Definition of a group Lesson 24
In this video we take our first look at the definition of a group. It is basically a set of elements and the operation defined on them. If this set of elements and the operation defined on them obey the properties of closure and associativity, and if one of the elements is the identity el
From playlist Abstract algebra
This video contains the origins of group theory, the formal definition, and theoretical and real-world examples for those beginning in group theory or wanting a refresher :)
From playlist Summer of Math Exposition Youtube Videos

What is a Group? | Abstract Algebra
Welcome to group theory! In today's lesson we'll be going over the definition of a group. We'll see the four group axioms in action with some examples, and some non-examples as well which violate the axioms and are thus not groups. In a fundamental way, groups are structures built from s
From playlist Abstract Algebra

Group Theory for Physicists (Definitions with Examples)
In this video, we cover the most basic points that a physicist should know about group theory. Along the way, we'll give you lots of examples that illustrate each step. 00:00 Introduction 00:11 Definition of a Group 00:59 (1) Closure 01:34 (2) Associativity 02:02 (3) Identity Element 03:
From playlist Mathematical Physics

Abstract Algebra: We introduce the notion of a group and describe basic properties. Examples given include familiar abelian groups and the symmetric groups. U.Reddit course materials available at http://ureddit.com/class/23794/intro-to-group-theory Master list at http://mathdoctorbob.o
From playlist Abstract Algebra

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Kritin Lauter, Supersingular isogeny graphs in cryptography
VaNTAGe Seminar, September 20, 2022 License: CC-BY-NC-SA Some of the papers mentioned in this talk: Charles, Goren, Lauter 2007: https://doi.org/10.1007/s00145-007-9002-x Mackenzie 2008: https://doi.org/10.1126/science.319.5869.1481 Pizer 1990: https://doi.org/10.1090/S0273-0979-1990-15
From playlist New developments in isogeny-based cryptography
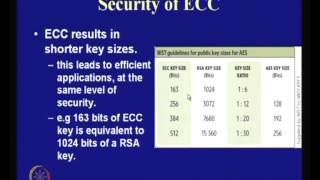
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Math Talk! Mickael Montessinos, Ph.D. student, Elliptic Curve Cryptography
After a break down of Diffe-Hellman key exchange, and post-qunatum cryptography, we explore the journey of becoming a mathematician. Luca De Feo's talk: https://www.youtube.com/watch?v=sSA3OMBBcyQ&ab_channel=TheIACR My Twitter: https://twitter.com/KristapsBalodi3 SIDH (0:00) Getting int
From playlist Math Talk!

Mathematics in Post-Quantum Cryptography - Kristin Lauter
2018 Program for Women and Mathematics Topic: Mathematics in Post-Quantum Cryptography Speaker: Kristin Lauter Affiliation: Microsoft Research Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist My Collaborators

Mathematics in Cryptography II - Toni Bluher
2018 Program for Women and Mathematics Topic: Mathematics in Cryptography II Speaker: Toni Bluher Affiliation: National Security Agency Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

Craig Costello - Post-quantum key exchange from supersingular isogenies- IPAM at UCLA
Recorded 26 July 2022. Craig Costello of Microsoft Research presents "Post-quantum key exchange from supersingular isogenies" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This talk will give an overview of Supersingular isogeny Diffie-Hellman (SIDH): t
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

A brief description of the "Basic Principle" and how it can be used to test for primality.
From playlist Cryptography and Coding Theory

Kirsten Eisentraeger - Classical and quantum algorithms for isogeny problems - IPAM at UCLA
Recorded 26 January 2022. Kirsten Eisentraeger of Pennsylvania State University presents "Classical and quantum algorithms for isogeny problems" at IPAM's Quantum Numerical Linear Algebra Workshop. Abstract: Isogeny-based cryptography is one of a few candidates for post-quantum cryptograph
From playlist Quantum Numerical Linear Algebra - Jan. 24 - 27, 2022

Cybersecurity Tutorial | Demo On Man In The Middle Attack | Cybersecurity Training | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl This "Cybersecurity tutorial" video presented by edureka gives an indepth information about the Cyber Security world and talks about its basic concepts.
From playlist Cyber Security Training for Beginners | Edureka

Group Definition (expanded) - Abstract Algebra
The group is the most fundamental object you will study in abstract algebra. Groups generalize a wide variety of mathematical sets: the integers, symmetries of shapes, modular arithmetic, NxM matrices, and much more. After learning about groups in detail, you will then be ready to contin
From playlist Abstract Algebra
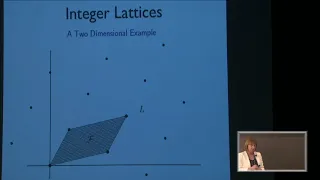
Mathematical Ideas in Lattice Based Cryptography - Jill Pipher
2018 Program for Women and Mathematics Topic: Mathematical Ideas in Lattice Based Cryptography Speaker: Jill Pipher Affiliation: Brown University Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain
