23C3: Analysis of a strong Random Number Generator
Speaker: Thomas Biege This paper (and slides) will descibe the inner workings of the the random number generator (/dev/{u}random) of Linux. Additionally some possible security flaws are shown (entropy overestimation, zero'izing the pool, etc.) For more information visit: http://bit.ly/
From playlist 23C3: Who can you trust
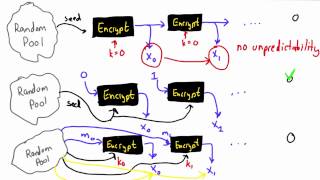
Pseudo Random Number Generator Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Coding Math: Episode 51 - Pseudo Random Number Generators Part I
Back to School Special. This short series will discuss pseudo random number generators (PRNGs), look at how they work, some algorithms for PRNGs, and how they are used. Support Coding Math: http://patreon.com/codingmath Source Code: https://jsbin.com/nifutup/1/edit?js,output Earlier Sourc
From playlist Episodes

Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Randomness Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

How to use the Random Number Generator in Excel
For more articles, how-tos and videos on Excel and statistics, visit us at: http://www.statisticshowto.com
From playlist Excel for Statistics

Biased Generator - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Pseudo Random Number Generator - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Jonathan Katz - Introduction to Cryptography Part 1 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will serve as a "crash course" in modern cryptography for those with no prior exposure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Speakers: djb | Nadia Heninger | Tanja Lange RSA factorization in the real world RSA is the dominant public-key cryptosystem on the Internet. This talk will explain the state of the art in techniques for the attacker to figure out your secret RSA keys. A typical 1024-bit RSA public key
From playlist 29C3: Not my department

Speakers: Henryk Plötz. Karsten Nohl Many RFID tags have weaknesses, but the security level of different tags varies widely. Using the Mifare Classic cards as an example, we illustrate the complexity of RFID systems and discuss different attack vectors. To empower further analysis of RFID
From playlist 25C3: Nothing to hide

Black Hat USA 2010: Understanding the Windows SMB NTLM Weak Nonce Vulnerability 3/5
Speakers: Hernan Ochoa, Agustin Azubel In February 2010, we found a vulnerability in the SMB NTLM Windows Authentication mechanism that have been present in Windows systems for at least 14 years (from Windows NT 4 to Windows Server 2008). You probably haven't heard about this vulnerabilit
From playlist BH USA 2010 - OS WARS

30C3: The Year in Crypto (DE - translated)
For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speakers: Nadia Heninger | djb | Tanja Lange This was a busy year for crypto. TLS was broken. And then broken again. Discrete logs were computed. And then computed again.
From playlist 30C3

Jonathan Katz - Introduction to Cryptography Part 2 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography II" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This session will focus on public-key cryptography, including key exchange, public-key encryption,
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography
Black Hat USA 2010: Understanding the Windows SMB NTLM Weak Nonce Vulnerability 5/5
Speakers: Hernan Ochoa, Agustin Azubel In February 2010, we found a vulnerability in the SMB NTLM Windows Authentication mechanism that have been present in Windows systems for at least 14 years (from Windows NT 4 to Windows Server 2008). You probably haven't heard about this vulnerabilit
From playlist BH USA 2010 - OS WARS

24C3: Mifare (Little Security, Despite Obscurity)
Speakers: Karsten Nohl, Henryk Plötz Mifare are the most widely deployed brand of secure RFID chips, but their security relies on proprietary and secret cryptographic primitives. We analyzed the hardware of the Mifare tags and found weaknesses in several parts of the cipher. For more i
From playlist 24C3: Full steam ahead

Analog vs. Digital Epsilons: Implementation Considerations Considerations for Differential Privacy
A Google TechTalk, presented by Olya Ohrimenko, 2021/11/17 Differential Privacy for ML series.
From playlist Differential Privacy for ML

randomGenerator in Number Puzzles
https://teacher.desmos.com/activitybuilder/custom/61282f1b979758794705a7d6
From playlist Computation Layer

25c3: Predictable RNG in the vulnerable Debian OpenSSL package
Speakers: Luciano Bello, Maximiliano Bertacchini the What and the How Recently, the Debian project announced an OpenSSL package vulnerability which they had been distributing for the last two years. This bug makes the PRNG predictable, affecting the keys generated by openssl and every ot
From playlist 25C3: Nothing to hide