
Deep Dive into PostgresSQL Statistics
PostgreSQL RDBMS is a complex piece of software that comprises many subsystems, and its overall performance depends on these subsystems. For an optimal performance, Postgres collects various statistics and information from these subsystems. This helps Postgres to estimate its effectiveness
From playlist 2016

Reliability 1: External reliability and rater reliability and agreement
In this video, I discuss external reliability, inter- and intra-rater reliability, and rater agreement.
From playlist Reliability analysis

Definition of an Injective Function and Sample Proof
We define what it means for a function to be injective and do a simple proof where we show a specific function is injective. Injective functions are also called one-to-one functions. Useful Math Supplies https://amzn.to/3Y5TGcv My Recording Gear https://amzn.to/3BFvcxp (these are my affil
From playlist Injective, Surjective, and Bijective Functions
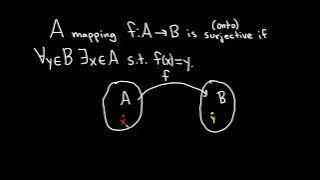
Definition of a Surjective Function and a Function that is NOT Surjective
We define what it means for a function to be surjective and explain the intuition behind the definition. We then do an example where we show a function is not surjective. Surjective functions are also called onto functions. Useful Math Supplies https://amzn.to/3Y5TGcv My Recording Gear ht
From playlist Injective, Surjective, and Bijective Functions

An general explanation of the underactive thyroid.
From playlist For Patients

The idea of ‘atonement’ sounds very old-fashioned and is deeply rooted in religious tradition. To atone means, in essence, to acknowledge one’s capacity for wrongness and one’s readiness for apology and desire for change. It’s a concept that every society needs at its center. For gifts and
From playlist RELATIONSHIPS

TDD Is The Best Design Technique
Test Driven Development is one of the most profound ways to improve the quality of your code. This is not just in the simplistic sense of “we tested it works” but also the way that testing very strongly encourages us, if not forces us, to create testable code, and the hallmarks of testab
From playlist Automated Testing

Which Incapacitating Agent is the Most Effective?
This time, we're ranking incapacitating agents! The term incapacitating agent is defined by the United States Department of Defense as: "An agent that produces temporary physiological or mental effects, or both, which will render individuals incapable of concerted effort in the performance
From playlist Chemistry Tierlists

What Is A GED? MUST WATCH BEFORE YOU TRY TO GET ONE!
GED Math Lessons http://www.gedmathlessons.com this video will explain what is a GED. Many people want to get their GED but do not know the correct process. Also many people have other options such as the HiSET and TASC exams.
From playlist GED Prep Videos

Lesson 10: Deep Learning Foundations to Stable Diffusion, 2022
(All lesson resources are available at http://course.fast.ai.) This lesson creates a complete Diffusers pipeline from the underlying components: the VAE, unet, scheduler, and tokeniser. By putting them together manually, this gives you the flexibility to fully customise every aspect of the
From playlist Practical Deep Learning 2022 Part 2

Totient - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography