
Hamming Code For Error Detection And Correction | Hamming Code Error Correction | Simplilearn
In this video on "Hamming Code for Error Detection," we will look into the introductory knowledge related to the network technique of hamming code. This network will allow us to detect and correct errors on the receiver side. Explained in the stepwise format for proper clarification. Topi
From playlist Networking

Vigenere Cipher - Decryption (Known Key)
This video shows how to decrypt the ciphertext when the key is known. Decryption (unknown key): http://youtu.be/LaWp_Kq0cKs Encryption: http://youtu.be/izFivfLjD5E
From playlist Cryptography and Coding Theory

Symmetric Key Cryptography | Stream Cipher & Block Cipher Explained | Network Security | Simplilearn
This video on Symmetric Key Cryptography will acquaint you with the process of symmetric encryption and decryption. Here, we take a small recap into cryptography, the working and applications of symmetric key cryptography, and its advantages. We also have stream cipher and block cipher exp
From playlist Cyber Security Playlist [2023 Updated]🔥

5 Animals With Superpowers | What the Stuff?!
Some animals have superpowers seemingly straight out of a comic book! 10 Superhero Powers of the Animal Kingdom: http://animals.howstuffworks.com/animal-facts/10-animal-superpowers.htm Video Attribution: The Princess Bride Blu-ray CLIP - Have Fun Storming The Castle (2012) - Cary Elwes
From playlist Episodes hosted by Ben

This video is about the Vigenere Cipher: years used, key format, encryption. Note: sorry, I may have mispronounced names. Decryption (known key): http://youtu.be/oHcJ4QLiiP8 Decryption (unknown key): http://youtu.be/LaWp_Kq0cKs
From playlist Cryptography and Coding Theory

How to detect and correct an error using the Hamming Code. Hamming codes are a type of linear code, see link for intro to linear code: https://www.youtube.com/watch?v=oYONDEX2sh8 Questions? Feel free to post them in the comments and I'll do my best to answer!
From playlist Cryptography and Coding Theory

Time Travel in Science Fiction: A Brief History | James Gleick | Big Think
Time Travel in Science Fiction: A Brief History Watch the newest video from Big Think: https://bigth.ink/NewVideo Join Big Think Edge for exclusive videos: https://bigth.ink/Edge ---------------------------------------------------------------------------------- The idea of time travel, s
From playlist Best Videos | Big Think

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

RIPCORD Blockchains: distinguishing blockchain value from blockchain bullshit
RIPCORD is a way for you to remember the most important characteristics of the most important blockchains. Use the RIPCORD acronym and principles to more easily identify the blockchain projects that might represent real change and those that are just more of the status quo. 00:00 - What i
From playlist English Subtitles - aantonop Videos with subtitles in English

Modern Poetry (ENGL 310) with Langdon Hammer Hart Crane's masterwork The Bridge is positioned as a response to the modernist aesthetics of T.S. Eliot's The Waste Land. The visionary and specifically American aspects of the epic are stressed. Crane's interest in myth and symbol, his inclus
From playlist Modern Poetry with Langdon Hammer (ENGL 310)

UFOs and the Occult | The Story of George Hunt Williamson
UFOs and the occult may seem like strange bedfellows, but they share an overlap of believers and practitioners. Self-proclaimed spiritual medium and alien contactee George Hunt Williamson even formed a career—and a cult—out of it. Brace yourself; it's gonna be a weird ride. This video is
From playlist Science
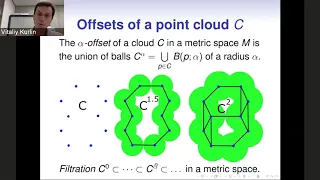
Vitaliy Kurlin (5/9/18): Skeletonization algorithms with theoretical guarantees for point clouds
We study the problem of approximating an unorganized cloud of points (in any Euclidean or metric space) by a 1-dimensional graph or a skeleton. The following recent algorithms provide theoretical guarantees for an output skeleton: the 1-dimensional Mapper, alpha-Reeb graphs and a Homologic
From playlist AATRN 2018

Stuff They Don't Want You to Know - Alien Abductions
Stories of alien abductions are found across the world. Yet according to mainstream science, there's no evidence to prove these outlandish claims. Tune in to learn more about the controversy surrounding stories of alien abductions. http://howstuffworks.com http://facebook.com/ConspiracySt
From playlist Stuff They Don't Want You To Know

Time travel is an ancient concept (it even occurs in the Hindu epic The Mahabharata) but could it really happen? Could a person physically travel through time? SUBSCRIBE | http://bit.ly/stdwytk-sub WEBSITE | http://bit.ly/stdwytk-home AUDIO PODCAST | http://bit.ly/stdwytk-audio-itun
From playlist Stuff They Don't Want You To Know, New Episodes!

Stories of alien abductions are found across the world. Yet according to mainstream science, there's no evidence to prove these outlandish claims. Tune in to learn more about the controversy surrounding stories of alien abductions. SUBSCRIBE | http://bit.ly/stdwytk-sub WEBSITE | http:
From playlist Stuff They Don't Want You To Know, New Episodes!

Beaches and scenic views of the island. The island has been "by-passed by the holiday-making throngs". A reel of the Greek island Thasos and visitable places. Thasos Island, Greece. Beaches and scenic views of the island. Narrator states that the island has been "by-passed by the holi
From playlist THE JET-SET TOURIST

Password Cracking With John The Ripper - RAR/ZIP & Linux Passwords
Hey guys! HackerSploit here back again with another video, in this video, we will be looking at Linux and encrypted password cracking with John the Ripper. John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, and OpenVMS. Its primary purpo
From playlist Ethical Hacking & Penetration Testing - Complete Course

Into the Depths | British Pathé
THE THINGS THAT SCARE US - MYSTERIES & HORROR MONTH ON BRITISH PATHÉ (OCTOBER 2015): Newsreels of the Week: Into the Depths. This week we head into some very spooky caves to look at the rock formations and the bats that live among them. We also explore an eerie underwater shipwreck and jo
From playlist Newsreels of the Week | British Pathé

Stereolab, "Vonal declosion". From the album "Margerine Eclipse" (2004). Ah c'est un travail que cet amour qui fait souffrir Qui frustre quand on n'arrive pas a s'ouvrir Le carcan le control semblent alors plus faciles Ne reservent pourtant que des temps difficiles. On le force on le cr
From playlist the absolute best of stereolab