
Transcendental Functions 3 Examples using Properties of Logarithms.mov
Examples using the properties of logarithms.
From playlist Transcendental Functions

Transcendental Functions 13 Derivatives of a Function and its Inverse.mov
The first derivative of a function and the inverse of that function.
From playlist Transcendental Functions

Transcendental Functions 19 The Function a to the power x.mp4
The function a to the power x.
From playlist Transcendental Functions

Multi-group fairness, loss minimization and indistinguishability - Parikshit Gopalan
Computer Science/Discrete Mathematics Seminar II Topic: Multi-group fairness, loss minimization and indistinguishability Speaker: Parikshit Gopalan Affiliation: VMware Research Date: April 12, 2022 Training a predictor to minimize a loss function fixed in advance is the dominant paradigm
From playlist Mathematics
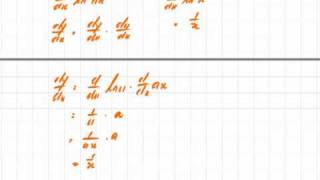
Transcendental Functions 16 Proof of the Properties of Logarithms Part 1.mov
Proof of some of the properties of logarithms.
From playlist Transcendental Functions

Transcendental Functions 16 Proof of the Properties of Logarithms Part 2.mov
Proof of the exponential or power property of logarithms.
From playlist Transcendental Functions
Giray Ökten: Number sequences for simulation - lecture 1
After an overview of some approaches to define random sequences, we will discuss pseudorandom sequences and low-discrepancy sequences. Applications to numerical integration, Koksma-Hlawka inequality, and Niederreiter’s uniform point sets will be discussed. We will then present randomized q
From playlist Probability and Statistics

Transcendental Functions 9 One More Property of Logarithms.mov
Another logarithmic property.
From playlist Transcendental Functions

Jonathan Katz - Introduction to Cryptography Part 1 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will serve as a "crash course" in modern cryptography for those with no prior exposure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Clip 4/6 Speaker: Travis Goodspeed Open JTAG with Voltage Glitching The GoodFET is an open source tool for programming microcontrollers and memories by SPI, I2C, JTAG, and a slew of vendor-proprietary protocols. In this lecture, the design of the GoodFET will be explained in detail,
From playlist 26C3: Here be dragons day 2

Pseudorandomness from Shrinkage - Raghu Meka
Raghu Meka Institute for Advanced Study May 8, 2012 One powerful theme in complexity theory and pseudorandomness in the past few decades has been the use of lower bounds to give pseudorandom generators (PRGs). However, the general results using this hardness vs. randomness paradigm suffer
From playlist Mathematics

Interview Igor Shparlinski : Jean Morlet Chair (First Semester 2014)
Jean-Morlet Chair on 'Number Theory and its Applications to Cryptography' Beneficiaries : Jean-Morlet Chair : Igor SHPARLINSKI School of Mathematics and Statistics University of New South Wales Sydney, Australia igor.shparlinski@unsw.edu.au Local project leader : David KOHEL I2M - Insti
From playlist Jean-Morlet Chair's holders - Interviews

Transcendental Functions 11 Inverse Functions Part 1.mov
Moving on in our study of transcendental functions, we look at the inverse of a function.
From playlist Transcendental Functions

Transcendental Functions 2 Properties of Logarithms.mov
Properties of Logarithms.
From playlist Transcendental Functions

Michal Pilipczuk: Introduction to parameterized algorithms, lecture II
The mini-course will provide a gentle introduction to the area of parameterized complexity, with a particular focus on methods connected to (integer) linear programming. We will start with basic techniques for the design of parameterized algorithms, such as branching, color coding, kerneli
From playlist Summer School on modern directions in discrete optimization

Katalin Gyarmati: On the cross-combined measure of families of binary lattices and sequences
Abstract: The cross-combined measure (which is a natural extension of crosscorrelation measure) is introduced and important constructions of large families of binary lattices with nearly optimal cross-combined measures are presented. These results are important in the study of large famili
From playlist Women at CIRM

Better Pseudorandom Generators from Milder Pseudorandom Restrictions - Parikshit Gopalan
Parikshit Gopalan Microsoft Research Silicon Valley, Mountain View, CA April 3, 2012 We present an iterative approach to constructing pseudorandom generators, based on the repeated application of mild pseudorandom restrictions. We use this template to construct pseudorandom generators for
From playlist Mathematics

Quantum Pseudoentanglement - Bill Fefferman
IAS It from Qubit Workshop Workshop on Spacetime and Quantum Information Topic: Quantum Pseudoentanglement Speaker: Bill Fefferman Affiliation: The University of Chicago Date: December 7, 2022 Wolfensohn Hall Quantum pseudorandom states are efficiently preparable states that are indistin
From playlist Natural Sciences

Transcendental Functions 4 Two Main Logarithmic Bases.mov
Logarithms with base 10 and Euler's number or the natural logarithm.
From playlist Transcendental Functions
