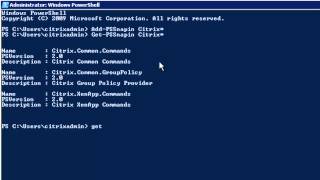
More videos like this online at http://www.theurbanpenguin.com if you are looking to make a start with PowerShell this may help you on your way using PowerShell with Citrix XenApp. We look at how you can list command by the module and the associated verb or noun
From playlist Citrix

Citrix : Applying XenServer Updates
More videos like this online at http://www.theurbanpenguin.com In this video we look at how to apply updates and hot fixes to Citrix XenServer. I am using XenServer 6.0 and as updates become available I have the option to install them as required. The Server will need rebooting during the
From playlist Citrix

Learn all about Xavix through an interview and demo from e3 2006.
From playlist Classic HowStuffWorks

Pulling Clear Images DIrectly Off Satellites | GOES-15,16,17 and Himawari 8 HRIT
In the fall of 2016 I saw my first rocket launch and little did I know that the satellite on that rocket would come to shape and fill my thoughts for many years. We're no strangers to getting data out of space on this channel, but GOES-16 is special, and not just because I was there when i
From playlist Highlights

Symmetric Key Cryptography: The XOR Cipher
This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers the XOR logical operation, that is the exclusive OR operation, explaining how it can be used to encrypt and decrypt a sequence of binary digits. XOR is an im
From playlist Cryptography

Citrix : XenServer xe vm-import from Windows
More videos like this online at http://www.theurbanpenguin.com In this video we look at using xe.exe and vm-import to import a virtual machine appliacance into our Citrix XenServer host. XE is part of the XenCeter install on windows and we can access in the %PROGRAMFILES%\Citrix\XenCenter
From playlist Citrix

More videos like this can be found at http://www.theurbanpenguin.com In this video we look at configuring NTP on Citrix XenServer 6 from the command line rather than xsconsole. The menu is ok but , in my case, I want to delete one entry and add another. This then is a 2 step process wherea
From playlist Citrix
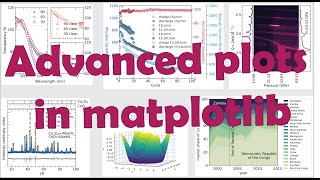
17. Python to make nice figures. Part III: advanced plots
This is part 3 in a 3-part series on making beautiful scientific figures in python. In this video, I will cover some advanced scientific plots in python. Check out part 1 and part 2 if you haven't yet. Part 1: https://youtu.be/rUV8VFbUi_U Part 2: https://youtu.be/Y8JWfGjj2okAll the files
From playlist Intro to Python Programming for Materials Engineers

Citrix : Branding Your Web Interface Site
More videos like this online at http://www.theurbanpenguin.com Sharing a Web Interface site for both Citrix XenApp and XenDesktop is probably what you would like to do. However the XenApp site is branded for XenApp and vice versa for XenDesktop. You may want to replace these central logo w
From playlist Citrix

Citrix : XenDesktop 5.6 Quick Deploy
More videos like this online at http://www.theurbanpenguin.com Here we take a look at installing Citrix XenDesktop 5.6 and using the quick deploy to create our desktop site. This version represents Citrix's latest VDI offering and enhances their status a leaders in desktop archtecture for
From playlist Citrix
Tensor Calculus 3b: Change of Coordinates
This course will eventually continue on Patreon at http://bit.ly/PavelPatreon Textbook: http://bit.ly/ITCYTNew Errata: http://bit.ly/ITAErrata McConnell's classic: http://bit.ly/MCTensors Table of Contents of http://bit.ly/ITCYTNew Rules of the Game Coordinate Systems and the Role of Te
From playlist Introduction to Tensor Calculus

