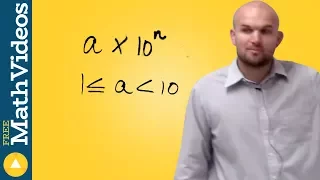
What is the definition of scientific notation
👉 Learn about scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is the number of digits up to t
From playlist Scientific Notation | Learn About

Raising a scientific number to the third power
👉 Learn how to multiply numbers written in scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is
From playlist Scientific Notation

Determine the product of two very large numbers by converting to scientific notation
👉 Learn how to multiply numbers written in scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is
From playlist Scientific Notation
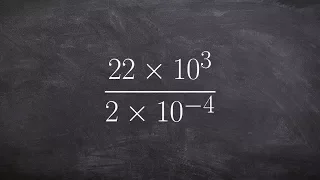
Dividing two numbers in scientific notation then rewriting answer in scientific notation
👉 Learn how to divide numbers written in scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is t
From playlist Scientific Notation

Converting a number to scientific notation
👉 Learn how to convert numbers to scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is the numb
From playlist Scientific Notation

Multiplying in scientific notation with negative exponents
👉 Learn how to multiply numbers written in scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is
From playlist Scientific Notation

Dominique Unruh - The quantum random oracle model Part 1 of 2 - IPAM at UCLA
Recorded 28 July 2022. Dominique Unruh of Tartu State University presents "The quantum random oracle model I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: The random oracle is a popular heuristic in classical security proofs that allows us to construct
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

How to create firewall rules with Security Groups | Amazon Web Services | AWS
In this video, we demonstrate how to create firewall rules for an EC2 instance in Amazon Web Services. 🕒🦎 VIDEO SECTIONS 🦎🕒 00:00 Welcome to DEEPLIZARD - Go to deeplizard.com for learning resources 00:30 Help deeplizard add video timestamps - See example in the description 06:06 Collecti
From playlist AWS - Amazon Web Services EC2 Management

Lec 24 | MIT 6.033 Computer System Engineering, Spring 2005
Advanced Authentication View the complete course at: http://ocw.mit.edu/6-033S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.033 Computer System Engineering, Spring 2005

Identify the Symbols in Statistics
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys Identify the Symbols in Statistics
From playlist Statistics

Anne Broadbent - Information-Theoretic Quantum Cryptography Part 1 of 2 - IPAM at UCLA
Recorded 27 July 2022. Anne Broadbent of the University of Ottawa presents "Information-Theoretic Quantum Cryptography" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: These lectures are an introduction to the interplay between quantum information and cryp
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Jonathan Katz - Introduction to Cryptography Part 3 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography III" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will introduce the notions of zero-knowledge proofs, proofs of knowledge, and secure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography
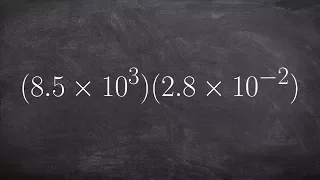
Multiplying numbers in scientific notation
👉 Learn how to multiply numbers written in scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is
From playlist Scientific Notation

Foundational Aspects of Blockchain Protocols (Lecture 1) by Juan Garay
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

Finding product of two numbers when they are in scientific notation
👉 Learn how to multiply numbers written in scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is
From playlist Scientific Notation
Nexus Trimester - Manoj Prabhakaran (University of Illinois) - 2/2
Some Capacity Question in MPC - 2/2 Manoj Prabhakaran (University of Illinois) March 18, 2016 Abstract: Secure multiparty computation allows two or more parties to perform a distributed computation on their local inputs while hiding the inputs from each other. This part of the minicourse
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

CERIAS Security: Security issues within embedded software development 4/5
Clip 4/5 Speaker: Ron Buskey · Motorola Software development processes and tools used for small communication devices have changed significantly over the years. Some of these practices and processes have resulted in improvements in quality and time to market for their target products,
From playlist The CERIAS Security Seminars 2007

Dividing two numbers in scientific notation
👉 Learn how to divide numbers written in scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is t
From playlist Scientific Notation
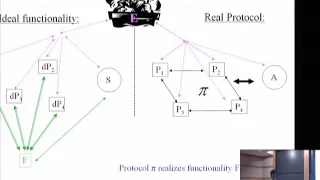
A Completeness Theorem for Pseudo-Linear Functions with App... - Charanjit Jutla
Charanjit Jutla IBM T. J. Watson Research Center February 28, 2010 We prove completeness results for certain class of functions which have implications for automatic proving of universally-composable security theorems for ideal and real functionalities composed of if-then-else programs wi
From playlist Mathematics
