
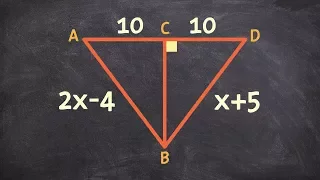
Using Two Congruent Triangles to Find the Value of X and Y
👉 Learn how to solve for unknown variables in congruent triangles. Two or more triangles are said to be congruent if they have the same shape and size. When one of the values of a pair of congruent sides or angles is unknown and the other value is known or can be easily obtained, then the
From playlist Congruent Triangles
Using Congruent Triangles to Determine the Value of X
👉 Learn how to solve for unknown variables in congruent triangles. Two or more triangles are said to be congruent if they have the same shape and size. When one of the values of a pair of congruent sides or angles is unknown and the other value is known or can be easily obtained, then the
From playlist Congruent Triangles

Determine the Value of your Variables with Congruent Triangles
👉 Learn how to solve for unknown variables in congruent triangles. Two or more triangles are said to be congruent if they have the same shape and size. When one of the values of a pair of congruent sides or angles is unknown and the other value is known or can be easily obtained, then the
From playlist Congruent Triangles

Learning to Find the Value of X and Y from Congruent Triangles
👉 Learn how to solve for unknown variables in congruent triangles. Two or more triangles are said to be congruent if they have the same shape and size. When one of the values of a pair of congruent sides or angles is unknown and the other value is known or can be easily obtained, then the
From playlist Congruent Triangles

Vernier caliper / diameter and length of daily used objects.
subscribe to my channel: https://www.youtube.com/channel/UC7HtImwPgmb1axsTJE5lxeA?sub_confirmation=1
From playlist Fine Measurements

How to Determine X and Y Using Congruent Triangles
👉 Learn how to solve for unknown variables in congruent triangles. Two or more triangles are said to be congruent if they have the same shape and size. When one of the values of a pair of congruent sides or angles is unknown and the other value is known or can be easily obtained, then the
From playlist Congruent Triangles

Determine the the Values of X and Y Using Congurent Triangles
👉 Learn how to solve for unknown variables in congruent triangles. Two or more triangles are said to be congruent if they have the same shape and size. When one of the values of a pair of congruent sides or angles is unknown and the other value is known or can be easily obtained, then the
From playlist Congruent Triangles
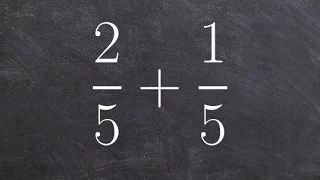
Adding fractions with like denominators - math homework answers
👉 Learn how to add or subtract fractions with common denominators. When adding or subtracting two or more fractions with common denominators, we add or subtract only the numerator while we keep the denominator the same. We will then simplify our answer by reducing the fraction if necessar
From playlist Add and Subtract Fractions with Like Denominators

Barry Sanders: Spacetime replication of continuous-variable quantum information
Abstract: Combining the relativistic speed limit on transmitting information with linearity and unitarity of quantum mechanics leads to a relativistic extension of the no-cloning principle called spacetime replication of quantum information. We introduce continuous-variable spacetime-repli
From playlist Mathematical Physics

MPC in the Head With Applications to Blockchain (Lecture 1) by Carmit Hazay
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

Stream archive: Todo API with Rust + Axum (2022-09-01)
Broadcasted live on Twitch -- Watch live at https://www.twitch.tv/brookzerker
From playlist Uncut Live Streams

Zero Knowledge Proofs - Seminar 8 - Completing the story of ZKSNARKS
This seminar series is about the mathematical foundations of cryptography. In this series Eleanor McMurtry is explaining Zero Knowledge Proofs (ZKPs). Last time Eleanor covered SNARKS, Succinct Non-interactive ARgument of Knowledge. Today this is extended to include: - Zero-knowledge - Ho
From playlist Metauni

Mathematics in Cryptography II - Toni Bluher
2018 Program for Women and Mathematics Topic: Mathematics in Cryptography II Speaker: Toni Bluher Affiliation: National Security Agency Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

OWASP AppSec EU 2013: Improving the Security of Session Management in Web Applications
For more information and to download the video visit: http://bit.ly/appseceu13 Playlist OWASP AppSec EU 2013: http://bit.ly/plappseceu13 Speakers: Lieven Desmet | Wouter Joosen | Frank Piessens | Philippe De Ryck Session management is a critical component of modern web applications, allo
From playlist OWASP AppSec EU 2013

How Do Computers Tell Secrets?
This video explores the beginnings of public key cryptography, through the Merkle's Puzzles formulation of a means to generate a secret on a communication channel with an eavesdropper. Ralph Merkel's Paper: http://www.ralphmerkle.com/1974/PuzzlesAsPublished.pdf #SoME2 #cryptography #com
From playlist Summer of Math Exposition 2 videos

Presented by WWCode Blockchain Speaker: Swetha Srinivasan, Google This talk will give an overview of introductory concepts in security such as confidentiality, integrity, availability, authentication and authorization. It will cover how cryptography is used in real world systems and funda
From playlist Center for Applied Cybersecurity Research (CACR)

Learn how to reflect a triangle over the y axis ex 2
👉 Learn how to solve for unknown variables in congruent triangles. Two or more triangles are said to be congruent if they have the same shape and size. When one of the values of a pair of congruent sides or angles is unknown and the other value is known or can be easily obtained, then the
From playlist Congruent Triangles

RailsConf 2017: Portable Sessions with JSON Web Tokens by Lance Ivy
RailsConf 2017: Portable Sessions with JSON Web Tokens by Lance Ivy Ever wonder why applications use sessions and APIs use tokens? Must there really be a difference? JSON Web Tokens are an emerging standard for portable secure messages. We'll talk briefly about how they're built and how t
From playlist RailsConf 2017

Cyber Security Week Day - 1 |Cryptography Full Course | Cryptography & Network Security| Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity-bootcamp This video on Cryptography full course will acquaint you with cryptograph
From playlist Simplilearn Live
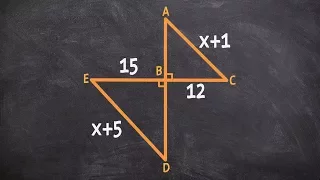
Using Similarity and proportions to find the missing values
👉 Learn how to solve with similar triangles. Two triangles are said to be similar if the corresponding angles are congruent (equal). Note that two triangles are similar does not imply that the length of the sides are equal but the sides are proportional. Knowledge of the length of the side
From playlist Similar Triangles