
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Numerically Calculating Partial Derivatives
In this video we discuss how to calculate partial derivatives of a function using numerical techniques. In other words, these partials are calculated without needing an analytical representation of the function. This is useful in situations where the function in question is either too co
From playlist Vector Differential Calculus

How to solve differentiable equations with logarithms
Learn how to solve the particular solution of differential equations. A differential equation is an equation that relates a function with its derivatives. The solution to a differential equation involves two parts: the general solution and the particular solution. The general solution give
From playlist Differential Equations

Convolution Theorem: Fourier Transforms
Free ebook https://bookboon.com/en/partial-differential-equations-ebook Statement and proof of the convolution theorem for Fourier transforms. Such ideas are very important in the solution of partial differential equations.
From playlist Partial differential equations

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Find the particular solution given the conditions and second derivative
Learn how to solve the particular solution of differential equations. A differential equation is an equation that relates a function with its derivatives. The solution to a differential equation involves two parts: the general solution and the particular solution. The general solution give
From playlist Solve Differential Equation (Particular Solution) #Integration
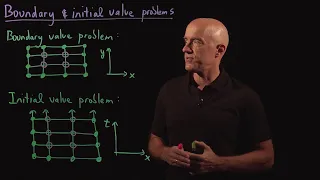
Boundary and Initial Value Problems | Lecture 60 | Numerical Methods for Engineers
Classification of partial differential equations into boundary value problems and initial value problems. Join me on Coursera: https://www.coursera.org/learn/numerical-methods-engineers Lecture notes at http://www.math.ust.hk/~machas/numerical-methods-for-engineers.pdf Subscribe to my c
From playlist Numerical Methods for Engineers

How to solve a differentialble equation by separating the variables
Learn how to solve the particular solution of differential equations. A differential equation is an equation that relates a function with its derivatives. The solution to a differential equation involves two parts: the general solution and the particular solution. The general solution give
From playlist Solve Differential Equation (Particular Solution) #Integration

Partial Derivatives and the Gradient of a Function
We've introduced the differential operator before, during a few of our calculus lessons. But now we will be using this operator more and more over the prime symbol we are used to when describing differentiation, as from now on we will frequently be differentiating with respect to a specifi
From playlist Mathematics (All Of It)

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

CERIAS Security: Recent Attacks on MD5 4/6
Clip 4/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

Block Ciphers and Data Encryption Standard (DES): Part 2
Fundamental concepts of Block Cipher Design Principles are discussed. Differential cryptanalysis and linear cryptanalysis are explained.
From playlist Network Security

Cryptanalysis of Vigenere cipher: not just how, but why it works
The Vigenere cipher, dating from the 1500's, was still used during the US civil war. We introduce the cipher and explain a standard method of cryptanalysis based on frequency analysis and the geometry of vectors. We focus on visual intuition to explain why it works. The only background
From playlist Classical Cryptography

RailsConf 2018: Encrypted Credentials on Rails 5.2: Secrets to Success by Christopher Rigor
RailsConf 2018: Encrypted Credentials on Rails 5.2: Secrets to Success by Christopher Rigor Secrets are out. Credentials are in. This new Rails 5.2 feature offers a number of advantages over the old way of managing secrets. You get atomic deploys, you avoid putting sensitive data on envir
From playlist RailsConf 2018

CERIAS Security: Recent Attacks on MD5 6/6
Clip 6/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

CERIAS Security: Recent Attacks on MD5 5/6
Clip 5/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

Modular Exponentiation Quiz - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Overview on Modern Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security