
Perfect Cipher - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Affine Cipher - Decryption (Known Plaintext Attack)
In this video I talk about ways to decrypt the Affine Cipher when the key is NOT known. Specifically, I go over an example of the known plaintext attack. 3^(-1) = 9 (mod 26) math worked out (Euclidean Algorithm): 1. Forwards: 26 = 3(8) + 2 3 = 2(1) + 1 2. Backwords: 1 = 3 -
From playlist Cryptography and Coding Theory

Convincing Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Perfect Cipher Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

What are common scams I should be aware of?
While online scams vary, many of them have certain features that help to identify them from legitimate online communications. Learn how to recognize and avoid some common types of scams.
From playlist Internet Safety

Most Common CyberSecurity Threats | CyberSecurity Attacks | CyberSecurity For Beginners |Simplilearn
This video from the cybersecurity domain will acquaint you with the Most Common Cybersecurity Threats faced in today's times. Cybersecurity holds paramount importance in safeguarding our digital data. This video will take you through cybersecurity attacks and how you can prevent them. 🔥Enr
From playlist Cyber Security Playlist [2023 Updated]🔥

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Modes of Operation of Block Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Weak Ciphers - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

DEFCON 20: Defeating PPTP VPNs and WPA2 Enterprise with MS-CHAPv2
Speakers: MOXIE MARLINSPIKE | DAVID HULTON | MARSH RAY MS-CHAPv2 is an authentication and key negotiation protocol that, while old and battered, is still unfortunately deployed quite widely. It underpins almost all PPTP VPN services, and is relied upon by many WPA2 Enterprise wireless dep
From playlist DEFCON 20

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
What is Cryptography? | Introduction to Cryptography | Cryptography for Beginners | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl Cryptography is essential to protect the information shared across the internet. This video on What is cryptography explaines you the fundamental concep
From playlist Cyber Security Training for Beginners | Edureka
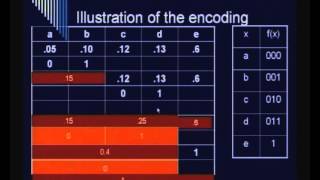
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Roberto La Scala, Università di Bari
Roberto La Scala, Università di Bari Ciphers and difference equations
From playlist Spring 2021 Online Kolchin Seminar in Differential Algebra

DDoS Attack Explained | What Is DDoS Attack? | Cyber Security Training | Simplilearn
This video on "What is a DDoS attack?" will help you understand all about a DDoS attack. Distributed Denial of Service (DDoS) attack is one of the most dangerous forms of cyberattacks. In this video, we will start with a few real-life scenarios of DDoS attacks and then learn about a DDoS a
From playlist Ethical Hacking Playlist [2023 Updated] 🔥


