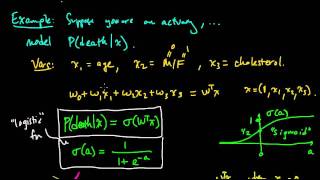Pseudorandom Number Generation and Stream Ciphers
Fundamental concepts of Pseudorandom Number Generation are discussed. Pseudorandom Number Generation using a Block Cipher is explained. Stream Cipher & RC4 are presented.
From playlist Network Security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography
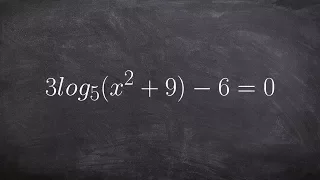
Isolating a logarithm and using the power rule to solve
👉 Learn how to solve logarithmic equations. Logarithmic equations are equations with logarithms in them. To solve a logarithmic equation, we first isolate the logarithm part of the equation. After we have isolated the logarithm part of the equation, we then get rid of the logarithm. This i
From playlist Solve Logarithmic Equations

What Is Quantum Computing | Quantum Computing Explained | Quantum Computer | #Shorts | Simplilearn
🔥Explore Our Free Courses With Completion Certificate by SkillUp: https://www.simplilearn.com/skillup-free-online-courses?utm_campaign=QuantumComputingShorts&utm_medium=ShortsDescription&utm_source=youtube Quantum computing is a branch of computing that focuses on developing computer tech
From playlist #Shorts | #Simplilearn
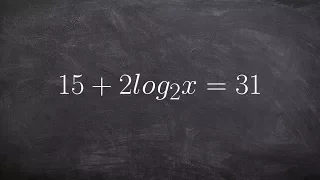
Math tutorial for solving a multi step logarithmic equation
👉 Learn how to solve logarithmic equations. Logarithmic equations are equations with logarithms in them. To solve a logarithmic equation, we first isolate the logarithm part of the equation. After we have isolated the logarithm part of the equation, we then get rid of the logarithm. This i
From playlist Solve Logarithmic Equations

Solving a natural logarithmic equation using your calculator
👉 Learn how to solve logarithmic equations. Logarithmic equations are equations with logarithms in them. To solve a logarithmic equation, we first isolate the logarithm part of the equation. After we have isolated the logarithm part of the equation, we then get rid of the logarithm. This i
From playlist Solve Logarithmic Equations

Linear algebra for Quantum Mechanics
Linear algebra is the branch of mathematics concerning linear equations such as. linear functions and their representations in vector spaces and through matrices. In this video you will learn about #linear #algebra that is used frequently in quantum #mechanics or #quantum #physics. ****
From playlist Quantum Physics

Follow-up: Barbie electronic typewriter
Here is a copy of the description from the Barbie video: ---- I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett fr
From playlist My Maths Videos

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Live CEOing Ep 544: Language Design in Wolfram Language [Ciphers & WFR Submissions] [Part 01]
In this episode of Live CEOing, Stephen Wolfram discusses upcoming improvements and features to the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Stephen Wolfram
From playlist Behind the Scenes in Real-Life Software Design
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

What is Bill Cipher? (Scientific Analysis)
What is Bill Cipher? Today we discover the very very confusing science of what Gravity Fall's Bill Cipher is. =======WARNING VERY VERY CONFUSING======= This video talks about dimensions and alternate universes. Your mind might explode! Sources: -http://en.wikipedia.org/wiki/Four-dim...
From playlist Scientific Videos

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

The Barbie electronic typewriter - with Just My Typewriter
I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett from Just My Typewriter, check out her channel here: https://www.y
From playlist My Maths Videos

25c3: An introduction to new stream cipher designs
Speaker: Tor E. Bjørstad Turning data into line noise and back Even with "nothing to hide", we want to protect the privacy of our bits and bytes. Encryption is an important tool for this, and stream ciphers are a major class of symmetric-key encryption schemes. Algorithms such as RC4 (us
From playlist 25C3: Nothing to hide

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security