
An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography
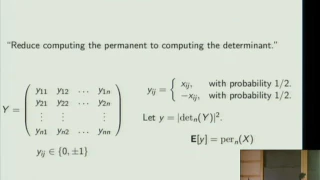
The Complexity of the Non-commutative Determinant - Srikanth Srinivasan
The Complexity of the Non-commutative Determinant Srikanth Srinivasan Institute for Advanced Study October 11, 2010 I will talk about the computational complexity of computing the noncommutative determinant. In contrast to the case of commutative algebras, we know of (virtually) no efficie
From playlist Mathematics

Commutative algebra 2 (Rings, ideals, modules)
This lecture is part of an online course on commutative algebra, following the book "Commutative algebra with a view toward algebraic geometry" by David Eisenbud. This lecture is a review of rings, ideals, and modules, where we give a few examples of non-commutative rings and rings without
From playlist Commutative algebra

This video gives a general introduction to cryptography WITHOUT actually doing any math. Terms covered include cryptology vs cryptography vs cryptanalysis, symmetric vs public key systems, and "coding theory." NOTE: Yes, I said and wrote "cryptOanalysis" when it's actually "cryptanalysis
From playlist Cryptography and Coding Theory

Secure Computation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Axel de Goursac: Noncommutative Supergeometry and Quantum Field Theory
In this talk, we present the philosophy and the basic concepts of Noncommutative Supergeometry, i.e. Hilbert superspaces, C*-superalgebras and quantum supergroups. Then, we give examples of these structures coming from deformation quantization and we expose an application to renormalizable
From playlist HIM Lectures: Trimester Program "Non-commutative Geometry and its Applications"

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Non-commutative arithmetic computation - Avi Wigderson
Avi Wigderson Institute for Advanced Study; Faculty, School of Mathematics February 11, 2014 I will survey what is known about the complexity of arithmetic circuits computing polynomials and rational functions with non-commuting variables, focusing on recent results and open problems. Stra
From playlist Mathematics

Kirsten Eisentraeger - Classical and quantum algorithms for isogeny problems - IPAM at UCLA
Recorded 26 January 2022. Kirsten Eisentraeger of Pennsylvania State University presents "Classical and quantum algorithms for isogeny problems" at IPAM's Quantum Numerical Linear Algebra Workshop. Abstract: Isogeny-based cryptography is one of a few candidates for post-quantum cryptograph
From playlist Quantum Numerical Linear Algebra - Jan. 24 - 27, 2022

Anne Broadbent - Information-Theoretic Quantum Cryptography Part 2 of 2 - IPAM at UCLA
Recorded 27 July 2022. Anne Broadbent of the University of Ottawa presents "Information-Theoretic Quantum Cryptography" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: These lectures are an introduction to the interplay between quantum information and cryp
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Mathematics in Cryptography II - Toni Bluher
2018 Program for Women and Mathematics Topic: Mathematics in Cryptography II Speaker: Toni Bluher Affiliation: National Security Agency Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Mathematics in Post-Quantum Cryptography II - Kristin Lauter
2018 Program for Women and Mathematics Topic: Mathematics in Post-Quantum Cryptography II Speaker: Kristin Lauter Affiliation: Microsoft Research Date: May 22, 2018 For more videos, please visit http://video.ias.edu
From playlist My Collaborators

Avi Wigderson & László Lovász - The Abel Prize interview 2021
00:30 Interview start 01:03 On the place of discrete math and theoretical computer science 08:14 Turing and Hilbert 14:28 P vs NP problem, what is it and why is it important? 25:09 Youth in Haifa, Avi Wigderson 30:09 Youth in Budapest, László Lovász 37:45 Problem solver or theory builde
From playlist László Lovász
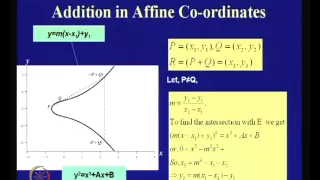
An Introduction to Elliptic Curve Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Elliptic Curves: Good books to get started
A few books for getting started in the subject of Elliptic Curves, each with a different perspective. I give detailed overviews and my personal take on each book. 0:00 Intro 0:41 McKean and Moll, Elliptic Curves: Function Theory, Geometry, Arithmetic 10:14 Silverman, The Arithmetic of El
From playlist Math

The Value of Errors in Proofs - Avi Wigderson
Members’ Seminar Topic: The Value of Errors in Proofs Speaker: Avi Wigderson Affiliation: Herbert H. Maass Professor, School of Mathematics Date: March 01, 2021 For more video please visit http://video.ias.edu
From playlist Mathematics

Math Talk! Mickael Montessinos, Ph.D. student, Elliptic Curve Cryptography
After a break down of Diffe-Hellman key exchange, and post-qunatum cryptography, we explore the journey of becoming a mathematician. Luca De Feo's talk: https://www.youtube.com/watch?v=sSA3OMBBcyQ&ab_channel=TheIACR My Twitter: https://twitter.com/KristapsBalodi3 SIDH (0:00) Getting int
From playlist Math Talk!

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain

Craig Costello - Post-quantum key exchange from supersingular isogenies- IPAM at UCLA
Recorded 26 July 2022. Craig Costello of Microsoft Research presents "Post-quantum key exchange from supersingular isogenies" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This talk will give an overview of Supersingular isogeny Diffie-Hellman (SIDH): t
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography
