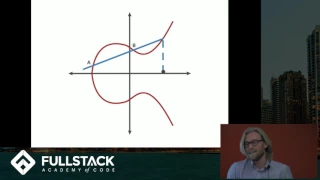
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Learn more advanced front-end and full-stack development at: https://www.fullstackacademy.com Elliptic Curve Cryptography (ECC) is a type of public key cryptography that relies on the math of both elliptic curves as well as number theory. This technique can be used to create smaller, fast
From playlist Elliptic Curves - Number Theory and Applications

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

PortLand: Scaling Data Center Networks to 100,000 Ports and Beyond
(November 18, 2009) Amin Vahdat, a professor of Computer Science and Engineering at the University of California-San Diego, discusses PortLand, a scalable, fault tolerant layer 2 routing and forwarding protocol for data centers, and places the work in the context of his larger efforts in d
From playlist Engineering

ShmooCon 2014: How to Train your Snapdragon: Exploring Power Frameworks on Android
For more information visit: http://bit.ly/shmooc14 To download the video visit: http://bit.ly/shmooc14_down Playlist Shmoocon 2014: http://bit.ly/shmooc14_pl Speaker: Josh "m0nk" Thomas Have you ever wondered how power is routed around your phone, how it is stored and if it could be made
From playlist ShmooCon 2014

Message Authentication Codes: Part 1
Message Authentication MACs based on Hash Functions: HMAC MACs based on Block Ciphers: DAA and CMAC Authenticated Encryption: CCM and GCM Pseudorandom Number Generation Using Hash Functions and MACs
From playlist Network Security

Public key cryptography - Diffie-Hellman Key Exchange (full version)
The history behind public key cryptography & the Diffie-Hellman key exchange algorithm. We also have a video on RSA here: https://www.youtube.com/watch?v=wXB-V_Keiu8
From playlist Cryptography, Security

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Totient - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Network Security, Part 2 : Public Key Encryption
Fundamental concepts of public key encryption are discussed. RSA encryption method explained with an example. Confidentiality of message is presented.
From playlist Cryptography, Security

Adventures in Customizing KDE Plasma to Look like MacOS Big Sur
Matt goes through the process of making KDE Plasma look like MacOS Big Sur. He's mostly successful. Link to the instructions I used ---- https://pastebin.com/2vZx3qZR Special Thanks to our first patron, Devon C for making this episode possible! -----💲💲 Support the Show 💲💲-- http://p
From playlist Ricing

Cryptography Course 🔥FREE | Cryptography Lecture | Cryptography Course Online Free | Simplilearn
🔥Enroll for Cryptography Course & Get Your Completion Certificate: https://www.simplilearn.com/learn-cryptography-basics-free-skillup-course?utm_campaign=CryptographySkillupIntro&utm_medium=Description&utm_source=youtube ✅Subscribe to our Channel to learn more about the top Technologies:
From playlist Cyber Security Playlist [2023 Updated]🔥

Symmetric Key Cryptography And Asymmetric Key Cryptography | Cryptography Tutorial | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=SymmetricKeyCryptographyAndAsymmetricKeyCryptography&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.sim
From playlist Cyber Security Playlist [2023 Updated]🔥

Symmetric Key Cryptography | Stream Cipher & Block Cipher Explained | Network Security | Simplilearn
This video on Symmetric Key Cryptography will acquaint you with the process of symmetric encryption and decryption. Here, we take a small recap into cryptography, the working and applications of symmetric key cryptography, and its advantages. We also have stream cipher and block cipher exp
From playlist Cyber Security Playlist [2023 Updated]🔥

Asymmetric Key Cryptography | RSA Encryption Algorithm | Asymmetric Encryption | Simplilearn
In this video on Asymmetric Key Cryptography, we learn the ins & outs of asymmetric encryption and decryption. From learning the importance of asymmetric encryption to its applications, advantages and workflow, we cover all the bases and also take a look at why it's called public key crypt
From playlist Cyber Security Playlist [2023 Updated]🔥

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
What is Cryptography? | Introduction to Cryptography | Cryptography for Beginners | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl Cryptography is essential to protect the information shared across the internet. This video on What is cryptography explaines you the fundamental concep
From playlist Cyber Security Training for Beginners | Edureka

What Is Cryptography? | Introduction To Cryptography | Cryptography Tutorial | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=WhatisCryptography&-rjWx39mB4Scutm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecu
From playlist Cyber Security Playlist [2023 Updated]🔥

Public Key Cryptography & RSA: Part 2
Fundamental concepts of Prime Numbers are discussed. Optimization of Private Key operations is presented. RSA Security is Analyzed.
From playlist Network Security

Cryptography is fascinating because of the close ties it forges between theory and practice. It makes use of bitwise computations, advanced algebra, string operations and everything in between. Explaining cryptography requires not only showing the math behind it, but also tying it to real-
From playlist Wolfram Technology Conference 2021
