
Authentication, Authorization, Accounting (AAA) - Part 2
Fundamental concepts of authentication protocols are discussed. Radius server is presented. Extensible Authentication protocol is explained.
From playlist Network Security

Reliability 1: External reliability and rater reliability and agreement
In this video, I discuss external reliability, inter- and intra-rater reliability, and rater agreement.
From playlist Reliability analysis

Authentication, Authorization, Accounting, (AAA) - Part 1
Fundamental concepts of authentication protocols are discussed. Radius server is presented. Extensible Authentication protocol is explained.
From playlist Network Security

TLS Record Protocol - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Fundamental concepts of IPSec are discussed. Authentication Header is explained. Encapsulating Security Payload (ESP) and Internet Key Exchange (IKE) are analyzed.
From playlist Network Security

Fundamental concepts of IPSec are discussed. Authentication Header is explained. ESP & IKE are analyzed.
From playlist Network Security

Transport Layer Security Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Digital Trace Data Introduction
Dr. Ridhi Kashyap, Associate Professor of Social Demography at the University of Oxford, talks about how the digital revolution is creating new kinds of data — specifically digital trace data — and how social scientists can use this to ask interesting social science questions.
From playlist SICSS 2022
Marcello Delitala: Combination therapies and drug resistance in heterogeneous tumoral populations
Abstract: How combination therapies can reduce the emergence of cancer resistance? Can we exploit intra-tumoral competition to modify the effectiveness of anti-cancer treatments? Bearing these questions in mind, we present a mathematical model of cancer-immune competition under therapies.
From playlist Mathematics in Science & Technology

IMT4889: Contact tracing options
IMT4889: Mobile Research lecture In this lecture we have explored options for COVID-19 contact tracing.
From playlist Archive - Research in Mobile/Wearable Tech

A variational approach to closure of nonlinear dynamical systems - Liu - Workshop 1 - CEB T3 2019
Liu (Virginia Tech) / 09.10.2019A variational approach to closure of nonlinear dynamical systems In this talk, we discuss the closure problem of nonlinear evolution systems, with a focus on systems subject to autonomous forcings and placed in parameter regimes for which no slaving p
From playlist 2019 - T3 - The Mathematics of Climate and the Environment

CERIAS Security: Policy Engineering Framework for Federated Access Management 5/6
Clip 5/6 Speaker: Rafae Bhatti · Purdue University Federated systems are an emerging paradigm for information sharing and integration. Such systems require access management policies that not only protect user privacy and resource security but also allow scalable and seamless interope
From playlist The CERIAS Security Seminars 2006

Towards ambient intelligence in AI-assisted healthcare spaces - Dr Fei-Fei Li, Stanford University
Abstract: Artificial intelligence has begun to impact healthcare in areas including electronic health records, medical images, and genomics. But one aspect of healthcare that has been largely left behind thus far is the physical environments in which healthcare delivery takes place: hospit
From playlist Turing Seminars
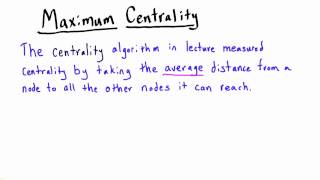
Centrality - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

CERIAS Security: Policy Engineering Framework for Federated Access Management 1/6
Clip 1/6 Speaker: Rafae Bhatti · Purdue University Federated systems are an emerging paradigm for information sharing and integration. Such systems require access management policies that not only protect user privacy and resource security but also allow scalable and seamless interope
From playlist The CERIAS Security Seminars 2006

Free CISSP Training Video | CISSP Tutorial Online Part 2
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=CCSPTrainingVideo-XghDe7VlVxo&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecur
From playlist CISSP Training Videos [2022 Updated]

CERIAS Security: Policy Engineering Framework for Federated Access Management 4/6
Clip 4/6 Speaker: Rafae Bhatti · Purdue University Federated systems are an emerging paradigm for information sharing and integration. Such systems require access management policies that not only protect user privacy and resource security but also allow scalable and seamless interope
From playlist The CERIAS Security Seminars 2006

SSH Authentication - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

25c3: Algorithmic Music in a Box
Speaker: Wesen Doing music with microcontrollers Small devices like microcontrollers, coupled to a few buttons, knobs, encoders and LEDs, allow for a host of interesting and creative musical applications. Solder a few bits together, program a few lines, and you can build a deep device to
From playlist 25C3: Nothing to hide
