
Public Key Cryptography & RSA: Part 1
Fundamental concepts of Public Key Encryption are discussed. RSA Public Encryption is presented. Optimization of Private Key operations is analyzed. Public Key Encryption Symmetric vs. Public-Key RSA Public Key Encryption RSA Key Construction Optimizing Private Key Operations RSA Securit
From playlist Network Security

Correctness Of RSA - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Picking E And D Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Network Security, Part 2 : Public Key Encryption
Fundamental concepts of public key encryption are discussed. RSA encryption method explained with an example. Confidentiality of message is presented.
From playlist Cryptography, Security

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Prime Numbers Make the Internet Possible. Here's How - The RSA Encryption Algorithm
In this video I talk about the RSA Encryption Algorithm, and about the history of cryptography. People have been coding and decoding information ever since we learnt how to write. The Romans were one of the first to implement it, making what they considered to be the unbreakable 'Caesar C
From playlist Prime Numbers

Theory and Practice of Cryptography
Google Tech Talks December, 12 2007 ABSTRACT Topics include: Introduction to Modern Cryptography, Using Cryptography in Practice, Proofs of Security and Security Definitions and A Special Topic in Cryptography Speaker: Steve Weis Steve Weis received his PhD from the Cryptography and In
From playlist Cryptography, Security

Stanford Seminar: Building Systems Using Malicious Components
EE380: Colloquium on Computer Systems Building Systems Using Malicious Components: How I learned to Stop Worrying and Trust SNARK Proofs Speaker: Eran Tromer, Tel Aviv University and Columbia University "Computers are unreliable and vulnerable to attacks. Therefore, we shouldn't belie
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

Efficient Zero Knowledge Proofs - A Modular Approach (Lecture 2) by Yuval Ishai
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020
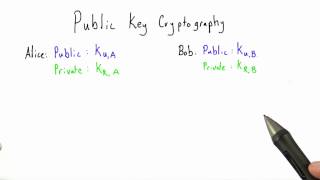
Public Key Cryptography - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Jonathan Katz - Introduction to Cryptography Part 2 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography II" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This session will focus on public-key cryptography, including key exchange, public-key encryption,
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Efficient Zero Knowledge Proofs - A Modular Approach (Lecture 1) by Yuval Ishai
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

PCP and Delegating Computation: A Love Story - Yael Tauman Kalai
Computer Science/Discrete Mathematics Seminar I Topic: PCP and Delegating Computation: A Love Story Speaker: Yael Tauman Kalai Affiliation: Microsoft Research Date: January 28, 2019 For more video please visit http://video.ias.edu
From playlist Mathematics

What is the Public Key Encryption?
A 1976, two Stanford researchers devised an encryption method that revolutionized cryptography by making it easier to send encrypted information without having to agree on a key beforehand. With the help of a short animation, cryptographer Tal Rabin explains how these "public" keys work.
From playlist Technology

Some Cryptographic Tools (in Blockchains) by Manoj Prabhakaran
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

Gambling, Computational Information, and Encryption Security - Bruce Kapron
Gambling, Computational Information, and Encryption Security Bruce Kapron University of Victoria; Member, School of Mathematics March 24, 2014 We revisit the question, originally posed by Yao (1982), of whether encryption security may be characterized using computational information. Yao p
From playlist Members Seminar

Jonathan Katz - Introduction to Cryptography Part 1 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will serve as a "crash course" in modern cryptography for those with no prior exposure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Delegating computation via no-signaling strategies – Yael Kalai – ICM2018
Mathematical Aspects of Computer Science Invited Lecture 14.4 Delegating computation via no-signaling strategies Yael Kalai Abstract: Efficient verification of computation, also known as ‘delegation of computation’, is one of the most fundamental notions in computer science, and in parti
From playlist Mathematical Aspects of Computer Science
