Cryptography | Random number generation
Hardware random number generator
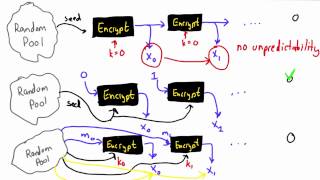
In computing, a hardware random number generator (HRNG) or true random number generator (TRNG) is a device that generates random numbers from a physical process, rather than by means of an algorithm. Such devices are often based on microscopic phenomena that generate low-level, statistically random "noise" signals, such as thermal noise, the photoelectric effect, involving a beam splitter, and other quantum phenomena. These stochastic processes are, in theory, completely unpredictable for as long as an equation governing such phenomena is unknown or uncomputable. This is in contrast to the paradigm of pseudo-random number generation commonly implemented in computer programs. A hardware random number generator typically consists of a transducer to convert some aspect of the physical phenomena to an electrical signal, an amplifier and other electronic circuitry to increase the amplitude of the random fluctuations to a measurable level, and some type of analog-to-digital converter to convert the output into a digital number, often a simple binary digit 0 or 1. By repeatedly sampling the randomly varying signal, a series of random numbers is obtained. The main application for electronic hardware random number generators is in cryptography, where they are used to generate random cryptographic keys to transmit data securely. They are widely used in Internet encryption protocols such as Transport Layer Security (TLS). Random number generators can also be built from "random" macroscopic processes, using devices such as coin flipping, dice, roulette wheels and lottery machines. The presence of unpredictability in these phenomena is supported by the theory of unstable dynamical systems and chaos theory. Even though macroscopic processes are deterministic under Newtonian mechanics, the output of a well-designed device can be impractical to predict in practice, because it depends on the sensitive, micro-details of the initial conditions of each use. Although dice have been mostly used in gambling, and as "randomizing" elements in games (e.g. role playing games), the Victorian scientist Francis Galton described a way to use dice to explicitly generate random numbers for scientific purposes in 1890. Hardware random number generators generally produce only a limited number of random bits per second. In order to increase the available output data rate, they are often used to generate the "seed" for a faster cryptographically secure pseudorandom number generator, which then generates a pseudorandom output sequence at a much higher data rate. With random number generators based on a noisy classical system or an elementary quantum measurement, assertions of unpredictability should be based on a careful model describing the underlying physics. Yet any such model must make a number of assumptions that may not be valid, and are difficult to verify. But starting in 2010, "Einstein-certified" quantum physics experiments have been able to demonstrate, sometimes even to remote observers, that the bits they produce are unpredictable, requiring only very mild assumptions about signals not being able to travel faster than the speed of light. (Wikipedia).