
Steganography Tutorial - Hide Messages In Images
Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step further by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it
From playlist Ethical Hacking & Penetration Testing - Complete Course

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Introduction - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

PMP® Change Management Process | PMP® Training Videos | Project Management Tutorial | Simplilearn
🔥 Post Graduate Program In Project Management: https://www.simplilearn.com/pgp-project-management-certification-training-course?utm_campaign=PMPChangeManagementProcess-rgfrFmphyig&utm_medium=DescriptionFF&utm_source=youtube 🔥 PMP® Certification Training Course: https://www.simplilearn.com/
From playlist Simplilearn Live

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

🔥Start a Cybersecurity Career in Six Months With IIIT Bangalore | Cybersecurity 2022 | Simplilearn
🔥Explore the CyberSecurity Career in Six Months With IIT Bangalore in Collaboration with Simplilearn: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=CyberSecurityWebinar16Nov22&utm_medium=DescriptionFirstFold&utm_source=youtube Start a Cybersecur
From playlist Simplilearn Live

Source Boston 2010: ZigBee Hacking and the Kinetic World 5/6
Clip 5/6 Speaker: Josh Wright. InGuardians, Inc. ZigBee has been established as a low-power wireless protocol, boasting features that make it attractive for smart grid technology. Combined with the Smart Energy Profile, ZigBee is quickly becoming a staple technology in the home area netwo
From playlist SOURCE Boston 2010
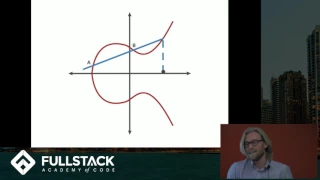
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Learn more advanced front-end and full-stack development at: https://www.fullstackacademy.com Elliptic Curve Cryptography (ECC) is a type of public key cryptography that relies on the math of both elliptic curves as well as number theory. This technique can be used to create smaller, fast
From playlist Elliptic Curves - Number Theory and Applications

Symmetric Cryptosystems - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Source Boston 2010: ZigBee Hacking and the Kinetic World 1/6
Clip 1/6 Speaker: Josh Wright. InGuardians, Inc. ZigBee has been established as a low-power wireless protocol, boasting features that make it attractive for smart grid technology. Combined with the Smart Energy Profile, ZigBee is quickly becoming a staple technology in the home area netwo
From playlist SOURCE Boston 2010

Source Boston 2010: Wifi Security 1/5
Clip 1/5 Speaker: Mike Kershaw For more information and presentation slides click here: http://bit.ly/8XJ1tm
From playlist SOURCE Boston 2010

Totient - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

Cryptography Course 🔥FREE | Cryptography Lecture | Cryptography Course Online Free | Simplilearn
🔥Enroll for Cryptography Course & Get Your Completion Certificate: https://www.simplilearn.com/learn-cryptography-basics-free-skillup-course?utm_campaign=CryptographySkillupIntro&utm_medium=Description&utm_source=youtube ✅Subscribe to our Channel to learn more about the top Technologies:
From playlist Cyber Security Playlist [2023 Updated]🔥

Symmetric Key Cryptography And Asymmetric Key Cryptography | Cryptography Tutorial | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=SymmetricKeyCryptographyAndAsymmetricKeyCryptography&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.sim
From playlist Cyber Security Playlist [2023 Updated]🔥

Symmetric Key Cryptography | Stream Cipher & Block Cipher Explained | Network Security | Simplilearn
This video on Symmetric Key Cryptography will acquaint you with the process of symmetric encryption and decryption. Here, we take a small recap into cryptography, the working and applications of symmetric key cryptography, and its advantages. We also have stream cipher and block cipher exp
From playlist Cyber Security Playlist [2023 Updated]🔥

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Asymmetric Key Cryptography | RSA Encryption Algorithm | Asymmetric Encryption | Simplilearn
In this video on Asymmetric Key Cryptography, we learn the ins & outs of asymmetric encryption and decryption. From learning the importance of asymmetric encryption to its applications, advantages and workflow, we cover all the bases and also take a look at why it's called public key crypt
From playlist Cyber Security Playlist [2023 Updated]🔥

