
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Random Oracle Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

How to solve EXACT DIFFERENTIAL EQUATIONS IVPs
► My Differential Equations course: https://www.kristakingmath.com/differential-equations-course Exact differential equations are a kind of homogeneous differential equation that take on a very specific form. In order to find the solution to an exact differential equation, you'll need to
From playlist Differential Equations

Introduction to Differential Equations
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys Introduction to Differential Equations - The types of differential equations, ordinary versus partial. - How to find the order of a differential equation.
From playlist Differential Equations

How to solve differentiable equations with logarithms
Learn how to solve the particular solution of differential equations. A differential equation is an equation that relates a function with its derivatives. The solution to a differential equation involves two parts: the general solution and the particular solution. The general solution give
From playlist Differential Equations

Perfect Cipher Is Impractical - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

This is one of my all-time favorite differential equation videos!!! :D Here I'm actually using the Wronskian to actually find a nontrivial solution to a second-order differential equation. This is amazing because it brings the concept of the Wronskian back to life! And as they say, you won
From playlist Differential equations

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

Ethical Hacking Tutorial For Beginners | Ethical Hacking Course | Ethical Hacking Training | Edureka
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training 🔵 Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN This Edureka "Ethical Hacking Tutorial" video will give you an introduction to Ethical Hacking. This video will give you an exhaustiv
From playlist Cyber Security Training for Beginners | Edureka
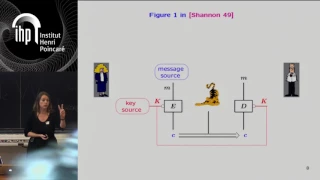
Shannon 100 - 26/10/2016 - Anne CANTEAUT
Comment concevoir un algorithme de chiffrement sûr et efficace : l'héritage de Shannon Anne Canteaut (INRIA) Dans son article fondateur publié en 1949 posant les fondements de la cryptographie, Claude Shannon a énoncé deux méthodes de conception visant à éviter les attaques statistiques
From playlist Shannon 100

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

How to solve a differentialble equation by separating the variables
Learn how to solve the particular solution of differential equations. A differential equation is an equation that relates a function with its derivatives. The solution to a differential equation involves two parts: the general solution and the particular solution. The general solution give
From playlist Solve Differential Equation (Particular Solution) #Integration

CERIAS Security: Recent Attacks on MD5 4/6
Clip 4/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

Types of Cryptography Algorithms | Cryptography in Network Security | Edureka | Cybersecurity Live-2
🔥Edureka Cybersecurity Online Training: https://www.edureka.co/cybersecurity-certification-training This Edureka video on Cryptography Algorithms Explained talks about the various algorithms used for cryptography and how they help in making our data secure. Cybersecurity Training Playlist
From playlist Edureka Live Classes 2020

Block Ciphers and Data Encryption Standard (DES): Part 2
Fundamental concepts of Block Cipher Design Principles are discussed. Differential cryptanalysis and linear cryptanalysis are explained.
From playlist Network Security

How to solve differential equations by substitution
Free ebook http://tinyurl.com/EngMathYT A basic example showing how substitutions can solve differential equations. The method is a very powerful technique.
From playlist Differential equations

CERIAS Security: Recent Attacks on MD5 1/6
Clip 1/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

Cryptanalysis of Vigenere cipher: not just how, but why it works
The Vigenere cipher, dating from the 1500's, was still used during the US civil war. We introduce the cipher and explain a standard method of cryptanalysis based on frequency analysis and the geometry of vectors. We focus on visual intuition to explain why it works. The only background
From playlist Classical Cryptography

Differential Equations: Exact DEs Example 1
It's important to be able to classify a differential equation so we can pick the right method to solve it. In this video, I run through the steps of how to classify a first order differential equation as separable, linear, exact, or neither.
From playlist Differential Equations