
This video gives a general introduction to cryptography WITHOUT actually doing any math. Terms covered include cryptology vs cryptography vs cryptanalysis, symmetric vs public key systems, and "coding theory." NOTE: Yes, I said and wrote "cryptOanalysis" when it's actually "cryptanalysis
From playlist Cryptography and Coding Theory

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

Introduction - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Steganography Tutorial - Hide Messages In Images
Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step further by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it
From playlist Ethical Hacking & Penetration Testing - Complete Course

Why Beautiful Things Make us Happy – Beauty Explained
It’s hard to define what makes something beautiful, but we seem to know beauty when we see it. Why is that and how does beauty affect our subconscious? This video was a collaboration with the creative agency Sagmeister & Walsh as a contribution to their upcoming Beauty exhibition at the M
From playlist Human Stuff

Hamiltonian Cycles, Graphs, and Paths | Hamilton Cycles, Graph Theory
What are Hamiltonian cycles, graphs, and paths? Also sometimes called Hamilton cycles, Hamilton graphs, and Hamilton paths, we’ll be going over all of these topics in today’s video graph theory lesson! A Hamilton cycle in a graph G is a cycle containing all vertices of G. A Hamilton path
From playlist Graph Theory

RTD Interview: 'Cryptocurrency Makes It Easier To Buy Gold' w/ Andreas Antonopoulos
Thanks for watching this RTD Interview. Share your thoughts in the comment section below. Subscribe & click the 🔔 icon to be notified of the next video. Take action into your own hands and get physical with your wealth. Get the RTD round and help support the channel. ***RTD 'Scary Georg
From playlist Interviews and Shows

Hae Kyung Im: "Prediction and Dissection of Complex Traits"
Computational Genomics Winter Institute 2018 "Prediction and Dissection of Complex Traits" Hae Kyung Im, University of Chicago Institute for Pure and Applied Mathematics, UCLA March 1, 2018 For more information: http://computationalgenomics.bioinformatics.ucla.edu/programs/2018-cgwi/
From playlist Computational Genomics Winter Institute 2018

Week of Reflection - Still Untitled: The Adam Savage Project - 9/3/19
After a particularly intense week, we regroup to talk about the ways in which we chilled and reset ourselves over the long labor day weekend. Norm recaps his trip to Galaxy's Edge, Will read The Fall, and Adam shared his favorite cosplay he saw posted from Dragon*Con. Plus, an appreciation
From playlist The Adam Savage Project
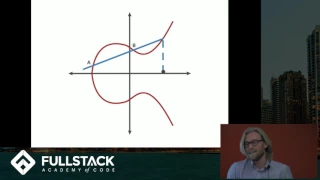
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Learn more advanced front-end and full-stack development at: https://www.fullstackacademy.com Elliptic Curve Cryptography (ECC) is a type of public key cryptography that relies on the math of both elliptic curves as well as number theory. This technique can be used to create smaller, fast
From playlist Elliptic Curves - Number Theory and Applications

OWASP Top 10 Mobile Risks: 2014 Reboot - Jack Mannino & Jason Haddix
The OWASP Top 10 Mobile Risks were first created in 2011. However, a lot has changed over the past three years. The mobile platforms themselves have evolved, mobile threats have evolved, and app developers have experimented with crazy new things. As a result, the OWASP Mobile Security Proj
From playlist AppSec California 2014

Astronomy Cast Ep. 270: Inertia
From playlist Astronomy Cast

What Is the Future of Cryptography?
Historically, as advances were made in the fields of engineering, mathematics, and physics, so the field of cryptography has advanced with them—usually by leaps and bounds. Where is it headed next? Science journalist Simon Singh concedes that the science of secrecy tends to be secret, so w
From playlist Technology

Spoiling My Child Rotten (Child Health Documentary) | Real Stories
From obesity to alcohol misuse, from rotting baby teeth to hearing problems caused by passive smoking – Britain’s largest children’s hospital is treating younger and younger patients for health problems which are ultimately preventable. Many are the result of kids’ lifestyles and are, acco
From playlist Medical Stories


