
An general explanation of the underactive thyroid.
From playlist For Patients

The method of determining eigenvalues as part of calculating the sets of solutions to a linear system of ordinary first-order differential equations.
From playlist A Second Course in Differential Equations

Changing notation with complex eigenvalues.
From playlist A Second Course in Differential Equations

Learn all about angles. An angle is a figure formed by two rays sharing a common endpoint. An angle can be classified as acute, right, obtuse, straight or refrex. An acute angle is an angle which measures less than 90 degrees. A right angle measures 90 degrees. An obtuse angle measures mor
From playlist Learn all about basics of Angles #Geometry

25c3: An introduction to new stream cipher designs
Speaker: Tor E. Bjørstad Turning data into line noise and back Even with "nothing to hide", we want to protect the privacy of our bits and bytes. Encryption is an important tool for this, and stream ciphers are a major class of symmetric-key encryption schemes. Algorithms such as RC4 (us
From playlist 25C3: Nothing to hide

Narcissism is the word we routinely use to describe someone self-satisfied and arrogant. But what do we really mean by the word – and are we applying it correctly? If you like our films, take a look at our shop (we ship worldwide): https://goo.gl/YfXSQO Join our mailing list: http://bit.ly
From playlist SELF

The idea of ‘atonement’ sounds very old-fashioned and is deeply rooted in religious tradition. To atone means, in essence, to acknowledge one’s capacity for wrongness and one’s readiness for apology and desire for change. It’s a concept that every society needs at its center. For gifts and
From playlist RELATIONSHIPS
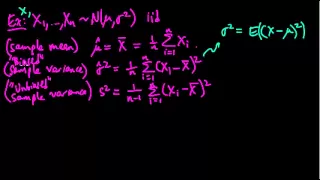
Definition of an estimator. Examples of estimators. Definition of an unbiased estimator.
From playlist Machine Learning

In this continuing look at the management of acute surgical conditions of the esophagus we take a look at the anatomy of the esophagus.
From playlist Acute Care Surgery

Now, a look at the principles of the function of the esophagus
From playlist Acute Care Surgery

Milky Way Erupted With a Power of Million Supernovae, But Why?
You can buy Universe Sandbox 2 game here: http://amzn.to/2yJqwU6 Hello and welcome! My name is Anton and in this video, we will talk about a new discovery that our galaxy very likely experienced a powerful explosion 3.5 million years ago, turning it into a Seyfert galaxy. Paper: https://a
From playlist The Milky Way

A11 Eigenvalues with complex numbers
Eigenvalues which contain complex numbers.
From playlist A Second Course in Differential Equations

Roberto La Scala, Università di Bari
Roberto La Scala, Università di Bari Ciphers and difference equations
From playlist Spring 2021 Online Kolchin Seminar in Differential Algebra