
Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

What is the definition of domain of a relation
👉 Learn about every thing you need to know to understand the domain and range of functions. We will look at functions represented as equations, tables, mapping, and ordered pairs. The domain is the set of all possible x or input values where the range is the set of all possible y or outp
From playlist What is the Domain and Range of the Function
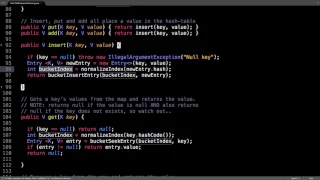
Hash table separate chaining source code
Related Videos: Hash table intro/hash function: https://www.youtube.com/watch?v=2E54GqF0H4s Hash table separate chaining: https://www.youtube.com/watch?v=T9gct6Dx-jo Hash table separate chaining code: https://www.youtube.com/watch?v=Av9kwXkuQFw Hash table open addressing: https://www.youtu
From playlist Data structures playlist

The best explanation of domain and range with multiple examples
👉 Learn about every thing you need to know to understand the domain and range of functions. We will look at functions represented as equations, tables, mapping, and ordered pairs. The domain is the set of all possible x or input values where the range is the set of all possible y or outp
From playlist What is the Domain and Range of the Function

What is the definition of a function
👉 Learn about every thing you need to know to understand the domain and range of functions. We will look at functions represented as equations, tables, mapping, and ordered pairs. The domain is the set of all possible x or input values where the range is the set of all possible y or outp
From playlist What is the Domain and Range of the Function

Zero to Hero: Week 8 - Building an AD Lab, LLMNR Poisoning, and NTLMv2 Cracking with Hashcat
Zero to Hero: 0:00 - Welcome 2:37 - Lesson overview 5:00 - Downloading our ISOs 6:35 - Installing Windows Server 2016 and Windows 10 16:30 - Renaming Windows Server 2016 19:00 - Installing VMWare Tools on Server 2016 21:15 - Finishing Windows 10 install 24:20 - Installing Active Directory
From playlist Zero to Hero: A Practical Network Penetration Testing Course

Most companies have moved into the cloud and on-premises applications and systems remain. This configuration is reasonably referred to as "hybrid"; in the cloud and not at the same time. Hybrid cloud requires integration and communication between the remaining on-prem infrastructure and th
From playlist Security

Dominique Unruh - The quantum random oracle model Part 1 of 2 - IPAM at UCLA
Recorded 28 July 2022. Dominique Unruh of Tartu State University presents "The quantum random oracle model I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: The random oracle is a popular heuristic in classical security proofs that allows us to construct
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Zero to Hero: Week 9 - NTLM Relay, Token Impersonation, Pass the Hash, PsExec, and more
Zero to Hero: 0:00 - Welcome 2:00 - Week overview and additional AD resources 22:52 - Additional lab buildout 32:50 - Loading Metasploit's psexec 34:00 - Sidetrack -- Using CrackMapExec 38:10 - Getting a shell with psexec 41:10 - Fun with Meterpreter pt 1 47:25 - Token Impersonation with I
From playlist Zero to Hero: A Practical Network Penetration Testing Course

DEFCON 20: Cryptohaze Cloud Cracking
Speaker: BITWEASIL LEAD DEVELOPER, CRYPTOHAZE TOOLS Bitweasil goes through the latest developments in the Cryptohaze GPU based password cracking suite. WebTables is a new rainbow table technology that eliminates the need to download rainbow tables before using them, and the new Cryptohaze
From playlist DEFCON 20

Password Exploitation Class: Part 3: Windows LM and NTLM hash cracking 2/5
Clip 2/5 Credits: irongeek.com This is a class we gave for the Kentuckiana ISSA on the the subject of password exploitation. The Password Exploitation Class was put on as a charity event for the Matthew Shoemaker Memorial Fund ( http://www.shoecon.org/ ). The speakers were Dakykilla,
From playlist Password Exploitation Class

BEST explanation how to determine domain algebraically
👉 Learn about every thing you need to know to understand the domain and range of functions. We will look at functions represented as equations, tables, mapping, and ordered pairs. The domain is the set of all possible x or input values where the range is the set of all possible y or outp
From playlist What is the Domain and Range of the Function

Hacking Live Stream: Episode 2 - HackTheBox Active, Vulnserver Buffer Overflow, and Career Q&A / AMA
❓Info❓ ___________________________________________ Need a Pentest?: https://tcm-sec.com Learn to Hack: https://academy.tcm-sec.com 🔹The Cyber Mentor Merch🔹 ___________________________________________ https://teespring.com/stores/the-cyber-mentor 📱Social Media📱 ___________________________
From playlist Hacking Live Streams

Find and Sketch the Domain of the Square Root Function f(x, y) = sqrt(x + y)
Find and Sketch the Domain of the Function f(x, y) = sqrt(x + y). Note the domain will be a subset of R^2 in this case because the domain is a set of ordered pairs. If you enjoyed this video please consider liking, sharing, and subscribing. Udemy Courses Via My Website: https://mathsorce
From playlist Domain of Multivariable Functions

Writing a DSL (Domain Specific Language) for PowerShell by Kevin Marquette
Writing a DSL (Domain Specific Language) for PowerShell by Kevin Marquette Creating a Domain Specific Language can often address specific problem domains better then generic coding or scripting alone. Join me as I break down what it takes to create a DSL in Powershell and show you how to
From playlist PowerShell + DevOps Global Summit 2018

DEFCON 20: Owned in 60 Seconds: From Network Guest to Windows Domain Admin
Speaker: ZACK FASEL Their systems were fully patched, their security team watching, and the amateur pentesters just delivered their "compliant" report. They thought their Windows domain was secure. They thought wrong. Zack Fasel (played by none other than Angelina Jolie) brings a New Too
From playlist DEFCON 20

Polynomial Functions: Domain and Range
How to find the domain and range for any polynomial function with a simple flowchart.
From playlist Domain and Range of Functions

DEFCON 20: Owned in 60 Seconds: From Network Guest to Windows Domain Admin
Speaker: ZACK FASEL Their systems were fully patched, their security team watching, and the amateur pentesters just delivered their "compliant" report. They thought their Windows domain was secure. They thought wrong. Zack Fasel (played by none other than Angelina Jolie) brings a New Too
From playlist DEFCON 20

