
Thwarting Guessing - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

What Could Go Wrong Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Weak Ciphers - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Correctness And Security - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Perfect Cipher - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Convincing Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Random Oracle - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

OWASP AppSec EU 2013: A Perfect CRIME? Only time will tell
For more information and to download the video visit: http://bit.ly/appseceu13 Playlist OWASP AppSec EU 2013: http://bit.ly/plappseceu13 Speaker: Tal Be'Ery In 2012, security researchers shook the world of security with their CRIME attack against the SSL encryption protocol. CRIME (Compr
From playlist OWASP AppSec EU 2013

Ruby Conf 2011 Better Than ROT13 by Bradley Grzesiak
We use encryption every day, from SSL to SSH to passing notes to your crush during Social Studies class. But how does it actually work? I'll avoid most of the math but cover the concepts of both symmetric and asymmetric encryption, including hashing and signing. I'll also show how to use O
From playlist Ruby Conference 2011

Affine Cipher - Decryption (Known Plaintext Attack)
In this video I talk about ways to decrypt the Affine Cipher when the key is NOT known. Specifically, I go over an example of the known plaintext attack. 3^(-1) = 9 (mod 26) math worked out (Euclidean Algorithm): 1. Forwards: 26 = 3(8) + 2 3 = 2(1) + 1 2. Backwords: 1 = 3 -
From playlist Cryptography and Coding Theory

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Toy Substitution Cipher 2 Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
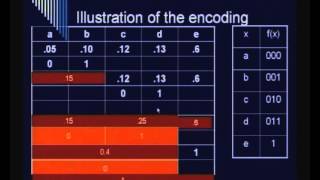
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

CERIAS Security: On the Evolution of Adversary Models for Security Protocols 2/6
Clip 2/6 Speaker: Virgil D. Gligor · University of Maryland Invariably, new technologies introduce new vulnerabilities which, in principle, enable new attacks by increasingly potent adversaries. Yet new systems are more adept at handling well-known attacks by old adversaries than anti
From playlist The CERIAS Security Seminars 2006

Tutorial: GeoHTTP Remote Buffer Overflow and DoS
A real example of a Buffer Overflow/Denial of Service attack! My favorite video: http://www.youtube.com/watch?v=z00kuZIVXlU Visit http://binslashshell.wordpress.com and join our forum community!!! This is a video showing what a Buffer Overflow Aattck can do to a Web Server. For th
From playlist Denial of Service attacks

Cryptography Lecture 2, Substitution Ciphers
From playlist Calculus I
