
An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

My stream schedule has changed, I will be skipping the morning stream and instead be keeping to the Sunday streams. When I have time I'll be streaming after work, but no set schedule at this time.
From playlist Channel updates

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Speakers: Henryk Plötz. Karsten Nohl Many RFID tags have weaknesses, but the security level of different tags varies widely. Using the Mifare Classic cards as an example, we illustrate the complexity of RFID systems and discuss different attack vectors. To empower further analysis of RFID
From playlist 25C3: Nothing to hide

Symmetric Key Cryptography: The XOR Cipher
This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers the XOR logical operation, that is the exclusive OR operation, explaining how it can be used to encrypt and decrypt a sequence of binary digits. XOR is an im
From playlist Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

22C3: Learning cryptography through handcyphers
Speaker: Brenno de Winter Shaping a digital future with ancient wisdom For many people cryptography is something that they consider too complicated. But actually one can understand the principles very well if they only try. By looking at old handcyphers used for coding one can begin to u
From playlist 22C3: Private Investigations

State-of-the-art named entity recognition with BERT | Webinar
Get your Free Spark NLP and Spark OCR Free Trial: https://www.johnsnowlabs.com/spark-nlp-try-free/ Watch all NLP & AI webinars: https://events.johnsnowlabs.com/webinars Deep neural network models have recently achieved state-of-the-art performance gains in a variety of natural language p
From playlist AI & NLP Webinars
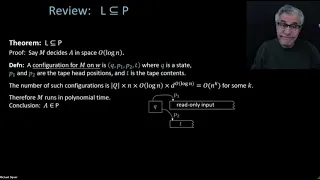
MIT 18.404J Theory of Computation, Fall 2020 Instructor: Michael Sipser View the complete course: https://ocw.mit.edu/18-404JF20 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP60_JNv2MmK3wkOt9syvfQWY Reviewed log space: NL is a subset of SPACE(log^2n) and NL is a subse
From playlist MIT 18.404J Theory of Computation, Fall 2020

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Network Security: Classical Encryption Techniques
Fundamental concepts of encryption techniques are discussed. Symmetric Cipher Model Substitution Techniques Transposition Techniques Product Ciphers Steganography
From playlist Network Security

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

Zaher Hani: Effective dynamics for the cubic nonlinear Schroedinger equation confined by domain ...
... or potential The lecture was held within the framework of the Hausdorff Trimester Program Harmonic Analysis and Partial Differential Equations. 11.6.2014
From playlist HIM Lectures: Trimester Program "Harmonic Analysis and Partial Differential Equations"

Numerical Homogenization by Localized Orthogonal Decomposition (Lecture 2) by Daniel Peterseim
DISCUSSION MEETING Multi-Scale Analysis: Thematic Lectures and Meeting (MATHLEC-2021, ONLINE) ORGANIZERS: Patrizia Donato (University of Rouen Normandie, France), Antonio Gaudiello (Università degli Studi di Napoli Federico II, Italy), Editha Jose (University of the Philippines Los Baño
From playlist Multi-scale Analysis: Thematic Lectures And Meeting (MATHLEC-2021) (ONLINE)

MIT 18.404J Theory of Computation, Fall 2020 Instructor: Michael Sipser View the complete course: https://ocw.mit.edu/18-404JF20 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP60_JNv2MmK3wkOt9syvfQWY Quickly reviewed last lecture. Finished Immerman-Szelepcsenyi theorem
From playlist MIT 18.404J Theory of Computation, Fall 2020

Block Ciphers and Data Encryption Standard (DES): Part 2
Fundamental concepts of Block Cipher Design Principles are discussed. Differential cryptanalysis and linear cryptanalysis are explained.
From playlist Network Security

19. Cell Trafficking and Protein Localization
MIT 7.016 Introductory Biology, Fall 2018 Instructor: Barbara Imperiali View the complete course: https://ocw.mit.edu/7-016F18 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP63LmSVIVzy584-ZbjbJ-Y63 Professor Imperiali talks about trafficking, or how things get to where
From playlist MIT 7.016 Introductory Biology, Fall 2018
