From playlist Trigonometry TikToks
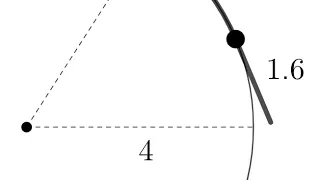
What is a radian? 🤔 Interactive dynamic radius wrapping exploration for Ss: https://www.geogebra.org/m/e3aamere #GeoGebra #MTBoS #ITeachMath #algebra #geometry #trigonometry #mathchat
From playlist Trigonometry: Dynamic Interactives!

Radon - Periodic Table of Videos
Here is a new video from us about Radon, including a look at a historic letter and a German cloud chamber! With thanks to the Royal Society and GSI. For those with annotations, the caption at the end for Radon should clearly be Rn, not Ra - sorry! More chemistry at http://www.periodicvi
From playlist Radioactive - Periodic Videos

stereolab - puncture in the radax permutation
check this out
From playlist the absolute best of stereolab

What is the Public Key Encryption?
A 1976, two Stanford researchers devised an encryption method that revolutionized cryptography by making it easier to send encrypted information without having to agree on a key beforehand. With the help of a short animation, cryptographer Tal Rabin explains how these "public" keys work.
From playlist Technology
In this video we will explore the difference between a radian and a degree and not only when to use each but how to convert between each other. ⭐️ Stop Memorizing the Unit Circle - https://www.youtube.com/watch?v=qW6Ua50fTw8 ✅ New Trigonometry Videos - https://youtube.com/playlist?list=P
From playlist Trigonometry in Pre-Calculus
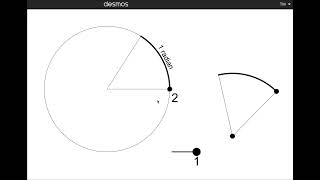
What Is a radian? Coffee ☕️ + Desmos 🙂 this AM = https://www.desmos.com/calculator/bcgjcpci3k. Also added to https://teacher.desmos.com/activitybuilder/custom/60742b18afd8ae0d274b6efb.
From playlist Desmos Activities, Illustrations, and How-To's

Radium - Periodic Table of Videos
Radium is a famous element - but also very dangerous. More links in description below ↓↓↓ Support Periodic Videos on Patreon: https://www.patreon.com/periodicvideos A video on every element: http://bit.ly/118elements More at http://www.periodicvideos.com/ Follow us on Facebook at http:/
From playlist With Portuguese subtitles (Português) - Periodic Videos
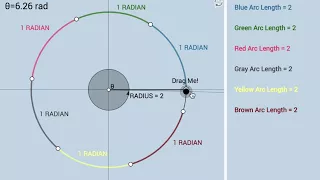
Radian Definition: Dynamic & Conceptual Illustrator
Link: https://www.geogebra.org/m/VYq5gSqU
From playlist Trigonometry: Dynamic Interactives!

"Fortunately, Unfortunately": How to Tell Whether a Number Is Prime #MegaFavNumbers
How can we tell whether or not a large integer is prime? Well, there's some bad news and some good news (and more bad news, and more good news, and...) My contribution to #MegaFavNumbers (and my first go at YouTube, so, you know, go easy on me). Matt Parker's video, which got me thinking
From playlist MegaFavNumbers

Faster Primality Test - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Asymmetric Cryptosystems - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Subscribe to our YouTube Channel for all the latest from World Science U. Visit our Website: http://www.worldscienceu.com/ Like us on Facebook: https://www.facebook.com/worldscienceu Follow us on Twitter: https://twitter.com/worldscienceu
From playlist Science Unplugged: Extra Dimensions
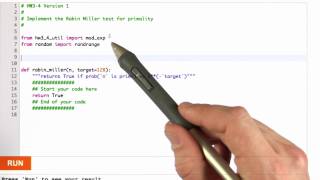
Rabin Miller Primality Test - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Keeping Secrets: Cryptography In A Connected World
Josh Zepps, Simon Singh, Orr Dunkelman, Tal Rabin, and Brian Snow discuss how, since the earliest days of communication, clever minds have devised methods for enciphering messages to shield them from prying eyes. Today, cryptography has moved beyond the realm of dilettantes and soldiers to
From playlist Explore the World Science Festival

Avi Wigderson & László Lovász - The Abel Prize interview 2021
00:30 Interview start 01:03 On the place of discrete math and theoretical computer science 08:14 Turing and Hilbert 14:28 P vs NP problem, what is it and why is it important? 25:09 Youth in Haifa, Avi Wigderson 30:09 Youth in Budapest, László Lovász 37:45 Problem solver or theory builde
From playlist László Lovász

One Way Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

26C3: Yes We Cant - on kleptography and cryptovirology 5/6
Clip 5/6 Speaker: Moti Yung In this talk I will survey some of the results (with Adam Young) on Cryptovirology (the art of employing public key cryptography maliciously as part of a malware attack, such as in ransomware) and the related Kleptography (the art of embedding cryptographic
From playlist 26C3: Here be dragons day 3

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Decomposing NOBEL GASSES! Decarboxylation of Acids with Xenon Difluoride! #Shorts
#Chemistry #Xenon #HydrogenFluoride #Shorts
From playlist Rad Chemistry Experiments