
Other Public Key Cryptosystems: Part 1
Fundamental concepts of Diffie-Hellman Key exchange are discussed. ElGamal Cryptosystem is presented. Elliptic curves are Analyzed.
From playlist Network Security

Other Public Key Cryptosystems: Part 2
Fundamental concepts of Diffie-Hellman Key exchange are discussed. ElGamal Cryptosystem is presented. Elliptic curves are Analyzed.
From playlist Network Security

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

Nexus Trimester - Delaram Kahrobaei (City University of New York)
Cryptosystems Based on Group-Theoretic Problems: A Survey, New Results, Open Problems Delaram Kahrobaei (City University of New York) March 31, 2016 Abstract: In this talk I will survey some of the cryptosystems based on group theoretic problems and their computational complexity such as
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

!!Con West 2019 - Pranshu Bajpai: The Conjuring: ransomware edition!!
Presented at !!Con West 2019: http://bangbangcon.com/west Ransomware is malevolent software that possesses hosts, holds files hostage, and allows its dark masters to perform extortion. This form of malware seeks to infect weak hosts, acquires a unique encryption secret, encrypts user data
From playlist !!Con West 2019

How To Create Cryptocurrency In C++ | Introduction | #C | #crypto | #blockchain
Don’t forget to subscribe! This project series will teach you how to create your own cryptocurrency in C++. Throughout this course we will learn how to fork a crypto project, renaming things in the project, creating our very own genesis block, and changing parameters and values. In the en
From playlist Create Cryptocurrency In C++
Fang Song - Introduction to quantum computing Part 2 of 3 - IPAM at UCLA
Recorded 26 July 2022. Fang Song of Portland State University presents "Introduction to quantum computing II" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will focus on two major (families of) quantum algorithms: period finding (a.k.a. Hidd
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Seminar on Applied Geometry and Algebra (SIAM SAGA): Elisa Gorla
For more information, see our website: http://wiki.siam.org/siag-ag/index.php/Webinar Date: Tuesday, September 14 at 11:00am Eastern time zone Speaker: Elisa Gorla, University of Neuchâtel Title: Multivariate cryptography and the complexity of polynomial system solving Abstract: T
From playlist Seminar on Applied Geometry and Algebra (SIAM SAGA)

Asymmetric Cryptosystems - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

2022 I E Block Community Lecture: AI and Cryptography
July 13, 2022 How is Artificial Intelligence (AI) changing your life and the world? How can you expect your data to be kept secure and private in an AI-driven future? Kristin Lauter of Meta AI Research gives the I. E. Block Community Lecture titled "Artificial Intelligence and Cryptograph
From playlist SIAM Conference Videos
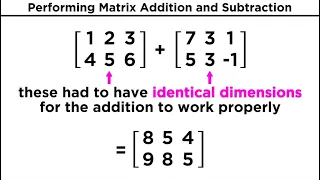
Types of Matrices and Matrix Addition
Alright, so we know what matrices are and we can use them to solve systems of linear equations, but we also have to do algebra with them! Let's start with the simplest operation of all, let's learn how to add two matrices together. Watch the whole Mathematics playlist: http://bit.ly/ProfD
From playlist Mathematics (All Of It)

One Way Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

26C3: Yes We Cant - on kleptography and cryptovirology 5/6
Clip 5/6 Speaker: Moti Yung In this talk I will survey some of the results (with Adam Young) on Cryptovirology (the art of employing public key cryptography maliciously as part of a malware attack, such as in ransomware) and the related Kleptography (the art of embedding cryptographic
From playlist 26C3: Here be dragons day 3

How To Create Cryptocurrency In C++ | Session 02 | #C | #crypto | #blockchain
Don’t forget to subscribe! This project series will teach you how to create your own cryptocurrency in C++. Throughout this course we will learn how to fork a crypto project, renaming things in the project, creating our very own genesis block, and changing parameters and values. In the en
From playlist Create Cryptocurrency In C++

Katherine E. Stange: Ring learning with errors and rounding
CIRM HYBRID EVENT Among the main candidates for post-quantum cryptography are systems based on the Ring Learning with Errors and Ring Learning with Rounding problems. I’ll give an overview of the number theory involved in these problems and try to persuade you to join in cryptanalyzing th
From playlist Number Theory

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

