
AQA A-Level Further Maths C10-01 Eigenvalues and Eigenvectors: Introduction
Navigate all of my videos at https://sites.google.com/site/tlmaths314/ Like my Facebook Page: https://www.facebook.com/TLMaths-1943955188961592/ to keep updated Follow me on Instagram here: https://www.instagram.com/tlmaths/ Many, MANY thanks to Dean @deanencoded for designing my openin
From playlist AQA A-Level Further Maths C10: Eigenvalues and Eigenvectors
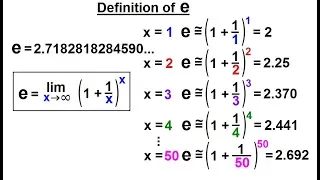
Calculus 1: Ch 5.1 Derivative of e^x and lnx (5 of 24) What is the number e ?
Visit http://ilectureonline.com for more math and science lectures! In this video I will explain the mathematical definition of e=2.7182818284590... The definition is e=lim(x approaches infinity)[1+(1/x)] raised to the power of x. When x=1 e~2, x=2 e~2.25, x=3 e~2.370, x=4 e~2.441, x=5 e`
From playlist CALCULUS 1 CH 5.1 DERIVATIVES e^x AND ln x

A11 Eigenvalues with complex numbers
Eigenvalues which contain complex numbers.
From playlist A Second Course in Differential Equations

Hash Collision Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

The method of determining eigenvalues as part of calculating the sets of solutions to a linear system of ordinary first-order differential equations.
From playlist A Second Course in Differential Equations

70-680 : Windows 7 cipher.exe and EFS
More videos like tis online at http://www.theurbanpenguin.com In this video we explore the strength of using the command line when using the Encrypted File system, EFS, in Windows 7. As Microsoft encourages technicians to be familiar with the command line tools this may become a topic in y
From playlist 70-680
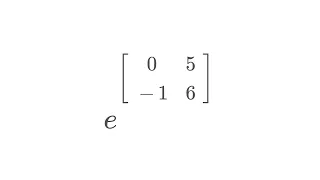
Calculating e^A for a matrix A, explaining what this has to do with diagonalization, and solving systems of differential equations Check out my Eigenvalues playlist: https://www.youtube.com/watch?v=H-NxPABQlxI&list=PLJb1qAQIrmmC72x-amTHgG-H_5S19jOSf Subscribe to my channel: https://www.y
From playlist Eigenvalues

Roberto La Scala, Università di Bari
Roberto La Scala, Università di Bari Ciphers and difference equations
From playlist Spring 2021 Online Kolchin Seminar in Differential Algebra

25c3: An introduction to new stream cipher designs
Speaker: Tor E. Bjørstad Turning data into line noise and back Even with "nothing to hide", we want to protect the privacy of our bits and bytes. Encryption is an important tool for this, and stream ciphers are a major class of symmetric-key encryption schemes. Algorithms such as RC4 (us
From playlist 25C3: Nothing to hide

Changing notation with complex eigenvalues.
From playlist A Second Course in Differential Equations

Yes, You Too Can Break Crypto: Exploiting Common Crypto Mistakes
Cryptography is tricky. Sure, everybody knows not to roll out their own crypto, but is it enough? Are the standard algorithms, libraries, and utilities always used the right way? This is of course a rhetorical question! Humans keep making mistakes that other humans can exploit, and Murphy’
From playlist Security

What is the number "e" and where does it come from?
e (2.718281828...), also known as Euler's number, is a critically important number in mathematics. It forms the basis of the exponential function and the natural logarithm, and like π it crops up in innumerable places (even where you wouldn't expect it).
From playlist Logarithms and Exponentials

Cryptography I Intro to Stream Ciphers
From playlist Crypto1

Cryptography I Intro to Stream Ciphers
From playlist Crypto1

Chole Martindale, Torsion point attacks on the SIDH key exchange protocol
VaNTAGe Seminar, November 8, 2022 License: CC-BY-NC-SA Links to papers mentioned in the video: Jao-De Feo-Plut (2011): https://eprint.iacr.org/2011/506.pdf Galbraith-Petit-Shani-Ti (2016): https://eprint.iacr.org/2016/859 Petit (2017): https://eprint.iacr.org/2017/571 dQKLMPPS (2020): h
From playlist New developments in isogeny-based cryptography

17. Two State Systems (continued)
MIT 8.05 Quantum Physics II, Fall 2013 View the complete course: http://ocw.mit.edu/8-05F13 Instructor: Barton Zwiebach In this lecture, the professor talked about the ammonia molecule as a two-state system, ammonia molecule in an electric field, nuclear magnetic resonance, etc. License:
From playlist 8.05 Quantum Physics II - Prof. Barton Zwiebach

Long COVID and Post-infection Syndromes: What We Know So Far
Head to https://linode.com/scishow to get a $100 60-day credit on a new Linode account. Linode offers simple, affordable, and accessible Linux cloud solutions and services. The list of symptoms for “Long COVID” are even more vast than the opinions about the right name for the condition. B
From playlist COVID-19 News & Updates

Zhaoting Wei: Determinant line bundles and cohesive modules
Talk by Zhaoting Wei in Global Noncommutative Geometry Seminar (Americas) https://www.math.wustl.edu/~xtang/NCG-Seminar on December 16, 2020
From playlist Global Noncommutative Geometry Seminar (Americas)

Calculus 1: Ch 5.1 Derivative of e^x and lnx (4 of 24) Infinite Series Expansion of e^x
Visit http://ilectureonline.com for more math and science lectures! In this video I will explain how mathematicians approximated the constant e=2.7182818284590... They used the infinite series of e^x=1+(x/1!)+(x^2/2!)+(x^3/3!)+(x^4/4!)+..., and when they let x=1 then they will get e^1=e=1
From playlist CALCULUS 1 CH 5.1 DERIVATIVES e^x AND ln x
