
Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

From playlist Week 2 2015 Shorts

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

RailsConf 2019 - Modern Cryptography for the Absolute Beginner by Jeffrey Cohen
RailsConf 2019 - Modern Cryptography for the Absolute Beginner by Jeffrey Cohen _______________________________________________________________________________________________ Cloud 66 - Pain Free Rails Deployments Cloud 66 for Rails acts like your in-house DevOps team to build, deploy and
From playlist RailsConf 2019

Symmetric Key Cryptography: The XOR Cipher
This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers the XOR logical operation, that is the exclusive OR operation, explaining how it can be used to encrypt and decrypt a sequence of binary digits. XOR is an im
From playlist Cryptography

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Group Theory for Cryptology by Carlo Scoppola
PROGRAM GROUP ALGEBRAS, REPRESENTATIONS AND COMPUTATION ORGANIZERS: Gurmeet Kaur Bakshi, Manoj Kumar and Pooja Singla DATE: 14 October 2019 to 23 October 2019 VENUE: Ramanujan Lecture Hall, ICTS Bangalore Determining explicit algebraic structures of semisimple group algebras is a fund
From playlist Group Algebras, Representations And Computation

Modes of Operation of Block Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Privacy preserving identity verification using third party cloud services and FHE
Speaker - Dr Srinivas Vivek, Open Consent UK and Global Privacy Rights About the event This hybrid conference brought together prominent academics and key players in the field of digital identity from government and industry sectors. The event focused on the socio-technical infrastructu
From playlist Turing trustworthy digital identity international conference 2022

DevOpsDays Silicon Valley 2018 - Modern Security With Microservices And The Cloud by Seth Vargo
DevOpsDays Silicon Valley 2018 Modern Security With Microservices And The Cloud by Seth Vargo
From playlist DevOpsDays Silicon Valley 2018

Live CEOing Ep 253: Reviewing Entries in the Wolfram Function Repository
Watch Stephen Wolfram and teams of developers in a live, working, language design meeting. This episode is about Reviewing Entries in the Wolfram Function Repository.
From playlist Behind the Scenes in Real-Life Software Design

Block Ciphers and Data Encryption Standard (DES): Part 2
Fundamental concepts of Block Cipher Design Principles are discussed. Differential cryptanalysis and linear cryptanalysis are explained.
From playlist Network Security
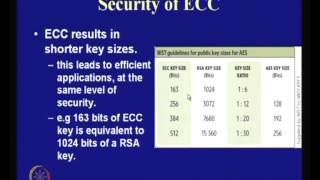
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Vigenere Cipher - Decryption (Known Key)
This video shows how to decrypt the ciphertext when the key is known. Decryption (unknown key): http://youtu.be/LaWp_Kq0cKs Encryption: http://youtu.be/izFivfLjD5E
From playlist Cryptography and Coding Theory

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

How the Lead Role in Strategic Intelligence Passed from Asia to the West
Christopher Andrew gave a series of three lectures in November on “The Lost History of Global Intelligence—and Why It Matters” for the Henry L. Stimson Lectures on World Affairs at the Whitney and Betty MacMillan Center for International and Area Studies at Yale. The lectures focused on th
From playlist The MacMillan Center

Theory and Practice of Cryptography
Google Tech Talks December, 12 2007 ABSTRACT Topics include: Introduction to Modern Cryptography, Using Cryptography in Practice, Proofs of Security and Security Definitions and A Special Topic in Cryptography Speaker: Steve Weis Steve Weis received his PhD from the Cryptography and In
From playlist Cryptography, Security

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security