
Cryptograph: Substitution Cipher (Caesar Cipher)
This lesson explains how to encrypt and decrypt a message using a Caeser cipher. Site: http://mathispower4u.com
From playlist Cryptography

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

From playlist Week 2 2015 Shorts

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

Hunting for the Zodiac Killer | History's Greatest Mysteries (Season 4)
The Zodiac Killer is one of the most elusive serial killers of all time. See more in this clip from Season 4, Episode 2, "Who is the Zodiac Killer?" Watch all new episodes of History's Greatest Mysteries, returning Monday, January 30 at 9/8c, and stay up to date on all of your favorite Th
From playlist History's Greatest Mysteries | Official Series Playlist | History

The Hunt for the Zodiac Killer: Codebreaking 101 | History
Kevin Knight describes how a team developed a high-tech codebreaking AI called Carmel to crack the Zodiac cypher. Subscribe for more from Hunt for the Zodiac Killer and other great HISTORY shows: http://histv.co/SubscribeHistoryYT Find out more about the show and watch full episodes on o
From playlist The Hunt for the Zodiac Killer | Official Playlist | History

Cryptography: Caesar Cipher With Shift
This lesson explains how to encrypt and decrypt a message using Caeser cipher with a shift. Site: http://mathispower4u.com
From playlist Cryptography

The Hunt For The Zodiac Killer: Code Breakers Unite | Premieres Nov. 14 | History
HISTORY delves into the mystery of the Zodiac Killer while on a mission to crack the code. Throughout the early 1960s and 1970s, the Zodiac Killer, one of history’s most famous unidentified serial murderers, terrorized America in a spree of heinous attacks, sending taunting letters and cod
From playlist The Hunt for the Zodiac Killer | Official Playlist | History

The Hunt For The Zodiac Killer: The Secret Weapon | Premieres Nov. 14 | History
A team of top investigators and code-breakers work in tandem with a super-computer, known as CARMEL, the first of its kind programmed to think like a killer. Throughout the early 1960s and 1970s, the Zodiac Killer, one of history’s most famous unidentified serial murderers, terrorized Amer
From playlist The Hunt for the Zodiac Killer | Official Playlist | History

The Hunt For The Zodiac Killer: The Holy Grail Of Unbroken Ciphers | Premieres Nov. 14 | History
The Zodiac Killer's ultimate taunt are four mysterious coded messages sent to the press. Throughout the early 1960s and 1970s, the Zodiac Killer, one of history’s most famous unidentified serial murderers, terrorized America in a spree of heinous attacks, sending taunting letters and codes
From playlist The Hunt for the Zodiac Killer | Official Playlist | History

Who Is the Zodiac Killer? | History's Greatest Mysteries | #Shorts
The Zodiac Killer is one of the most elusive serial killers of all time. See more in this #Short from History's Greatest Mysteries. Watch all new episodes of History's Greatest Mysteries, returning Monday, January 30 at 9/8c, and stay up to date on all of your favorite The HISTORY Channe
From playlist History's Greatest Mysteries | Official Series Playlist | History

MATH3411 Information, Codes and Ciphers This problem presents digital signatures via the DSS scheme. We are asked to find a public key from a private key, to generate a digital signature, and to check the validity of a received signature. Presented by Thomas Britz, School of Mathematics
From playlist MATH3411 Information, Codes and Ciphers

Pseudorandom Number Generation and Stream Ciphers
Fundamental concepts of Pseudorandom Number Generation are discussed. Pseudorandom Number Generation using a Block Cipher is explained. Stream Cipher & RC4 are presented.
From playlist Network Security

CMU Neural Nets for NLP 2017 (4): Why is word2vec so fast? Efficiency Tricks.
This lecture (by Taylor Berg-Kirkpatrick) for CMU CS 11-747, Neural Networks for NLP (Fall 2017) covers: * Softmax Approximations: Negative Sampling, Hierarchical Softmax * Parallel Training * Tips for Training on GPUs (this time slides are not in the video, so please reference the slides
From playlist CMU Neural Nets for NLP 2017

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

The Computer and Turing: Crash Course History of Science #36
Computers and computing have changed a lot over the History of Science but ESPECIALLY over the last 100 years. In this episode of Crash Course History of Science, we have a look at that history around World War Two and how that conflict forced changes in computing. *** Crash Course is
From playlist Back to School - Expanded
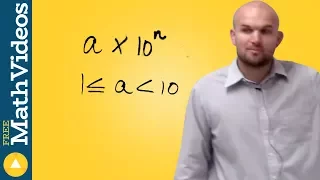
What is the definition of scientific notation
👉 Learn about scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is the number of digits up to t
From playlist Scientific Notation | Learn About

In Pursuit of The Zodiac Killer | Crimes of the Century
This video is lecture nine from the series "Crimes of the Century: A Selective History of Infamy" Stream the full series now on Wondrium! http://www.Wondrium.com/YouTube More than 50 years later, the Zodiac case remains as cold as the chilly night this infamous serial killer slayed the fi
From playlist Biology and Health

This Is What Stars and Constellations of Zodiac Really Look Like
Hello and welcome! My name is Anton and in this video, we will talk about Zodiac and Constellations. So I pre-recorded this video in December of 2018, but didn't get a chance to post it until now. Enjoy it nevertheless! Support this channel on Patreon to help me make this a full time job:
From playlist Scientific and Astronomical Concepts

Modern Symmetric Ciphers - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography