
Indistinguishability obfuscation from...to jumping pigs - Nir Bitansky
Indistinguishability obfuscation has turned out to be an outstanding notion with strong implications not only to cryptography, but also other areas such as complexity theory, and differential privacy. Nevertheless, our understanding of how to construct indistinguishability obfuscators is s
From playlist Mathematics

Indistinguishability Obfuscation from Well-Founded Assumptions - Huijia (Rachel) Lin
Computer Science/Discrete Mathematics Seminar I Topic: Indistinguishability Obfuscation from Well-Founded Assumptions Speaker: Huijia (Rachel) Lin Affiliation: University of Washington Date: November 16, 2020 For more video please visit http://video.ias.edu
From playlist Mathematics

Toy Ind3 - Part 02 - Indeterminacy Diagrams
This is terminology introduced to clarify the part of what goes on in IUT3. This isn't really in the body and Mochizuki may view this as implicit. We give an abstract definition of what an indeterminacy diagram is. We will apply this to the Log-Kummer correspondence. Errata: *The maps g
From playlist Toy Ind3

Linear Inequalities in Two Variables
http://mathispower4u.wordpress.com/
From playlist Linear and Absolute Value Inequalities

CERIAS Security: Obfuscated Databases: Definitions and Constructions 4/6
Clip 4/6 Speaker: Vitaly Shmatikov · University of Texas at Austin I will present some new definitions and constructions for privacy in large databases. In contrast to conventional privacy mechanisms that aim to prevent any access to individual records, our techniques are designed to
From playlist The CERIAS Security Seminars 2005 (1)
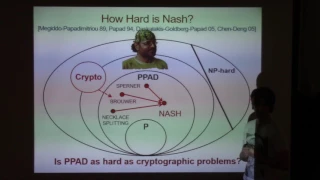
On the cryptographic hardness of finding a Nash equilibrium - Nir Bitansky
The computational complexity of finding Nash Equilibria in games has received much attention over the past two decades due to its theoretical and philosophical significance. This talk will be centered around the connection between this problem and cryptography. Mostly, I will discuss a res
From playlist Mathematics

Another, perhaps better, method of solving for a higher-order, linear, nonhomogeneous differential equation with constant coefficients. In essence, some form of differentiation is performed on both sides of the equation, annihilating the right-hand side (to zero), so as to change it into
From playlist Differential Equations

CERIAS Security: Obfuscated Databases: Definitions and Constructions 3/6
Clip 3/6 Speaker: Vitaly Shmatikov · University of Texas at Austin I will present some new definitions and constructions for privacy in large databases. In contrast to conventional privacy mechanisms that aim to prevent any access to individual records, our techniques are designed to
From playlist The CERIAS Security Seminars 2005 (1)

Method of Undetermined Coefficients
We demonstrate how to solve 2nd order, linear, inhomogeneous differential equations with the Method of Undetermined Coefficients.
From playlist Mathematical Physics I Uploads

CERIAS Security: Obfuscated Databases: Definitions and Constructions 1/6
Clip 1/6 Speaker: Vitaly Shmatikov · University of Texas at Austin I will present some new definitions and constructions for privacy in large databases. In contrast to conventional privacy mechanisms that aim to prevent any access to individual records, our techniques are designed to
From playlist The CERIAS Security Seminars 2005 (1)

CERIAS Security: Obfuscated Databases: Definitions and Constructions 5/6
Clip 5/6 Speaker: Vitaly Shmatikov · University of Texas at Austin I will present some new definitions and constructions for privacy in large databases. In contrast to conventional privacy mechanisms that aim to prevent any access to individual records, our techniques are designed to
From playlist The CERIAS Security Seminars 2005 (1)

Solving Equations Using Multiplication or Division
This video is about Solving Equations with Multiplication and Division
From playlist Equations and Inequalities

Bitcoin Q&A: Will Governments Let Privacy Coins Exist?
On the benefits and challenges with upcoming privacy improvements to Bitcoin. What do you think about Snowden's comments on privacy in Bitcoin and open public blockchains? What are unspent transaction outputs (UTXOs)? Can you re-anonymise UTXOs from KYC exchanges like Coinbase, by particip
From playlist Privacy and Surveillance

CERIAS Security: Obfuscated Databases: Definitions and Constructions 2/6
Clip 2/6 Speaker: Vitaly Shmatikov · University of Texas at Austin I will present some new definitions and constructions for privacy in large databases. In contrast to conventional privacy mechanisms that aim to prevent any access to individual records, our techniques are designed to
From playlist The CERIAS Security Seminars 2005 (1)
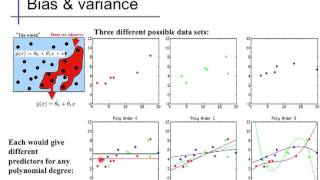
Linear regression (5): Bias and variance
Inductive bias; variance; relationship to over- & under-fitting
From playlist cs273a

CERIAS Security: Obfuscated Databases: Definitions and Constructions 6/6
Clip 6/6 Speaker: Vitaly Shmatikov · University of Texas at Austin I will present some new definitions and constructions for privacy in large databases. In contrast to conventional privacy mechanisms that aim to prevent any access to individual records, our techniques are designed to
From playlist The CERIAS Security Seminars 2005 (1)
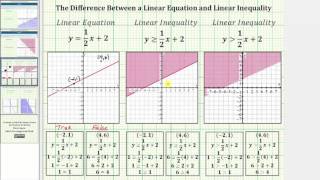
The Difference Between a Linear Equation and Linear Inequality (Two Variables)
This video explains the difference between a linear equation and linear inequality in two variables.
From playlist Solving Linear Inequalities in Two Variables

Brucon 2009: A new web attack vector: Script Fragmentation 1/6
Clip 1/6 Speaker: Stephan Chenette Abstract: This presentation will introduce a new web-based attack vector which utilizes client-side scripting to fragment malicious web content. This involves distributing web exploits in a asynchronous manner to evade signature detection. Similar
From playlist Brucon 2009