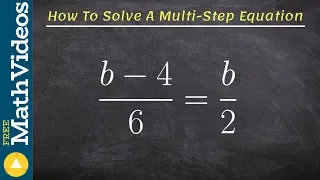
How to solve a multi step equation with rational terms - (b-4)/6 = b/2
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides

Solving an equation with variables on both side and one solution
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist Solve Multi-Step Equations......Help!
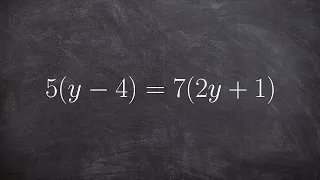
Solving an equation with distributive property on both sides
👉 Learn how to solve multi-step equations with parenthesis and variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To
From playlist Solve Multi-Step Equations......Help!
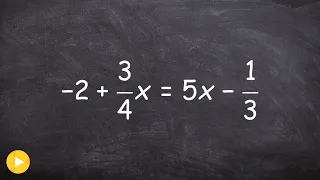
Solve an equation for x by clearing fractions with multiple steps
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides
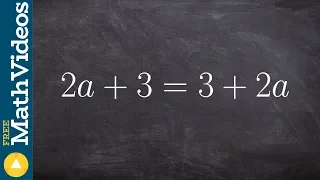
Solving an equation with infinite many solutions 2a+3=3+2a
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides
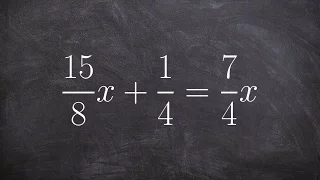
Solving an equation with fraction where your variable is on both sides
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides
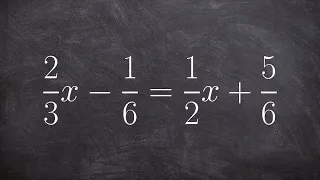
Solving a multi-step equation with fractions and variable on both sides
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides
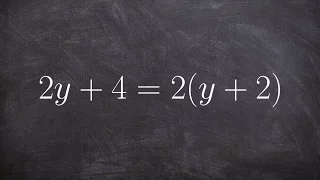
Solving an equation with a variable on both sides infinite solutions
👉 Learn how to solve multi-step equations with parenthesis and variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To
From playlist Solve Multi-Step Equations......Help!

Trusted CI Webinar: Trustworthy Computing for Scientific Workflows w/ Mayank Varia & Andrei Lapets
Originally recorded on July 23, 2018 There has been an unprecedented increase in the quantity of research data available in digital form. Combining these information sources within analyses that leverage cloud computing frameworks and big data analytics platforms has the potential to lead
From playlist Center for Applied Cybersecurity Research (CACR)

With a variable on both sides solving a multi step equation two ways
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides

De-Identification 201: Secure MPC Webinar
On February 12th, 2018, FPF held a special webinar on De-Identification 201: Secure Multi-Party Computation, with experts Mayank Varis, Andrei Lapets, and Frederick Jansen from Boston University, Laura Berntsen, Domestic Policy Advisor at the Senate Finance Committee, and moderator Michael
From playlist Center for Applied Cybersecurity Research (CACR)

Nexus Trimester - Yuval Ishai (Technion) 1/2
Secure Multiparty Computation - 1/2 Yuval Ishai (Technion) March 28, 2016 Abstract: Secure multiparty computation allows two or more parties to perform a distributed computation on their local inputs while hiding the inputs from each other. This part of the minicourse will give a broad o
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

Some Secure Computation concepts by Manoj Prabhakaran
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

MPC in the Head With Applications to Blockchain (Lecture 2) by Carmit Hazay
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

IMT4306 Mobile Research: Privacy and Anonymity
IMT4306 Introduction to Research in Mobile Decentralised systems, privacy, anonymity, privacy techniques.
From playlist 2021 - IMT4306 - Mobile Research

633: Responsible Decentralized Intelligence — with Dawn Song
#DecentralizedIntelligence #DifferentialPrivacy #PrivateSQL This week's episode is all about Responsible Decentralized Intelligence as award-winning professor and tech entrepreneur, Dawn Song, joins @JonKrohnLearns to help us explore this exciting topic in-depth. This episode is brought
From playlist Super Data Science Podcast

Breaking the Circuit-Size Barrier in Secret Sharing - Vinod Vaikuntanathan
Computer Science/Discrete Mathematics Seminar I Topic: Breaking the Circuit-Size Barrier in Secret Sharing Speaker: Vinod Vaikuntanathan Affiliation: MIT Date: October 15, 2018 For more video please visit http://video.ias.edu
From playlist Mathematics

CERIAS Security: Applying Recreational Mathematics to Secure Multiparty Computation 1/5
Clip 1/5 Speaker: Yvo Desmedt · University College, London The problem of a mice traveling through a maze is well known. The maze can be represented using a planar graph. We present a variant of the maze. We consider a grid vertex colored planar graph in which an adversary can choose
From playlist The CERIAS Security Seminars 2007

Solving Private Set Intersection via Cuckoo Hashing: Benny Pinkas, Bar-Ilan University, Israel
Private set intersection (PSI) allows two parties to compute the intersection of their sets without revealing any information about items that are not in the intersection. There has been considerable research on designing custom secure protocols for computing PSI, due to the fact that PSI
From playlist Turing Seminars
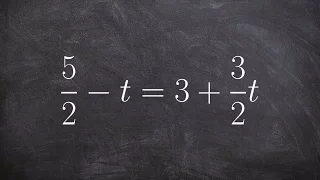
Solving a multi-step equation by multiplying by the denominator
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides