26C3: How you can build an eavesdropper for a quantum cryptosystem 3/6
Clip 3/6 Speakers: Qin Liu ,Sebastien Sauge This presentation will show the first experimental implementation of an eavesdropper for quantum cryptosystem. Although quantum cryptography has been proven unconditionally secure, by exploiting physical imperfections (detector vulnerabilit
From playlist 26C3: Here be dragons day 1
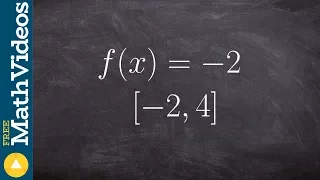
What is the max and min of a horizontal line on a closed interval
👉 Learn how to find the extreme values of a function using the extreme value theorem. The extreme values of a function are the points/intervals where the graph is decreasing, increasing, or has an inflection point. A theorem which guarantees the existence of the maximum and minimum points
From playlist Extreme Value Theorem of Functions

26C3: How you can build an eavesdropper for a quantum cryptosystem 2/6
Clip 2/6 Speakers: Qin Liu ,Sebastien Sauge This presentation will show the first experimental implementation of an eavesdropper for quantum cryptosystem. Although quantum cryptography has been proven unconditionally secure, by exploiting physical imperfections (detector vulnerabilit
From playlist 26C3: Here be dragons day 1

Extreme Value Statistics: Peak over Threshold methods
From playlist Extreme Value Statistics
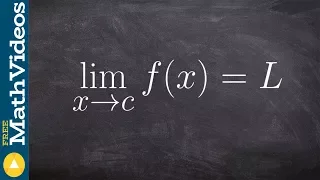
👉 Learn about the limit of a function. The limit of a function as the input variable of the function tends to a number/value is the number/value which the function approaches at that time. The limit of a function is said to exist if the value which the function approaches as x (or the inde
From playlist Learn about Limits
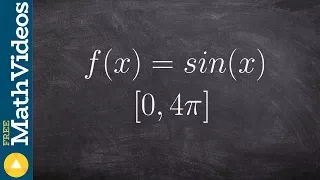
How to determine the max and min of a sine on a closed interval
👉 Learn how to find the extreme values of a function using the extreme value theorem. The extreme values of a function are the points/intervals where the graph is decreasing, increasing, or has an inflection point. A theorem which guarantees the existence of the maximum and minimum points
From playlist Extreme Value Theorem of Functions

Statistics - How to find outliers
This video covers how to find outliers in your data. Remember that an outlier is an extremely high, or extremely low value. We determine extreme by being 1.5 times the interquartile range above Q3 or below Q1. For more videos visit http://www.mysecretmathtutor.com
From playlist Statistics

In this video I briefly explain what minimum distance is and why it is helpful. Then I explain how to find it "the long way" and the "shortcut." Also during the process, I explain what Hamming Weight and Distance are and how to find them. Codewords from Generating Matrix Video: https://w
From playlist Cryptography and Coding Theory

R11. Cryptography: More Primitives
MIT 6.046J Design and Analysis of Algorithms, Spring 2015 View the complete course: http://ocw.mit.edu/6-046JS15 Instructor: Ling Ren In this recitation, problems related to cryptography are discussed. License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More c
From playlist MIT 6.046J Design and Analysis of Algorithms, Spring 2015

Maximum and Minimum Values (Closed interval method)
A review of techniques for finding local and absolute extremes, including an application of the closed interval method
From playlist 241Fall13Ex3

Chris Peikert - Post Quantum assumptions - IPAM at UCLA
Recorded 27 July 2022. Chris Peikert of the University of Michigan presents "Post Quantum assumptions" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Learn more online at: https://www.ipam.ucla.edu/programs/summer-schools/graduate-summer-school-on-post-quantum-and-
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Asymmetric Cryptosystems - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

One Way Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

26C3: Yes We Cant - on kleptography and cryptovirology 5/6
Clip 5/6 Speaker: Moti Yung In this talk I will survey some of the results (with Adam Young) on Cryptovirology (the art of employing public key cryptography maliciously as part of a malware attack, such as in ransomware) and the related Kleptography (the art of embedding cryptographic
From playlist 26C3: Here be dragons day 3

What Are Error Intervals? GCSE Maths Revision
What are error Intervals and how do we find them - that's the mission in this episode of GCSE Maths minis! Error Intervals appear on both foundation and higher tier GCSE maths and IGCSE maths exam papers, so this is excellent revision for everyone! DOWNLOAD THE QUESTIONS HERE: https://d
From playlist Error Intervals & Bounds GCSE Maths Revision

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography - Seminar 1 - Foundations
This seminar series is about the mathematical foundations of cryptography. In the first seminar Eleanor McMurtry introduces cryptography and explains some of the problems that need to be solved in order to develop proper foundations. The webpage for this seminar is https://lnor.net/uc-sem
From playlist Metauni

Modern Anomaly and Novelty Detection: Exercise - Session 15
iforest continued Tuning with respect to the data about prior knowledge of data ie. know % of outlier in data about threshold and decision boundaries - prediction match assumption overlapping cases one-SVM Hard vs soft boundaries Threshold hyperparameter
From playlist Modern Anomaly and Novelty Detection

Stanford Seminar - The Evolution of Public Key Cryptography
EE380: Computer Systems Colloquium Seminar The Evolution of Public Key Cryptography Speaker: Martin Hellman, Stanford EE (Emeritus) While public key cryptography is seen as revolutionary, after this talk you might wonder why it took Whit Diffie, Ralph Merkle and Hellman so long to discov
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series