How to sign a document in Microsoft Word
Doing this tutorial for a friend! He needed to know how to write his signature in a word document. Here is how you do it!
From playlist Microsoft Word Tutorials

Signature Validation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Can You Validate These Emails?
Email Validation is a procedure that verifies if an email address is deliverable and valid. Can you validate these emails?
From playlist Fun

From playlist Week 9 2014

Certificates - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Certificate Details - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Signature Validation - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

How to Create Signable PDF Documents (Tutorial)
Start sending free signable documents with Jotform: https://bit.ly/jotformsign Creating and sending signable documents is a must for any business. But isn't it complicated to make and manage these documents? Not with Jotform Sign! In this video, Scott Friesen shows you how easy it is to c
From playlist Productivity App Reviews for Entrepreneurs & Small Business

Signing Certificates - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

70-640 Certificate Services / 2008 R2 - Installing a Single Tier PKI (Detailed)
In this video we will demostrate all the details of how to install a single Tier Windows Server 2008 R2 Enterprise Root CA. This video is loaded with hints and tips to watch for durning the install. The perfect video for someone with a small company that want to setup a super simple PKI in
From playlist Cryptography, Security

Certificate Services: Stand-alone Certificate Authority
Certificate Services: Stand-alone Certificate Authority, CA
From playlist Cryptography, Security

OWASP AppSecUSA 2012: Reverse Engineering Secure HTTP API's With an SSL Proxy
Speakers: Alejandro Caceres and Mark Haase The proliferation of mobile devices has led to increased emphasis on native applications, such as Objective-C applications written for iOS or Java applications written for Android. Nonetheless, these native client applications frequently use HTTP
From playlist OWASP AppSecUSA 2012

Lec 22 | MIT 6.033 Computer System Engineering, Spring 2005
Authentication View the complete course at: http://ocw.mit.edu/6-033S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.033 Computer System Engineering, Spring 2005

DEFCON 17: More Tricks For Defeating SSL
Speaker: Moxie Marlinspike This talk aims to pick up where SSL stripping left off. While sslstrip ultimately remains quite deadly in practice, this talk will demonstrate some new tricks for defeating SSL/TLS in places where sslstrip does not reach. Cautious users, for example, have been a
From playlist DEFCON 17

DjangoCon US 2016 - SSL All The Things by Markus Holtermann
DjangoCon US 2016 - SSL All The Things by Markus Holtermann Over the last few years SSL/TLS encryption of not only websites but many other services as well has risen tremendously. The Let’s Encrypt organization and certificate authority (CA) makes that pretty easy. Since September 2015 al
From playlist DjangoCon US 2016

Lec 24 | MIT 6.033 Computer System Engineering, Spring 2005
Advanced Authentication View the complete course at: http://ocw.mit.edu/6-033S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.033 Computer System Engineering, Spring 2005

Puppet Tutorial | Puppet Tutorial For Beginners | Puppet Configuration Management Tool | Simplilearn
🔥DevOps Engineer Master Program (Discount Code: YTBE15): https://www.simplilearn.com/devops-engineer-masters-program-certification-training?utm_campaign=PuppetTutorial-3hQiFuc-5kc&utm_medium=DescriptionFF&utm_source=youtube 🔥Post Graduate Program In DevOps: https://www.simplilearn.com/pgp
From playlist DevOps Tools Tutorial Videos | Simplilearn🔥[2022 Updated]

Puppet Installation And Configuration In CentOS | Puppet Installation and Configuration |Simplilearn
This Puppet installation & configuration video will take you through the step by step process of Puppet installation on CentOS. Puppet is a configuration management tool. It ensures that all your systems are maintained at a consistent state. Puppet is also used as a deployment tool. It has
From playlist DevOps Tools Tutorial Videos | Simplilearn🔥[2022 Updated]

Certificates Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
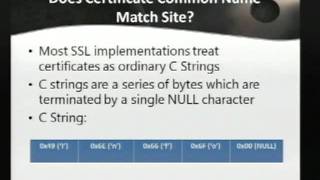
NOTACON 8: SSL Wars - The Dark Side of SSL
Speaker: Darth Vader The Rebel Alliance uses SSL to encrypt their transmissions so that the empire does not find the location of their secret base. In order to defeat the Rebel Alliances Darth Vader has studied SSL extensively to learn how it can be bypassed to listen to rebel transmissio
From playlist Notacon 8