
In this video on topics in emergency surgery for medical students and doctors, I discuss the common condition of biliary colic. Watch this video if your are preparing for the exams or are seeing a patient with biliary colic. Biliary colic is the most common form of gallstone disease, an
From playlist Let's talk Surgery

Rahul Savani: Polymatrix Games Algorithms and Applications
Polymatrix games are multi-player games that capture pairwise interactions between players. They are defined by an underlying interaction graph, where nodes represent players, and every edge corresponds to a two-player strategic form (bimatrix) game. This talk will be a short survey that w
From playlist HIM Lectures: Trimester Program "Combinatorial Optimization"

Biliary pancreatitis develops when a gallstone moves down the cystic and common bile ducts to obstruct the ampulla of Vater.
From playlist Let's talk Surgery

CERIAS Security: Role Discovery 5/5
Clip 5/5 Speaker: Bill Horne · HP Labs The first step in migrating to a role based access control (RBAC) system, is role development, in which teams of people meticulously define sets of roles that meet the needs of an organization's security and business requirements. Because it is s
From playlist The CERIAS Security Seminars 2007

CERIAS Security: Role Discovery 4/5
Clip 4/5 Speaker: Bill Horne · HP Labs The first step in migrating to a role based access control (RBAC) system, is role development, in which teams of people meticulously define sets of roles that meet the needs of an organization's security and business requirements. Because it is s
From playlist The CERIAS Security Seminars 2007

CERIAS Security: Role Discovery 3/5
Clip 3/5 Speaker: Bill Horne · HP Labs The first step in migrating to a role based access control (RBAC) system, is role development, in which teams of people meticulously define sets of roles that meet the needs of an organization's security and business requirements. Because it is s
From playlist The CERIAS Security Seminars 2007

CERIAS Security: Role Discovery 1/5
Clip 1/5 Speaker: Bill Horne · HP Labs The first step in migrating to a role based access control (RBAC) system, is role development, in which teams of people meticulously define sets of roles that meet the needs of an organization's security and business requirements. Because it is s
From playlist The CERIAS Security Seminars 2007

CERIAS Security: Role Discovery 2/5
Clip 2/5 Speaker: Bill Horne · HP Labs The first step in migrating to a role based access control (RBAC) system, is role development, in which teams of people meticulously define sets of roles that meet the needs of an organization's security and business requirements. Because it is s
From playlist The CERIAS Security Seminars 2007

Concave Quadrilateral Craziness! (GoGeometry Action 80)
Link: https://www.geogebra.org/m/T4axJRwY
From playlist Geometry: Challenge Problems

Electromagnetic induction and Antigravity!!!
Physics demonstrations (la physique)!!!
From playlist physics

This playlist is for patients and those interested in learning more about emergency surgical conditions and procedures. I am Dr Juan Klopper, a consultant surgeon at Groote Schuur Hospital and Head of Surgical Education at the University of Cape Town in South Africa. This video contains
From playlist Surgical information for patients

Old and New Results on the Spread of the Spectrum of a Graph - John C Urschel
The spread of a matrix is defined as the diameter of its spectrum. This quantity has been well-studied for general matrices and has recently grown in popularity for the specific case of the adjacency matrix of a graph. Most notably, Gregory, Herkowitz, and Kirkland proved a number of key r
From playlist Mathematics

"AWESOME Antigravity double cone" (science experiments)
Physics (la physique). Explain why double cone goes up on inclaned plane (science experiments)
From playlist MECHANICS
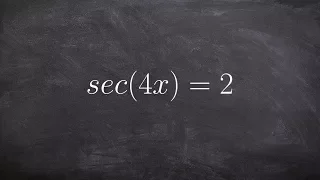
How to solve an equation with the multiple angle of secant
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric equations, they include by factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the given
From playlist Solve Trigonometric Equations with Multi Angles

DDOS Attack Explained | What Is DDOS Attack? | Cyber Security Training For Beginners | Simplilearn
This video on DDOS Attack Explained will help you understand what is DDoS attack and all about it. In this video, we will start with a few real-life scenarios of DDoS attacks and then learn about a DDoS attack in-depth. We will also look into the types of DDoS attacks and how you can preve
From playlist Cyber Security Playlist [2023 Updated]🔥

DDoS Attack Explained | What Is DDoS Attack? | Cyber Security Training | Simplilearn
This video on "What is a DDoS attack?" will help you understand all about a DDoS attack. Distributed Denial of Service (DDoS) attack is one of the most dangerous forms of cyberattacks. In this video, we will start with a few real-life scenarios of DDoS attacks and then learn about a DDoS a
From playlist Ethical Hacking Playlist [2023 Updated] 🔥

How To Create Game Combat System Like Final Fantasy | Session 16 | #unity | #gamedev
Don’t forget to subscribe! This project series will guide you on how to create a game combat system like Final Fantasy. Welcome to this series! We’ll be creating the combat system of the most popular FF Game! A game that was loved by millions and still loved to this day. And we are going
From playlist Create Game Combat System Like Final Fantasy

How To Create Game Combat System Like Final Fantasy | Session 11 | #unity | #gamedev
Don’t forget to subscribe! This project series will guide you on how to create a game combat system like Final Fantasy. Welcome to this series! We’ll be creating the combat system of the most popular FF Game! A game that was loved by millions and still loved to this day. And we are going
From playlist Create Game Combat System Like Final Fantasy

3 Squares Problem: Trigonometric Identity (Proof Without Words)
Link: https://www.geogebra.org/m/w8r7rn9Q
From playlist Trigonometry: Dynamic Interactives!