Südafrika im Kampf gegen Tuberkulose
Im Schlepptau der Immunschwäche-Krankheit Aids ist in vielen Gebieten Afrikas auch die Tuberkulose zurückgekehrt. Immer häufiger treten dort resistente Tuberkulose-Erreger auf, gegen die kein Medikament mehr wirkt. Stefan Kaufmann vom Max-Planck-Institut für Infektionsbiologie in Berlin ar
From playlist Most popular videos
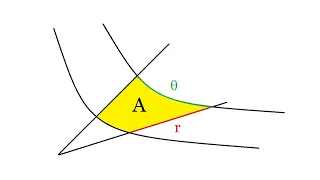
In this video, I introduce the hyperbolic coordinates, which is a variant of polar coordinates that is particularly useful for dealing with hyperbolas (and 3 dimensional versions like hyperboloids of one sheet or two sheets). Suprisingly (or not), they involve the hyperbolic trig functions
From playlist Double and Triple Integrals

BlueHat v9: RIA Security: Real-World Lessons from Flash and Silverlight 1/5
Clip 1/5 Presented by Peleus Uhley, Senior Security Researcher, Adobe and Jesse Collins, Software Security Engineer, Microsoft Rich Internet Application frameworks like Adobe Flash and Flex and Microsoft Silverlight allow developers to create unique and exciting Web applications; but i
From playlist BlueHat v9

"저희는 도구를 드립니다. 여러분은 창의력으로 만들어주세요." PC로 보실때는 서울산업진흥원(www.sba.kr)에서 제작한 유튜브 동영상에서 HD 동영상을 보시는 것이 좋습니다. 1080p로 설정해서 보시면 글자가 잘 보입니다. 오른쪽 하단 톱니모양에서 1080p를 선택하세요. 그리고 모바일로 보실 때에는 유튜브 앱으로 보십시오. 그래야 글자가 잘 보입니다. - PPT 파일, 소스파일은 첨부파일은 http://seouliotcenter.tistory.com/tag/java, http://makerspace.
From playlist 자바-JSP-Spring 강좌

Jacobian chain rule and inverse function theorem
A lecture that discusses: the general chain rule for the Jacobian derivative; and the inverse function theorem. The concepts are illustrated via examples and are seen in university mathematics.
From playlist Several Variable Calculus / Vector Calculus
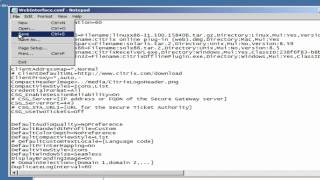
Citrix : Using the Web Interface to deliver clients
More videos like this can be found at http://www.theurbanpenguin.com This is just a quick step though in delivering the Citrix Receiver via the Web interface that ships with XenApp 6.5. It does mean an edit to the WebInterface.Conf as the change is not exposed in the Web Console.
From playlist Citrix

Gravitational Waves From Soft Theorem by Ashoke Sen
Discussion Meeting The Future of Gravitational-Wave Astronomy ORGANIZERS: Parameswaran Ajith, K. G. Arun, B. S. Sathyaprakash, Tarun Souradeep and G. Srinivasan DATE: 19 August 2019 to 22 August 2019 VENUE: Ramanujan Lecture Hall, ICTS Bangalore This discussion meeting, organized in c
From playlist The Future of Gravitational-wave Astronomy 2019
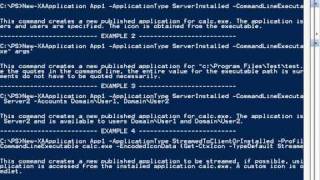
PowerShell: XenApp 6 Integration
More videos like this on http://www.theurbanpenguin.com : PowerShell simply cannot be ignored. Its power within Microsoft has been utilized for several years now and we are seeing increased third-pary support. Citris supply PowerShell Modules to manage there RD systems as standard with X
From playlist Citrix

The Deadly Return of TB in Swaziland (Disease Documentary) | Real Stories
The human stories behind the deadly infection TB A deadly airborne disease is making a dramatic comeback in Swaziland. Passed on by a simple cough or sneeze, TB is travelling fast and now new, multi-drug resistant variants are starting to appear all over the world. Multi-BAFTA winning fi
From playlist Medical Stories