
An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

One Time Pad - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Symmetric Key Cryptography: The XOR Cipher
This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers the XOR logical operation, that is the exclusive OR operation, explaining how it can be used to encrypt and decrypt a sequence of binary digits. XOR is an im
From playlist Cryptography

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

Perfect Cipher - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptograph: Substitution Cipher (Caesar Cipher)
This lesson explains how to encrypt and decrypt a message using a Caeser cipher. Site: http://mathispower4u.com
From playlist Cryptography

Using the inverse of an exponential equation to find the logarithm
👉 Learn how to convert an exponential equation to a logarithmic equation. This is very important to learn because it not only helps us explain the definition of a logarithm but how it is related to the exponential function. Knowing how to convert between the different forms will help us i
From playlist Logarithmic and Exponential Form | Learn About

Pseudorandom Number Generation and Stream Ciphers
Fundamental concepts of Pseudorandom Number Generation are discussed. Pseudorandom Number Generation using a Block Cipher is explained. Stream Cipher & RC4 are presented.
From playlist Network Security

Vigenere Cipher - Decryption (Known Key)
This video shows how to decrypt the ciphertext when the key is known. Decryption (unknown key): http://youtu.be/LaWp_Kq0cKs Encryption: http://youtu.be/izFivfLjD5E
From playlist Cryptography and Coding Theory
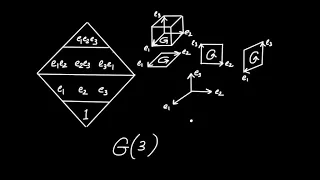
Geometric Algebra in 3D - Fundamentals
In this video, we set up the geometric algebra of three dimensions, called G(3). We will see that the introduction of a third basis vector adds two extra bivectors and a trivector to our basis for G(3) compared to G(2). We'll see that geometric interpretations and computations are analogou
From playlist Math
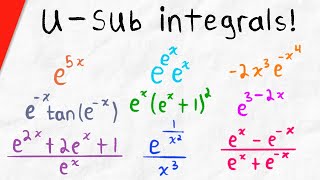
Integrating Exponential Functions with Substitution | Calculus 1 Exercises
We go over integrals of exponential functions (like e^2x) that require u-substitution (also called change of variable). We will also solve one integral simply requiring us to split up a fraction. Lots of exponential integral problems make for great practice! #apcalculus #calculus1 We int
From playlist Calculus 1 Exercises

Mod-01 Lec-36 Reaction Engineering Examples in Biochemical & Environmental Engineering
Advanced Chemical Reaction Engineering (PG) by Prof. H.S.Shankar,Department of Chemical Engineering,IIT Bombay.For more details on NPTEL visit http://nptel.ac.in
From playlist IIT Bombay: Advanced Chemical Reaction Engineering | CosmoLearning.org

How to Use Variation of Parameters to Solve y'' + 3y' + 2y = 1/(7 + e^x)
How to Use Variation of Parameters to Solve y'' + 3y' + 2y = 1/(7 + e^x) If you enjoyed this video please consider liking, sharing, and subscribing. You can also help support my channel by becoming a member https://www.youtube.com/channel/UCr7lmzIk63PZnBw3bezl-Mg/join Thank you:)
From playlist Zill DE 4.6 Variation of Parameters

Geometric Algebra in 3D - Bivector Addition
In this video, we will look at the algebraic and geometric interpretations of adding bivectors together in G(3). We will also show that all the bivectors in G(2) and G(3) can be factored as a wedging of two vectors, i.e. they are all 2-blades. This video has plenty of drawings and examples
From playlist Math

Derivatives of Exponential Functions
This calculus video tutorial explains how to find the derivative of exponential functions using a simple formula. It explains how to do so with the natural base e or with any other number. This video contains plenty of examples and practice problems including those using the product rule
From playlist New Calculus Video Playlist

E^pi and pi^e. Can you determine which quantity is bigger without using a calculator? In this video, I present some approaches to solving this problem. If you have a different approach, make sure to leave it in the comments below! Thanks for watching! Instagram: https://www.instagram.co
From playlist Proofs

Geometric Algebra - Duality and the Cross Product
In this video, we will introduce the concept of duality, involving a multiplication by the pseudoscalar. We will observe the geometric meaning of duality and also see that the cross product and wedge product are dual to one another, which means that the cross product is already contained w
From playlist Geometric Algebra

13 Year-Old Explaining the Simson Line #SoME
Hi! This is my first YouTube video and I sincerely hope that you enjoy watching it! The Simson line, as explained, is defined as follows- given a triangle ABC and a point P on its circumcircle, the three closest points to P on lines AB, AC, and BC are collinear. In this video, I'll be prov
From playlist Summer of Math Exposition Youtube Videos

Geometric Algebra in 2D - Fundamentals and Another Look at Complex Numbers
In this video, I introduce some of the concepts of geometric (Clifford) algebra, focusing on two-dimensional space (R^2). We'll talk about the wedge (exterior) product, review the dot product, and introduce the geometric product. We'll see that a new mathematical object, the bivector, aris
From playlist Math
