
What Is Quantum Computing | Quantum Computing Explained | Quantum Computer | #Shorts | Simplilearn
🔥Explore Our Free Courses With Completion Certificate by SkillUp: https://www.simplilearn.com/skillup-free-online-courses?utm_campaign=QuantumComputingShorts&utm_medium=ShortsDescription&utm_source=youtube Quantum computing is a branch of computing that focuses on developing computer tech
From playlist #Shorts | #Simplilearn

Other Public Key Cryptosystems: Part 1
Fundamental concepts of Diffie-Hellman Key exchange are discussed. ElGamal Cryptosystem is presented. Elliptic curves are Analyzed.
From playlist Network Security

Kritin Lauter, Supersingular isogeny graphs in cryptography
VaNTAGe Seminar, September 20, 2022 License: CC-BY-NC-SA Some of the papers mentioned in this talk: Charles, Goren, Lauter 2007: https://doi.org/10.1007/s00145-007-9002-x Mackenzie 2008: https://doi.org/10.1126/science.319.5869.1481 Pizer 1990: https://doi.org/10.1090/S0273-0979-1990-15
From playlist New developments in isogeny-based cryptography

Seminar on Applied Geometry and Algebra (SIAM SAGA): Gretchen Matthews
Title: Multivariate Goppa Codes Speaker: Gretchen Matthews, Virginia Tech Date: Tuesday, May 10, 2022 at 11:00am Eastern Abstract: Goppa codes were introduced in 1971 by V. D. Goppa using a univariate polynomial g(x), called a generator polynomial, over a finite field. Properties of the G
From playlist Seminar on Applied Geometry and Algebra (SIAM SAGA)

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

Asymmetric Cryptosystems - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
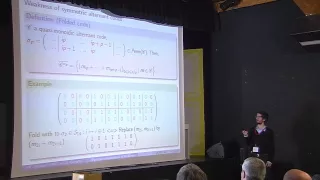
Frédéric de Portzamparc - Faiblesse structurelle des schémas McEliece avec clefs compactes
Faiblesse structurelle des schémas McEliece avec clefs compactes
From playlist Journées Codage et Cryptographie 2014

From playlist Cryptography

Other Public Key Cryptosystems: Part 2
Fundamental concepts of Diffie-Hellman Key exchange are discussed. ElGamal Cryptosystem is presented. Elliptic curves are Analyzed.
From playlist Network Security

Alain Couvreur - Comment domestiquer les codes de Goppa sauvages?
Le schéma de McEliece est un schéma de chiffrement basé sur les codes correcteurs d'erreurs dont la sécurité repose sur la difficulté à décoder un code aléatoire. Parmi les différentes familles de codes algébriques proposées pour ce schéma, les codes de Goppa classiques sont les seuls à ré
From playlist Journées Codage et Cryptographie 2014

One Way Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

26C3: Yes We Cant - on kleptography and cryptovirology 5/6
Clip 5/6 Speaker: Moti Yung In this talk I will survey some of the results (with Adam Young) on Cryptovirology (the art of employing public key cryptography maliciously as part of a malware attack, such as in ransomware) and the related Kleptography (the art of embedding cryptographic
From playlist 26C3: Here be dragons day 3

Challenge Question - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography - Seminar 1 - Foundations
This seminar series is about the mathematical foundations of cryptography. In the first seminar Eleanor McMurtry introduces cryptography and explains some of the problems that need to be solved in order to develop proper foundations. The webpage for this seminar is https://lnor.net/uc-sem
From playlist Metauni

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Stanford Seminar - The Evolution of Public Key Cryptography
EE380: Computer Systems Colloquium Seminar The Evolution of Public Key Cryptography Speaker: Martin Hellman, Stanford EE (Emeritus) While public key cryptography is seen as revolutionary, after this talk you might wonder why it took Whit Diffie, Ralph Merkle and Hellman so long to discov
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

