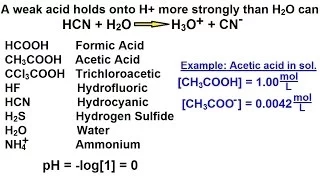
Chemistry - Acids & Bases Fundamentals (22 of 35) What Is A Weak Acid?
Visit http://ilectureonline.com for more math and science lectures! In this video I will explain "What is a weak acid?" (A "weak" acid is "strong".)
From playlist CHEMISTRY 22 ACIDS AND BASES

pH of .2 M of NH3 (weak base). More free lessons at: http://www.khanacademy.org/video?v=gDJtOIxDu78
From playlist Chemistry

IB Strong and Weak Acids and bases
IB SL Chemistry lesson on strong and weak acids and bases
From playlist IB Chemistry

When people close to us annoy us, and we wonder why we allowed them into our lives, we should draw vital comfort from a theory known as The Weakness of Strength. If you like our films take a look at our shop (we ship worldwide): http://www.theschooloflife.com/shop/all/ Brought to you by
From playlist SELF

The Weak Nuclear Force: Through the looking glass
Of all of the known subatomic forces, the weak force is in many ways unique. One particularly interesting facet is that the force differentiates between a particle that is rotating clockwise and counterclockwise. In this video, Fermilab’s Dr. Don Lincoln describes this unusual property a
From playlist Videos by Don Lincoln

Calculating the pH of a weak acid More free lessons at: http://www.khanacademy.org/video?v=dencuBNp_Ck
From playlist Chemistry
Open Source vs. Closed Source Software
In this video, you’ll learn more about the differences between open-source software and closed-source software. Visit https://edu.gcfglobal.org/en/basic-computer-skills/ for more technology, software, and computer tips. We hope you enjoy!
From playlist Technology Trends

All F chords are made from different permutations and combinations of the F,C and A notes
From playlist Music Lessons

27c3: News Key Recovery Attacks on RC4/WEP (en)
Speaker: Martin Vuagnoux In this paper, we present several weaknesses in the stream cipher RC4. First, we present a technique to automatically reveal linear correlations in the PRGA of RC4. With this method, 48 new exploitable correlations have been discovered. Then we bind these new b
From playlist 27C3: We come in peace

Foundations for Learning in the Age of Big Data IV - Maria Florina Balcan
2022 Program for Women and Mathematics: The Mathematics of Machine Learning Topic: Foundations for Learning in the Age of Big Data II Speaker: Maria Florina Balcan Affiliation: Carnegie Mellon University Date: May 24, 2022 Balcan-2022-05-27
From playlist Mathematics

Shiping Liu (7/29/22): Signed graphs and Nodal domain theorems for symmetric matrices
Abstract: A signed graph is a graph whose edges are labelled by a signature. It serves as a simple model of discrete vector bundle. We will discuss nodal domain theorems for arbitrary symmetric matrices by exploring the induced signed graph structure. This is an extension of the nodal doma
From playlist Applied Geometry for Data Sciences 2022

(IC 4.8) Optimality of Huffman codes (part 3) - sibling codes
We prove that Huffman codes are optimal. In part 3, we show that there exists a "sibling code". A playlist of these videos is available at: http://www.youtube.com/playlist?list=PLE125425EC837021F
From playlist Information theory and Coding

From playlist Sichere Email mit Dr. Christoph Meinel

28C3: Taking control over the Tor network (en)
For more information visit: http://bit.ly/28C3_information To download the video visit: http://bit.ly/28C3_videos Playlist 28C3: http://bit.ly/28C3_playlist Speakers: Eric Filiol, Seun Omosowon This talk deals with weaknesses identified in the TOR network protocol and cryptography
From playlist 28C3: Behind Enemy Lines

24C3: Mifare (Little Security, Despite Obscurity)
Speakers: Karsten Nohl, Henryk Plötz Mifare are the most widely deployed brand of secure RFID chips, but their security relies on proprietary and secret cryptographic primitives. We analyzed the hardware of the Mifare tags and found weaknesses in several parts of the cipher. For more i
From playlist 24C3: Full steam ahead

How to Prepare for HR Interview? | HR Interview Questions and Answers For Freshers | Simplilearn
🔥 Post Graduate Program In Full Stack Web Development: https://www.simplilearn.com/pgp-full-stack-web-development-certification-training-course?utm_campaign=DiscordBotPythonTutorial&utm_medium=Description&utm_source=youtube In this video on "How to prepare for HR Interview", you will lea
From playlist Interview Tips and Career Advice | Soft Skills Training 🔥[2022 Updated]

Particle Physics (8 of 41) The Weak Force
Visit http://ilectureonline.com for more math and science lectures! In this video I will explain the weak force. Next video in the Particle Physics series can be seen at: https://youtu.be/ZEhYj4dDuyw
From playlist PHYSICS 65 PARTICLE PHYSICS


