
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

TOR Extended 1 - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Steganography Tutorial - Hide Messages In Images
Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step further by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it
From playlist Ethical Hacking & Penetration Testing - Complete Course

Totient Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Tor Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
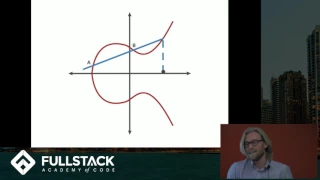
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Learn more advanced front-end and full-stack development at: https://www.fullstackacademy.com Elliptic Curve Cryptography (ECC) is a type of public key cryptography that relies on the math of both elliptic curves as well as number theory. This technique can be used to create smaller, fast
From playlist Elliptic Curves - Number Theory and Applications

Phong NGUYEN - Recent progress on lattices's computations 1
This is an introduction to the mysterious world of lattice algorithms, which have found many applications in computer science, notably in cryptography. We will explain how lattices are represented by computers. We will present the main hard computational problems on lattices: SVP, CVP and
From playlist École d'Été 2022 - Cohomology Geometry and Explicit Number Theory

Structure and randomness in the prime numbers - Terence Tao
Speaker : Terence Tao ( Department of Mathematics, UCLA ) Venue : AG 66, TIFR, Mumbai Date and Time : 23 Feb 12, 16:00 "God may not play dice with the universe, but something strange is going on with the prime numbers" - Paul Erdos The prime numbers are a fascinating blend of both struc
From playlist Public Lectures

Open Days 2019 Part 2: Pure Mathematics at Oxford
Our Open Days are intended to give an insight in to Maths at Oxford, whether you are a potential applicant or are just curious. In this talk to an audience of sixth-formers (High School students) and their families, Vicky Neale gives a glimpse of the undergraduate Pure Maths courses throug
From playlist Study Here - advice for applying to Oxford Mathematics

Totient - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Elliptic Curves: Good books to get started
A few books for getting started in the subject of Elliptic Curves, each with a different perspective. I give detailed overviews and my personal take on each book. 0:00 Intro 0:41 McKean and Moll, Elliptic Curves: Function Theory, Geometry, Arithmetic 10:14 Silverman, The Arithmetic of El
From playlist Math
Entropy, Algebraic Integers and Moduli of Surfaces - Curtis McMullen
Curtis McMullen Harvard University December 7, 2010 For more videos, visit http://video.ias.edu
From playlist Mathematics

STEMerch Store: https://stemerch.com/ Support the Channel: https://www.patreon.com/zachstar PayPal(one time donation): https://www.paypal.me/ZachStarYT This video continues on from part 1 and covers pure math concepts such as abstract algebra, real analysis, and topology. Those classes ha
From playlist Math Major

Quantum physics and the computational lens - Dorit Aharonov
A Celebration of Mathematics and Computer Science Celebrating Avi Wigderson's 60th Birthday October 5 - 8, 2016 More videos on http://video.ias.edu
From playlist Mathematics

Daniele Agostini - Curves and theta functions: algebra, geometry & physics
Riemann’s theta function is a central object throughout mathematics, from algebraic geometry to number theory, and from mathematical physics to statistics and cryptography. One of my long term projects is to develop a program to study and connect the various aspects - geometric, computatio
From playlist Research Spotlight

Edray Goins, Critical points of toroidal Belyi maps
VaNTAGe seminar, August 31, 2021 License CC-BY-NC-SA
From playlist Belyi maps and Hurwitz spaces

Tor Extended 3 - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Applied topology 2: Topology and homotopy equivalences
Applied topology 2: Topology and homotopy equivalences Abstract: From a high-level perspective, we try to explain what topology measures and ignores about shapes. We explain how a coffee cup is in some sense the same shape as a donut. Topologists often deem two shapes to be the same if th
From playlist Applied Topology - Henry Adams - 2021
