
Ex: Determine the Value of a Number on a Logarithmic Scale (Log Form)
This video explains how to determine the value of several numbers on a logarithmic scale scaled in logarithmic form. http://mathispower4u.com
From playlist Using the Definition of a Logarithm

What are natural logarithms and their properties
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

What are the properties of logarithms and natural logarithms
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

When is a logarithm undefined? log4 (-32)
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

Solving the Logarithmic Equation log(A) = log(B) - C*log(x) for A
Solving the Logarithmic Equation log(A) = log(B) - C*log(x) for A Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys
From playlist Logarithmic Equations

What are the properties of logarithms
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

Discrete Logarithm Problem (DLP)
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Elliptic Curve Cryptography (ECC)
From playlist Cryptography Lectures

Some detail about cyclic groups and their application to cryptography, especially Diffie Hellman Key Exchange.
From playlist PubKey

This is an worked example of logarithms in Algebra 2.
From playlist Logs Group Quiz
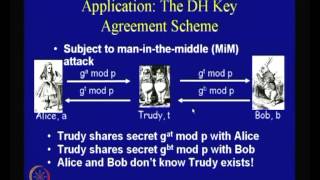
The Diffie-Hellman Problem and Security of ElGamal Systems
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
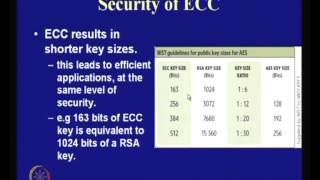
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Jan Maas : Gradient flows and Ricci cuevature in discrete and quantum probability
Recording during the thematic meeting : "Geometrical and Topological Structures of Information" the August 28, 2017 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker: Guillaume Hennenfent
From playlist Geometry

Math tutorial for evaluating a logarithmic expression when undefined
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

Eugenia Malinnikova : Uncertainty principles for discrete Schrödinger evolutions
Find this video and other talks given by worldwide mathematicians on CIRM's Audiovisual Mathematics Library: http://library.cirm-math.fr. And discover all its functionalities: - Chapter markers and keywords to watch the parts of your choice in the video - Videos enriched with abstracts, b
From playlist Analysis and its Applications

DLP Attacks and intro to El Gamal
We cover basic attacks on the discrete logarithm problem. The El Gamal Cipher is presented. We start discussion digital signatures.
From playlist PubKey

Parallel session 4 by Jayadev Athreya
Geometry Topology and Dynamics in Negative Curvature URL: https://www.icts.res.in/program/gtdnc DATES: Monday 02 Aug, 2010 - Saturday 07 Aug, 2010 VENUE : Raman Research Institute, Bangalore DESCRIPTION: This is An ICM Satellite Conference. The conference intends to bring together ma
From playlist Geometry Topology and Dynamics in Negative Curvature

Elliptic Curves - Lecture 17a - Torsion on groups associated to formal groups
This video is part of a graduate course on elliptic curves that I taught at UConn in Spring 2021. The course is an introduction to the theory of elliptic curves. More information about the course can be found at the course website: https://alozano.clas.uconn.edu/math5020-elliptic-curves/
From playlist An Introduction to the Arithmetic of Elliptic Curves

Overview of log properties - Inverse properties
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms
