
Trig identities and partial fraction decomposition. New math videos every Wednesday. Subscribe to make sure you see them!
From playlist Integrals
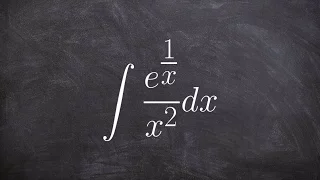
How to integrate exponential expression with u substitution
👉 Learn how to evaluate the integral of a function. The integral, also called antiderivative, of a function, is the reverse process of differentiation. Integral of a function can be evaluated as an indefinite integral or as a definite integral. A definite integral is an integral in which t
From playlist The Integral

Apply u substitution to a polynomial
👉 Learn how to evaluate the integral of a function. The integral, also called antiderivative, of a function, is the reverse process of differentiation. Integral of a function can be evaluated as an indefinite integral or as a definite integral. A definite integral is an integral in which t
From playlist The Integral

Overview on Modern Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Dirichlet Eta Function - Integral Representation
Today, we use an integral to derive one of the integral representations for the Dirichlet eta function. This representation is very similar to the Riemann zeta function, which explains why their respective infinite series definition is quite similar (with the eta function being an alte rna
From playlist Integrals

How to use u substitution to find the indifinite integral
👉 Learn how to evaluate the integral of a function. The integral, also called antiderivative, of a function, is the reverse process of differentiation. Integral of a function can be evaluated as an indefinite integral or as a definite integral. A definite integral is an integral in which t
From playlist The Integral
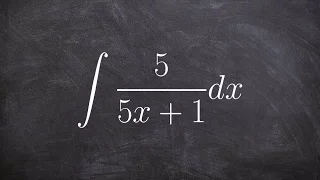
Integrate the a rational expression using logarithms and u substitution
👉 Learn how to evaluate the integral of a function. The integral, also called antiderivative, of a function, is the reverse process of differentiation. Integral of a function can be evaluated as an indefinite integral or as a definite integral. A definite integral is an integral in which t
From playlist The Integral

Types of Cryptography Algorithms | Cryptography in Network Security | Edureka | Cybersecurity Live-2
🔥Edureka Cybersecurity Online Training: https://www.edureka.co/cybersecurity-certification-training This Edureka video on Cryptography Algorithms Explained talks about the various algorithms used for cryptography and how they help in making our data secure. Cybersecurity Training Playlist
From playlist Edureka Live Classes 2020

Learn how to use u substitution to integrate a polynomial
👉 Learn how to evaluate the integral of a function. The integral, also called antiderivative, of a function, is the reverse process of differentiation. Integral of a function can be evaluated as an indefinite integral or as a definite integral. A definite integral is an integral in which t
From playlist The Integral

Cryptanalysis of Vigenere cipher: not just how, but why it works
The Vigenere cipher, dating from the 1500's, was still used during the US civil war. We introduce the cipher and explain a standard method of cryptanalysis based on frequency analysis and the geometry of vectors. We focus on visual intuition to explain why it works. The only background
From playlist Classical Cryptography

CS105: Introduction to Computers | 2021 | Lecture 20.2 Computer Security: Mechanisms
Patrick Young Computer Science, PhD This course is a survey of Internet technology and the basics of computer hardware. You will learn what computers are and how they work and gain practical experience in the development of websites and an introduction to programming. To follow along wi
From playlist Stanford CS105 - Introduction to Computers Full Course

What is an integral and it's parts
👉 Learn about integration. The integral, also called antiderivative, of a function, is the reverse process of differentiation. Integral of a function can be evaluated as an indefinite integral or as a definite integral. A definite integral is an integral in which the upper and the lower li
From playlist The Integral

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Ethical Hacking Tutorial For Beginners | Ethical Hacking Course | Ethical Hacking Training | Edureka
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training 🔵 Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN This Edureka "Ethical Hacking Tutorial" video will give you an introduction to Ethical Hacking. This video will give you an exhaustiv
From playlist Cyber Security Training for Beginners | Edureka

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

How to find the integral of an exponential function using u sub
👉 Learn how to evaluate the integral of a function. The integral, also called antiderivative, of a function, is the reverse process of differentiation. Integral of a function can be evaluated as an indefinite integral or as a definite integral. A definite integral is an integral in which t
From playlist The Integral

Colossus - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Bitcoin Q&A: Migrating to Post-Quantum Cryptography
Keywords/phrases: Quantum cryptography, quantum cryptoanalysis, quantum computing. Bitcoin uses SHA-256. In cryptography there is a 20-30 year lifecycle for an algorithm before it gets exceeded by new technologies and developments in mathematics. Both the signing and hashing algorithms can
From playlist English Subtitles - aantonop Videos with subtitles in English

How to find the integral with a radical
👉 Learn how to evaluate the integral of a function. The integral, also called antiderivative, of a function, is the reverse process of differentiation. Integral of a function can be evaluated as an indefinite integral or as a definite integral. A definite integral is an integral in which t
From playlist The Integral