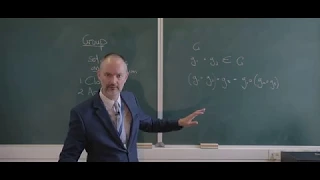
Definition of a group Lesson 24
In this video we take our first look at the definition of a group. It is basically a set of elements and the operation defined on them. If this set of elements and the operation defined on them obey the properties of closure and associativity, and if one of the elements is the identity el
From playlist Abstract algebra

Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security

Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security

Visual Group Theory, Lecture 1.4: Group presentations
Visual Group Theory, Lecture 1.4: Group presentations We begin this lecture by learning how to take a Cayley diagram and label its nodes with the elements of a group. Such a labeled diagram can function as a "group calculator". It leads to the notion of a "group presentation", which is a
From playlist Visual Group Theory

Visual Group Theory, Lecture 1.6: The formal definition of a group
Visual Group Theory, Lecture 1.6: The formal definition of a group At last, after five lectures of building up our intuition of groups and numerous examples, we are ready to present the formal definition of a group. We conclude by proving several basic properties that are not built into t
From playlist Visual Group Theory

What is a Group? | Abstract Algebra
Welcome to group theory! In today's lesson we'll be going over the definition of a group. We'll see the four group axioms in action with some examples, and some non-examples as well which violate the axioms and are thus not groups. In a fundamental way, groups are structures built from s
From playlist Abstract Algebra

Group Theory III Cayley Tables
Why are groups so popular? Well, in part it is because of their ability to characterise symmetries. This makes them a powerful tool in physics, where symmetry underlies our whole understanding of the fundamental forces. In the second video of this introduction to group theory, we check th
From playlist Group Theory

Now that we have defined and understand quotient groups, we need to look at product groups. In this video I define the product of two groups as well as the group operation, proving that it is indeed a group.
From playlist Abstract algebra

Symmetric Groups (Abstract Algebra)
Symmetric groups are some of the most essential types of finite groups. A symmetric group is the group of permutations on a set. The group of permutations on a set of n-elements is denoted S_n. Symmetric groups capture the history of abstract algebra, provide a wide range of examples in
From playlist Abstract Algebra
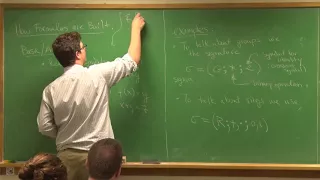
Fundamentals of Mathematics - Lecture 14: Signatures, Formulas, Structures, Theories, and Models
course page: http://www.uvm.edu/~tdupuy/logic/Math52-Fall2017.html videography - Eric Melton handouts - DZB, Emory
From playlist Fundamentals of Mathematics

Model Theory - part 01 - The Setup in Classical Set Valued Model Theory
Here we give the basic setup for Model Theory. I learned this from a talk Tom Scanlon gave in 2010 at CUNY.
From playlist Model Theory

Markus Banagl : The L-Homology fundamental class for singular spaces and the stratified Novikov
Abstract : An oriented manifold possesses an L-homology fundamental class which is an integral refinement of its Hirzebruch L-class and assembles to the symmetric signature. In joint work with Gerd Laures and James McClure, we give a construction of such an L-homology fundamental class for
From playlist Topology

DLP Attacks and intro to El Gamal
We cover basic attacks on the discrete logarithm problem. The El Gamal Cipher is presented. We start discussion digital signatures.
From playlist PubKey

DjangoCon US 2018 - Building Workflows With Celery by Josue Balandrano Coronel
Task Queues is a topic which most developers will eventually have to dive into, specially in today’s web development world. The idea is really simple: whenever one has any functionality which might take too long to perform, one can spawn a process which will take care of this functionality
From playlist DjangoCon US 2018

Mathematics in Cryptography II - Toni Bluher
2018 Program for Women and Mathematics Topic: Mathematics in Cryptography II Speaker: Toni Bluher Affiliation: National Security Agency Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Proper Actions and Representation Theory Part 2
Professor Toshiyuki Kobayashi, University of Tokyo, Japan
From playlist Distinguished Visitors Lecture Series

S. Filip - K3 surfaces and Dynamics (Part 1)
K3 surfaces provide a meeting ground for geometry (algebraic, differential), arithmetic, and dynamics. I hope to discuss: - Basic definitions and examples - Geometry (algebraic, differential, etc.) of complex surfaces - Torelli theorems for K3 surfaces - Dynamics on K3s (Cantat, McMullen)
From playlist Ecole d'été 2018 - Teichmüller dynamics, mapping class groups and applications

How does Schnorr Signature Work?
Describe the theoretical aspect of Schnorr digital signature.
From playlist crypto

Luca De Feo, Proving knowledge of isogenies, quaternions and signatures
VaNTAGe Seminar, November 15, 2022 License: CC-BY-NC-SA Links to some of the papers and cites mentioned in the talk: Couveignes (2006): https://eprint.iacr.org/2006/291 Fiat-Shamir (1986): https://doi.org/10.1007/3-540-47721-7_12 De Feo-Jao-Plût (2011): https://eprint.iacr.org/2011/506 B
From playlist New developments in isogeny-based cryptography
