
Cryptograph: Substitution Cipher (Caesar Cipher)
This lesson explains how to encrypt and decrypt a message using a Caeser cipher. Site: http://mathispower4u.com
From playlist Cryptography

From playlist Week 2 2015 Shorts

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

Pseudorandom Number Generation and Stream Ciphers
Fundamental concepts of Pseudorandom Number Generation are discussed. Pseudorandom Number Generation using a Block Cipher is explained. Stream Cipher & RC4 are presented.
From playlist Network Security

Toy Substitution Cipher 1 - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

25c3: An introduction to new stream cipher designs
Speaker: Tor E. Bjørstad Turning data into line noise and back Even with "nothing to hide", we want to protect the privacy of our bits and bytes. Encryption is an important tool for this, and stream ciphers are a major class of symmetric-key encryption schemes. Algorithms such as RC4 (us
From playlist 25C3: Nothing to hide

Toy Substitution Cipher 2 - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
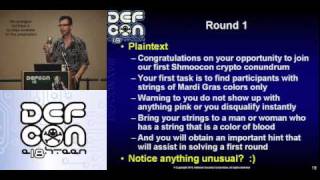
DEFCON 18: Tales from the Crypt 2/4
Speaker: G. Mark Hardy Learn how to crack crypto contests like a pro. The speaker has awarded half a dozen free round-trip plane tickets to previous contest winners. Maybe you'll be next. From the daily newspaper puzzle to badge contests to codes that keep the National Security Agency a
From playlist DEFCON 18-1

Episode 042: A Trans, Religious, Simulation Allegory, Oh My! The Matrix Film Franchise
Join Alex in an exploration of the themes and allegories — that have a psychological flair, of course — in The Matrix (1999) film franchise! In this episode, Alex dives into the Wachowski sisters' true meaning of the first film, which was a transgender allegory. He also explores the iconic
From playlist CinemaPsych Podcast

RailsConf 2022 - Pictures Of You, Pictures Of Me, Crypto Steganography by Sean Marcia
I was puzzled when a friend sent me a Buffy the Vampire Slayer picture out of the blue but, knowing that friend is an oddball, thought nothing of it. Days later, again without warning, a Babylon 5 picture. A few days after that a picture from Firefly. Then he repeated the pictures. A crypt
From playlist RailsConf 2022

OWASP AppSecUSA 2012: Web App Crypto - A Study in Failure
Speaker: Travis H. Seldom in cryptography do we have any unconditional proofs of the difficulty of defeating our cryptosystems. Furthermore, we are often defeated not by the attacks we anticipated, but the vectors we did not know about. Like fire and safety engineers, we learn from the mi
From playlist OWASP AppSecUSA 2012

The Simplest Encoding You’ve Never Heard Of
As soon as you start looking into different algorithms and techniques to build models that learn from data, you realize that many, if not most of them, don’t like text: they can’t process it directly, they only work with numbers. This video will show you how three encoding techniques work
From playlist Machine Learning Techniques

Jessica Sklar - Mathematical Art Inspirations, Instantiations, and Installations - CoM Feb 2022
During 2020, while the world shut down, creativity flourished. Choral groups sang over Zoom, friends attended virtual cocktail hours, and mathematicians and artists spent their lockdown hours knitting, painting, and constructing wonders. In this talk, I’ll show and discuss pieces by QED A
From playlist Celebration of Mind

Cryptography: Caesar Cipher With Shift
This lesson explains how to encrypt and decrypt a message using Caeser cipher with a shift. Site: http://mathispower4u.com
From playlist Cryptography

I Interviewed NEIL PATRICK HARRIS and it got weird.. (Puzzles, Magic, Escape rooms)
BUY BOX ONE HERE: https://www.target.com/p/box-one-presented-by-neil-patrick-harris-game/-/A-79810129 Today I had the pleasure of chatting with Neil Patrick Harris about his latest creation, it's an immersive board game which takes the player on an adventure! Box One! We chatted magic, puz
From playlist Puzzles!

Cryptography: Transposition Cipher
This lesson explains how to encrypt and decrypt a message using a transposition cipher. Site: http://mathispower4u.com
From playlist Cryptography

It Took Me 4 YEARS To Solve This Mystery!!
MY SHOP: https://www.1st.shop/ Theory 11: https://www.theory11.com/ Today I'm going to attempt to solve the Mystery behind the Bad Robot Playing Cards Puzzle! This Puzzle will lead me down a rabbit hole and hopefully I can find my way out! Cool Stuff Available here: https://bit.ly/3f8RDm0
From playlist Puzzles!
