
This video gives a general introduction to cryptography WITHOUT actually doing any math. Terms covered include cryptology vs cryptography vs cryptanalysis, symmetric vs public key systems, and "coding theory." NOTE: Yes, I said and wrote "cryptOanalysis" when it's actually "cryptanalysis
From playlist Cryptography and Coding Theory

Network Security, Part 2 : Public Key Encryption
Fundamental concepts of public key encryption are discussed. RSA encryption method explained with an example. Confidentiality of message is presented.
From playlist Cryptography, Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Few other Cryptanalytic Techniques
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Other Public Key Cryptosystems: Part 1
Fundamental concepts of Diffie-Hellman Key exchange are discussed. ElGamal Cryptosystem is presented. Elliptic curves are Analyzed.
From playlist Network Security

Public key cryptography - Diffie-Hellman Key Exchange (full version)
The history behind public key cryptography & the Diffie-Hellman key exchange algorithm. We also have a video on RSA here: https://www.youtube.com/watch?v=wXB-V_Keiu8
From playlist Cryptography, Security

25c3: Full-Disk-Encryption Crash-Course
Speaker: Juergen Pabel Everything to hide This is not a hacking presentation, no vulnerabilities are presented. It's a crash-course in full-disk-encryption ("FDE") concepts, products and implementation aspects. An overview of both commercial and open-source offerings for Windows, Linux,
From playlist 25C3: Nothing to hide

How To Create Identity Verification Smart Contract | Session 04 | #ethereum | #blockchain
Don’t forget to subscribe! In this project series, you will learn to create a smart contract for identity verification. This series will cover all the details necessary to teach you how to write a smart contract to verify the identity of a person or an object on the blockchain and ultima
From playlist Create Identity Verification Smart Contract

ESXiArgs Ransomware Analysis with @fwosar
Join us as we reverse engineer the ESXiArgs ransomware used in wide spread attacks targeting unpatched VMware servers with CVE-2021-21974. Fabian (https://twitter.com/fwosar) joins us to do the heavy lifting! Tutorial that may assist with decrypting files that have been encrypted by E
From playlist Open Analysis Live!

DEFCON 20: Weaponizing the Windows API with Metasploits Railgun
Speaker: DAVID €ŒTHELIGHTCOSINE€ MALONEY SOFTWARE ENGINEER, METASPLOIT RAPID7 No part of the Metasploit Framework has been shrouded in more mystery and confusion than the Railgun extension. Railgun is one of the most powerful tools in the Metasploit arsenal when it comes to Post Exploi
From playlist DEFCON 20

25c3: Chip Reverse Engineering
Speakers: Karsten Nohl, starbug Cryptographic algorithms are often kept secret in the false belief that this provides security. To find and analyze these algorithms, we reverse-engineering the silicon chips that implement them. With simple tools, we open the chips, take pictures, and ana
From playlist 25C3: Nothing to hide

OWASP AppSec EU 2013: Recipes for enabling HTTPS
For more information and to download the video visit: http://bit.ly/appseceu13 Playlist OWASP AppSec EU 2013: http://bit.ly/plappseceu13 Speakers: Nelis Boucké | Thomas Herlea | Johan Peeters Securely enabling HTTPS turns out to be tricky and time consuming. There is the considerable acc
From playlist OWASP AppSec EU 2013

Cryptography Tutorial For Beginners | Cybersecurity Training | Edureka | Cybersecurity Live - 2
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training This Edureka video on "Cryptography Tutorial" gives an introduction to the Cryptography and talks about its basic concepts. 🔴Subscribe to our channel to get video updates. Hit the subscribe butto
From playlist Edureka Live Classes 2020
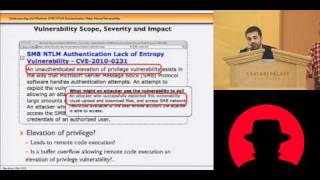
Black Hat USA 2010: Understanding the Windows SMB NTLM Weak Nonce Vulnerability 5/5
Speakers: Hernan Ochoa, Agustin Azubel In February 2010, we found a vulnerability in the SMB NTLM Windows Authentication mechanism that have been present in Windows systems for at least 14 years (from Windows NT 4 to Windows Server 2008). You probably haven't heard about this vulnerabilit
From playlist BH USA 2010 - OS WARS

Live CEOing Ep 403: Cryptography Review in Wolfram Language
In this episode of Live CEOing, Stephen Wolfram reviews upcoming functionality for cryptography features of the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Ste
From playlist Behind the Scenes in Real-Life Software Design

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Blockchain Interview Questions and Answers | Blockchain Technology | Blockchain Tutorial | Edureka
** Blockchain Training : https://www.edureka.co/blockchain-training ** This Edureka's Blockchain video consists of the frequently asked Blockchain Interview Questions which will help you in the preparation of Blockchain Interviews. Below are the topics covered in this session: 1. Blockcha
From playlist Blockchain Tutorial Videos | Edureka

