth/papers/cs1055.pdf) Professor Knuth is the Professor Emeritus at Stanford University. D
From playlist Donald Knuth Lectures

8ECM Invited Lecture: Burak Özbağcı
From playlist 8ECM Invited Lectures

This video explores the eigenvalues and eigenvectors of a matrix "A". This is one of the most important concepts in linear algebra. The eigenvectors represent a change of coordinates in which the "A" matrix becomes diagonal, with entries given by the eigenvalues. This allows us to easil
From playlist Engineering Math: Differential Equations and Dynamical Systems

Follow-up: Barbie electronic typewriter
Here is a copy of the description from the Barbie video: ---- I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett fr
From playlist My Maths Videos
In this video we discuss the concept of eigenvalues and eigenvectors of a matrix. We show that an eigenvector has the property that when it is operated on by the matrix, the resulting output vector is a scaled version of the input vector (it is scaled by the eigenvalue). We discuss how t
From playlist Linear Algebra
Robert Lipshitz - Computing involutive HF-hat
June 20, 2018 - This talk was part of the 2018 RTG mini-conference Low-dimensional topology and its interactions with symplectic geometry Hendricks-Manolescu's "involutive Heegaard Floer homology" is a variant of Heegaard Floer homology which capitalizes on the conjugation action on spin^
From playlist 2018 RTG mini-conference on low-dimensional topology and its interactions with symplectic geometry I