
ADFGVX Cipher: Encryption and Decryption (OLD VERSION: SEE NEW VERSION LINK BELOW)
This video has been replaced with an updated video: visit https://youtu.be/T0xfKiU9Rr4 Encryption and Decryption of the World War One ADFGVX Cipher, through examples.
From playlist Classical Cryptography

ADFGVX Cipher: Encryption and Decryption (Updated)
Encryption and Decryption of the World War One ADFGVX Cipher, through examples. This video replaces an earlier one with the same content, but has some improvements and corrections. #cryptography
From playlist Classical Cryptography

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

Cryptography: Codes, Ciphers, and Connections
The encryption of information is as old as information itself. Ever since two people wanted to pass something along, so has there been a third party who wanted to be privy to it. This back and forth battle of creating codes, breaking them, and finding new ones has been happening quietly fo
From playlist Mathematics

Kernel Recipes 2015 - WireGuard: A Kernelspace VPN - by J. A. Donenfeld
WireGuard is an upcoming project to replace IPSec with a newer more modern and secure VPN protocol. It lives inside the kernel and provides a very simple and novel interface for setting up secure encrypted network tunnels. All the cryptography is cutting edge -- DJB's Curve25519, ChaCha20,
From playlist Kernel Recipes 2015

This video is a brief introduction to linear codes: dimensions, G (generating matrix), H (parity check matrix), their forms. Also gives an example of how to convert between G and H. Here is the formal definition of a Linear Code: A linear code of dimension k and length n over a field
From playlist Cryptography and Coding Theory

Block Cipher Operation (BCO): Part 1
Fundamental concepts of Block Cipher Operation are discussed. Various extensions of DES are presented. Encryption modes for long messages are explained. Double DES, Triple DES, DES-X Encryption Modes for long messages: Electronic Code Book (ECB) Cipher Block Chaining (CBC) Cipher Feedback
From playlist Cryptography, Security

Speaker: khorben Firmware reverse-engineering tactics This lecture aims at providing ideas and practical techniques about the reverse-engineering process of equipment firmware images. It touches upon data encoding, compression, bootstraps, deciphering, disassembly, and emulation. Thi
From playlist 23C3: Who can you trust

Oscar Randal-Williams: Moduli spaces of manifolds (part 2)
The lecture was held within the framework of the Hausdorff Trimester Program: Homotopy theory, manifolds, and field theories and Introductory School (05.05.2015)
From playlist HIM Lectures 2015

Advancing Focus - Glen Goodwin - JSConf US 2019
Some things in web development just work; they do what they are supposed to do day in and day out, and we don't ever have to worry about them. It's the "little engine that could" story: it's reliable, it stable, it's trustworthy. The Focus subsystem is one such system... reliable, stable,
From playlist JSConf US 2019

Special Topics - GPS (66 of 100) WGS 84 World Geodetic System
Visit http://ilectureonline.com for more math and science lectures! http://www.ilectureonline.com/donate https://www.patreon.com/user?u=3236071 We will learn about the WGS 84 (World Geodetic System). It was established and maintained by the US National Geospatial – Intelligence Agency la
From playlist SPECIAL TOPICS 2 - GPS

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

Block Ciphers and Data Encryption Standard (DES): Part 2
Fundamental concepts of Block Cipher Design Principles are discussed. Differential cryptanalysis and linear cryptanalysis are explained.
From playlist Network Security

Learn how to deploy a Docker container with Galaxy software on the NSF cloud system, Jetstream.
From playlist Jetstream - the first NSF-funded production cloud environment

Deconstructing diversity starting out, getting there, staying alive by Kartik Shanker
The Third Bangalore School on Population Genetics and Evolution DATE:05 March 2018 to 17 March 2018 VENUE:Ramanujan Lecture Hall, ICTS Bangalore. No living organism escapes evolutionary change. Evolutionary biology thus connects all biological disciplines. To understand the processes dri
From playlist Third Bangalore School on Population Genetics and Evolution
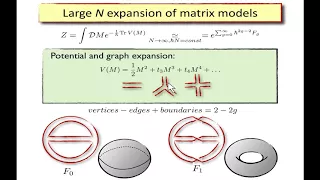
Piotr Sułkowski (6/28/17) Bedlewo: Topological recursion, chord diagrams, and RNA complexes
I will introduce the topological recursion, which is a universal formalism — originating in the realm of matrix models — which assigns an infinite family of symplectic invariants to a given algebraic curve. I will illustrate the power of this formalism by showing how it can be used to solv
From playlist Applied Topology in Będlewo 2017

EMBERCONF 2015 - ALIGNING EMBER WITH WEB STANDARDS
BY: MATTHEW BEALE JavaScript is a language awakening from long slumber. Browser vendors have already adopted many features from the ES6 specification ahead of its formal release in 2015, and even implemented some of the early ES7 draft specification. Ember, to help us build apps today,
From playlist EmberConf 2015

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Outbreak surveillance and investigation using IRIDA and SNVPhyl, 20160629
Galaxy Community Conference 2016, Indiana University - Bloomington | https://gcc2016.iu.edu/ https://gcc16.sched.com/event/cb10e4d8df21798b84856c3afc67e196# Authors: Aaron Petkau (1), Franklin Bristow (1), Thomas Matthews (1), Josh Adam (1), Philip Mabon (1), Cameron Sieffert (1), Eric E
From playlist 2016 Galaxy User Community Conference (GCC16)