
Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

Symmetric Key Cryptography: The XOR Cipher
This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers the XOR logical operation, that is the exclusive OR operation, explaining how it can be used to encrypt and decrypt a sequence of binary digits. XOR is an im
From playlist Cryptography

From playlist Week 2 2015 Shorts

Cryptograph: Substitution Cipher (Caesar Cipher)
This lesson explains how to encrypt and decrypt a message using a Caeser cipher. Site: http://mathispower4u.com
From playlist Cryptography

Science & Technology Q&A for Kids (and others) [Part 8]
Stephen Wolfram hosts a live and unscripted Ask Me Anything about science and technology for all ages. Find the playlist of Q&A's here: https://wolfr.am/youtube-sw-qa Originally livestreamed at: https://twitch.tv/stephen_wolfram Follow us on our official social media channels. Twitter:
From playlist Stephen Wolfram Ask Me Anything About Science & Technology

28C3: Introducing Osmo-GMR (en)
For more information visit: http://bit.ly/28C3_information To download the video visit: http://bit.ly/28C3_videos Playlist 28C3: http://bit.ly/28C3_playlist Speaker: Sylvain Munaut Building a sniffer for the GMR satphones The latest member of the Osmocom-family projects, osmo-gm
From playlist 28C3: Behind Enemy Lines

Fundamental concepts of IPSec are discussed. Authentication Header is explained. Encapsulating Security Payload (ESP) and Internet Key Exchange (IKE) are analyzed.
From playlist Network Security

The Curse of Oak Island: UNBELIEVABLE Knights Templar Discovery (Season 10)
Is it possible that Rick and members of the team have found a carved symbol, less than 50 miles from Oak Island, that match one found in a church in Portugal known to have been constructed by members of the Knights Templar? See more in this scene from Season 10, Episode 11, "Oh, Well!" Wa
From playlist The Curse of Oak Island: Season 10 | History

Homology Smale-Barden manifolds with K-contact and Sasakian structures by Aleksy Tralle
Higgs bundles URL: http://www.icts.res.in/program/hb2016 DATES: Monday 21 Mar, 2016 - Friday 01 Apr, 2016 VENUE : Madhava Lecture Hall, ICTS Bangalore DESCRIPTION: Higgs bundles arise as solutions to noncompact analog of the Yang-Mills equation. Hitchin showed that irreducible solutio
From playlist Higgs Bundles

DEFCON 13: Mosquito - Secure Remote Code Execution Framework
Speakers: Wes Brown, Senior Security Consultant Scott Dunlop, Security Researcher Mosquito is a lightweight framework to deploy and run code remotely and securely in the context of penetration tests. It makes a best effort to ensure that the communications are secure. Special care is tak
From playlist DEFCON 13
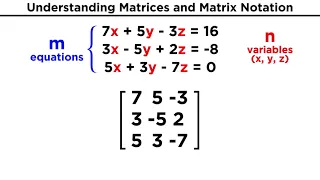
Understanding Matrices and Matrix Notation
In order to do linear algebra, we will have to know how to use matrices. So what's a matrix? It's just an array of numbers listed in a grid of particular dimensions that can represent the coefficients and constants from a system of linear equations. They're fun, I promise! Let's just start
From playlist Mathematics (All Of It)

Counting closed orbits of Anosov flows in free homotopy classes - Fenley
Geometric Structures on 3-manifolds Topic: Counting closed orbits of Anosov flows in free homotopy classes Speaker: Sergio Fenley A Date: Friday, March 18 This is joint work with Thomas Barthelme of Penn State University. There are Anosov and pseudo-Anosov flows so that some orbits are
From playlist Mathematics

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

ShmooCon 2014: Introducing idb - Simplified Blackbox iOS App Pentesting
For more information visit: http://bit.ly/shmooc14 To download the video visit: http://bit.ly/shmooc14_down Playlist Shmoocon 2014: http://bit.ly/shmooc14_pl Speaker: Daniel A. Mayer More than ever, mobile apps are used to manage and store sensitive data by both corporations and individu
From playlist ShmooCon 2014

Follow-up: Barbie electronic typewriter
Here is a copy of the description from the Barbie video: ---- I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett fr
From playlist My Maths Videos

Adam Savage vs The "Perpetual Motion" Machine!
Subscribe for more videos (and click the bell for notifications): http://www.youtube.com/subscription_center?add_user=testedcom Among the artifacts housed at The Royal Society is a curious device purporting to be a perpetual motion machine. The creation of the late British scientist and
From playlist Tested's 10 Most Popular Videos

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

