
Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

Network Security: Classical Encryption Techniques
Fundamental concepts of encryption techniques are discussed. Symmetric Cipher Model Substitution Techniques Transposition Techniques Product Ciphers Steganography
From playlist Network Security

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

Block Ciphers and Data Encryption Standard (DES): Part 2
Fundamental concepts of Block Cipher Design Principles are discussed. Differential cryptanalysis and linear cryptanalysis are explained.
From playlist Network Security

Perfect Cipher - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Pseudorandom Number Generation and Stream Ciphers
Fundamental concepts of Pseudorandom Number Generation are discussed. Pseudorandom Number Generation using a Block Cipher is explained. Stream Cipher & RC4 are presented.
From playlist Network Security

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

This video is about asymmetric key cryptography; an extremely important aspect of computer science and cyber security. It covers the fundamental principles of asymmetric key cryptography, including the use of a public encryption key and a private decryption key. It explains that this co
From playlist Cryptography

25c3: An introduction to new stream cipher designs
Speaker: Tor E. Bjørstad Turning data into line noise and back Even with "nothing to hide", we want to protect the privacy of our bits and bytes. Encryption is an important tool for this, and stream ciphers are a major class of symmetric-key encryption schemes. Algorithms such as RC4 (us
From playlist 25C3: Nothing to hide

OWASP AppSec USA 2010: State of SSL on the Internet: 2010 Survey Results and Conclusions 3/3
Speaker: Ivan Ristic, Qualys More information can be found on the OWASP website: http://bit.ly/hY4bqh Source: http://bit.ly/owasp_appsec_us_2010
From playlist OWASP AppSec USA 2010

Securing Your Site by Thomas Pomfret
Rails makes it very easy to rapidly develop web applications, but doesn't always make it so simple to deploy or secure them. This talk is going to focus on best practices to secure your rails application, learnt through multiple high profile projects and penetration tests. The talk will b
From playlist Rails Conf 2012
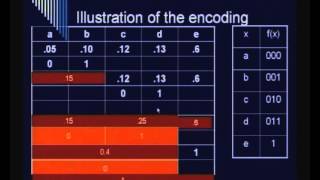
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

One Time Pad - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

OWASP AppSecUSA 2011: ESAPI 2.0 - Defense Against the Dark Arts
Speakers: Beef (Chris Schmidt), Kevin Wall In this presentation Chris, joined by Kevin Wall and other members of the ESAPI team will highlight the latest GA release of OWASP Enterprise Security API 2.0. Key touchpoints of the talk will include: What is ESAPI Integrating Controls Crypto E
From playlist OWASP AppSecUSA 2011

Correctness And Security - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Speakers: Henryk Plötz. Karsten Nohl Many RFID tags have weaknesses, but the security level of different tags varies widely. Using the Mifare Classic cards as an example, we illustrate the complexity of RFID systems and discuss different attack vectors. To empower further analysis of RFID
From playlist 25C3: Nothing to hide