
Use Prime Factorization to Simplify the Square Root of a Number, sqrt(32)
👉 Learn how to find the square root of a number. To find the square root of a number, we identify whether that number which we want to find its square root is a perfect square. This is done by identifying a number which when raised to the 2nd power gives the number which we want to find it
From playlist How to Simplify the Square Root of a Number
Explain how to take the root of a number even or odd using prime factorization, root
👉 Learn how to find the square root of a number. To find the square root of a number, we identify whether that number which we want to find its square root is a perfect square. This is done by identifying a number which when raised to the 2nd power gives the number which we want to find it
From playlist How to Simplify the Square Root of a Number

Simplifying the Square Root of a Number Using a Factor Tree, Sqrt(80)
👉 Learn how to find the square root of a number. To find the square root of a number, we identify whether that number which we want to find its square root is a perfect square. This is done by identifying a number which when raised to the 2nd power gives the number which we want to find it
From playlist How to Simplify the Square Root of a Number

How to take the square root of three different types of numbers, root(4), root(18)
👉 Learn how to find the square root of a number. To find the square root of a number, we identify whether that number which we want to find its square root is a perfect square. This is done by identifying a number which when raised to the 2nd power gives the number which we want to find it
From playlist How to Simplify the Square Root of a Number

Breaking down the square root of forty, sqrt(40)
👉 Learn how to find the square root of a number. To find the square root of a number, we identify whether that number which we want to find its square root is a perfect square. This is done by identifying a number which when raised to the 2nd power gives the number which we want to find it
From playlist How to Simplify the Square Root of a Number
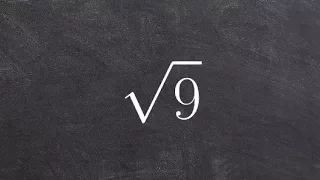
How To Take the Square Root of a Number Using the Identify Element
👉 Learn how to find the square root of a number. To find the square root of a number, we identify whether that number which we want to find its square root is a perfect square. This is done by identifying a number which when raised to the 2nd power gives the number which we want to find it
From playlist How to Simplify the Square Root of a Number

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

How to take the square root of a number using prime factorization, sqrt(64)
👉 Learn how to find the square root of a number. To find the square root of a number, we identify whether that number which we want to find its square root is a perfect square. This is done by identifying a number which when raised to the 2nd power gives the number which we want to find it
From playlist How to Simplify the Square Root of a Number

ADFGVX Cipher: Encryption and Decryption (Updated)
Encryption and Decryption of the World War One ADFGVX Cipher, through examples. This video replaces an earlier one with the same content, but has some improvements and corrections. #cryptography
From playlist Classical Cryptography
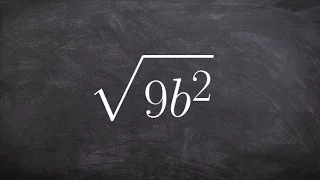
Using prime factorization to simplify the square root of an expression
👉 Learn how to simplify the square root of an expression. The square root of an expression is an expression which will multiply itself twice to give the original expression. To simplify the square root of an expression, we decompose/factor the expression into a product of two terms that ar
From playlist Simplify the Square Root Expressions

Math for Liberal Studies - Lecture 3.6.2 The Bifid Cipher
This is the second video lecture for Math for Liberal Studies Section 3.6: An Introduction to Cryptography. In this lecture, we discuss a new method for encrypting and decrypting messages: the bifid cipher. This method relies on converting the letters in the message to coordinates in a let
From playlist Math for Liberal Studies Lectures
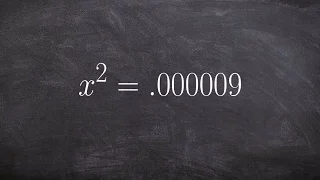
Taking the Square Root of a Decimal
👉 Learn how to find the square root of a number. To find the square root of a number, we identify whether that number which we want to find its square root is a perfect square. This is done by identifying a number which when raised to the 2nd power gives the number which we want to find it
From playlist How to Simplify the Square Root of a Number
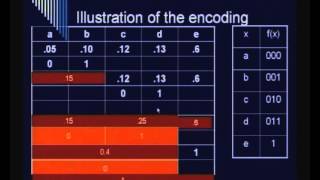
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

ADFGVX Cipher: Encryption and Decryption (OLD VERSION: SEE NEW VERSION LINK BELOW)
This video has been replaced with an updated video: visit https://youtu.be/T0xfKiU9Rr4 Encryption and Decryption of the World War One ADFGVX Cipher, through examples.
From playlist Classical Cryptography
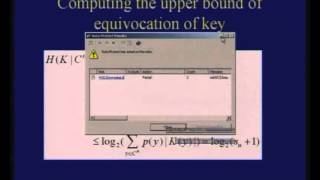
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Follow-up: Barbie electronic typewriter
Here is a copy of the description from the Barbie video: ---- I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett fr
From playlist My Maths Videos

The Trick That Solves Rubik’s Cubes and Breaks Ciphers (Meet in the Middle)
What do the Rubik's cube and a cipher from the 70s have in common? Let's find out. 0:00 Rubik's cube 9:40 DES ------------------------ Links: Feliks setting the 4.73 record https://www.youtube.com/watch?v=R07JiT0PlcE&ab_channel=FeliksZemdegs webpage "God's number is 20" http://www.cub
From playlist Algorithms

caesar - CS50 Walkthroughs 2019
*** This is CS50, Harvard University's introduction to the intellectual enterprises of computer science and the art of programming. *** HOW TO SUBSCRIBE http://www.youtube.com/subscription_center?add_user=cs50tv HOW TO TAKE CS50 edX: https://cs50.edx.org/ Harvard Extension School: ht
From playlist CS50 Walkthroughs 2019

Learn how to simplify square root of a number when it is multiplied by another number
👉 Learn how to find the square root of a number. To find the square root of a number, we identify whether that number which we want to find its square root is a perfect square. This is done by identifying a number which when raised to the 2nd power gives the number which we want to find it
From playlist Simplify the Square Root Expressions

Jessica Sklar - Mathematical Art Inspirations, Instantiations, and Installations - CoM Feb 2022
During 2020, while the world shut down, creativity flourished. Choral groups sang over Zoom, friends attended virtual cocktail hours, and mathematicians and artists spent their lockdown hours knitting, painting, and constructing wonders. In this talk, I’ll show and discuss pieces by QED A
From playlist Celebration of Mind